Question: please use the code provided in the post and use python, please. Also, highlight the code and make sure everything in the rubric is fulfilled.
please use the code provided in the post and use python, please. Also, highlight the code and make sure everything in the rubric is fulfilled. Thank you!
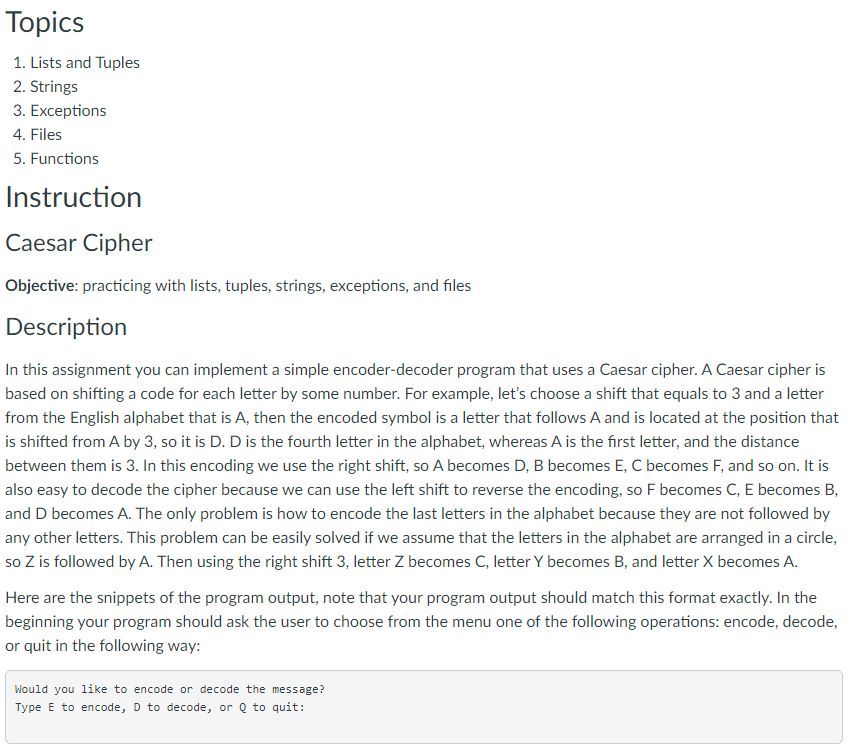
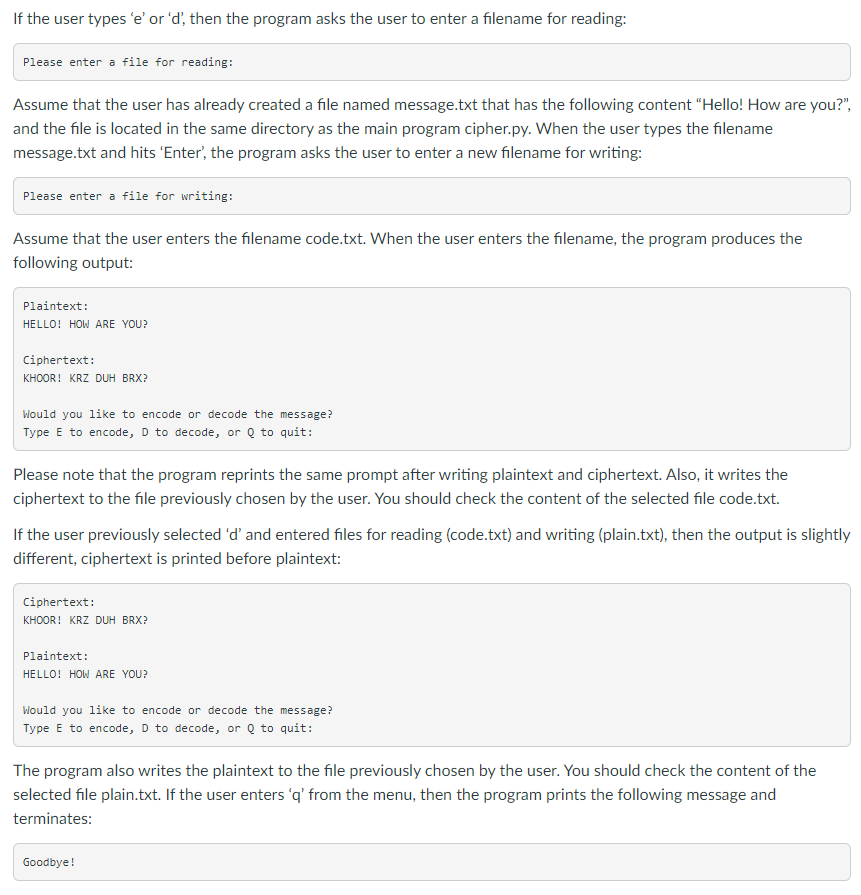
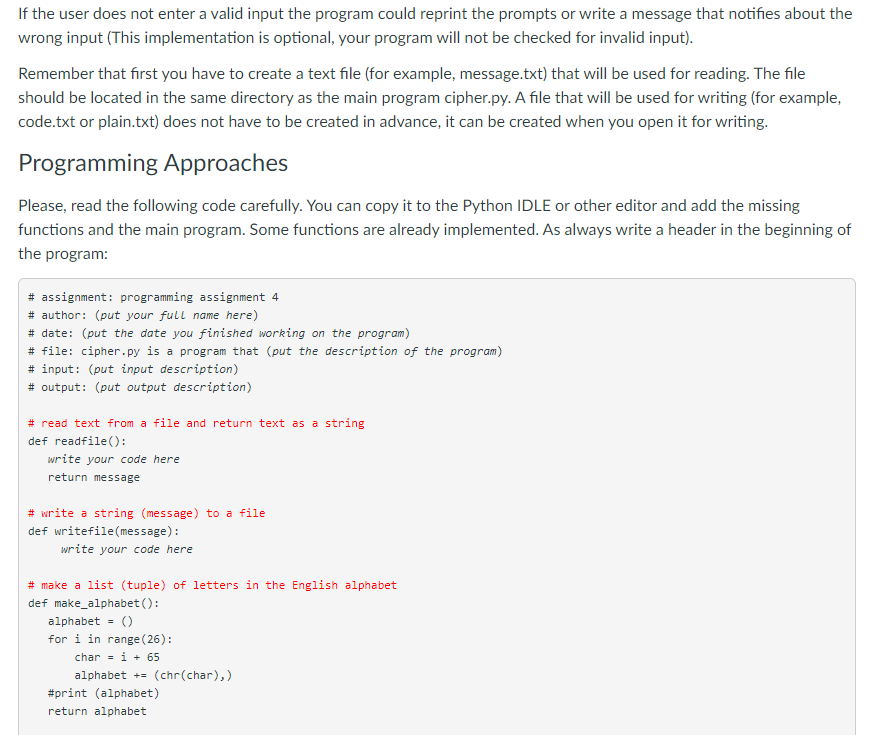
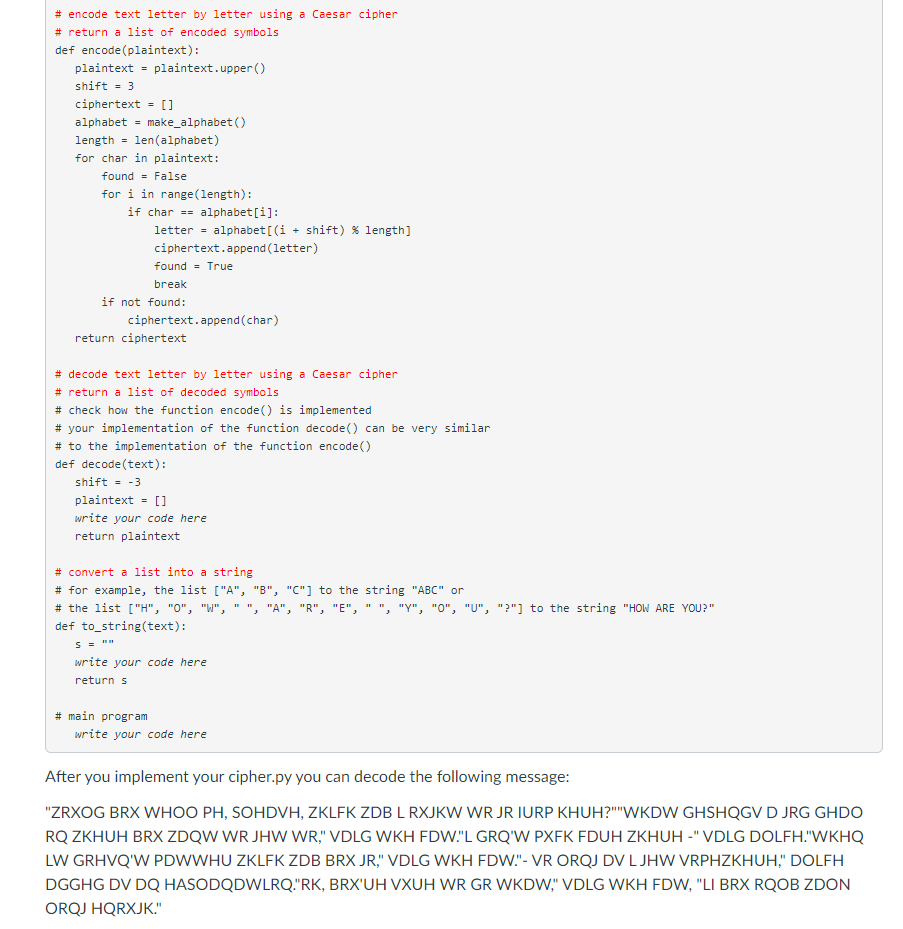
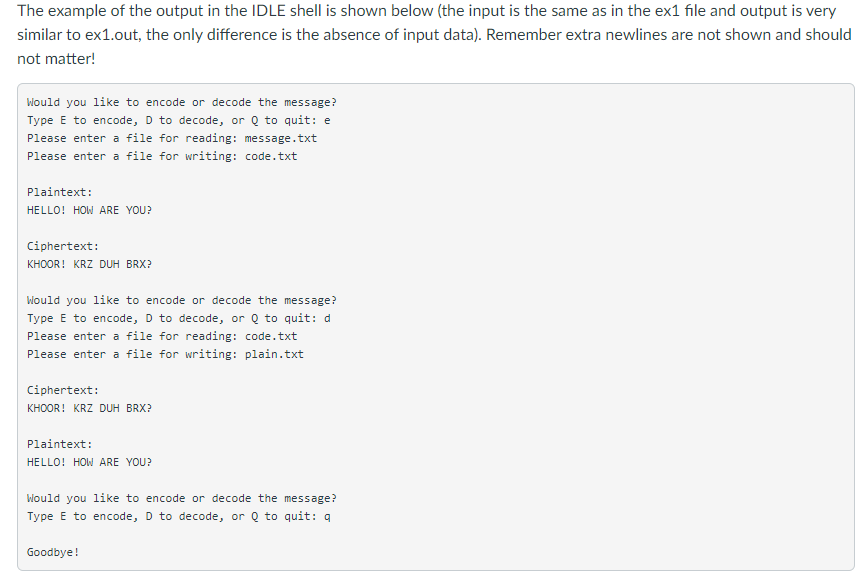
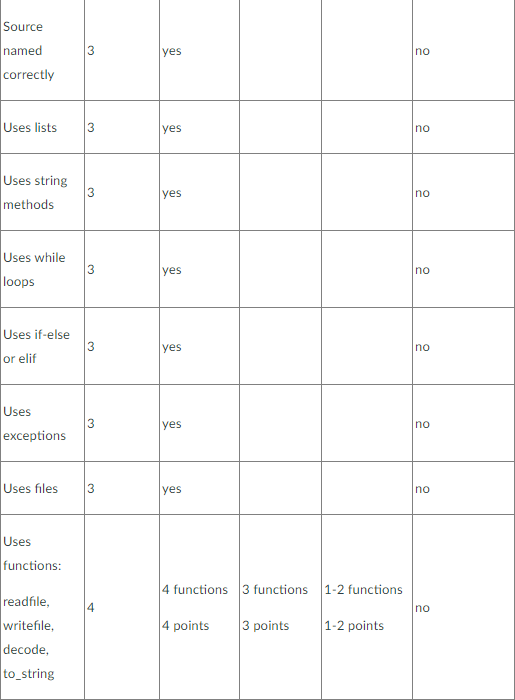
Topics 1. Lists and Tuples 2. Strings 3. Exceptions 4. Files 5. Functions Instruction Caesar Cipher Objective: practicing with lists, tuples, strings, exceptions, and files Description In this assignment you can implement a simple encoder-decoder program that uses a Caesar cipher. A Caesar cipher is based on shifting a code for each letter by some number. For example, let's choose a shift that equals to 3 and a letter from the English alphabet that is A, then the encoded symbol is a letter that follows A and is located at the position that is shifted from A by 3, so it is D. D is the fourth letter in the alphabet, whereas A is the first letter, and the distance between them is 3. In this encoding we use the right shift, so A becomes D, B becomes E, C becomes F, and so on. It is also easy to decode the cipher because we can use the left shift to reverse the encoding, so F becomes C, E becomes B, and D becomes A. The only problem is how to encode the last letters in the alphabet because they are not followed by any other letters. This problem can be easily solved if we assume that the letters in the alphabet are arranged in a circle, 50 Z is followed by A. Then using the right shift 3, letter Z becomes C, letter Y becomes B, and letter X becomes A. Here are the snippets of the program output, note that your program output should match this format exactly. In the beginning your program should ask the user to choose from the menu one of the following operations: encode, decode, or quit in the following way: Would you like to encode or decode the message? Type E to encode, D to decode, or Q to quit: If the user types 'e' or 'd', then the program asks the user to enter a filename for reading: Please enter a file for reading: Assume that the user has already created a file named message.txt that has the following content "Hello! How are you?", and the file is located in the same directory as the main program cipher.py. When the user types the filename message.txt and hits 'Enter', the program asks the user to enter a new filename for writing: Please enter a file for writing: Assume that the user enters the filename code.txt. When the user enters the filename, the program produces the following output: Plaintext: HELLO! HOW ARE YOU? Ciphertext: KHOOR! KRZ DUH BRX? Would you like to encode or decode the message? Type E to encode, D to decode, or Q to quit: Please note that the program reprints the same prompt after writing plaintext and ciphertext. Also, it writes the ciphertext to the file previously chosen by the user. You should check the content of the selected file code.txt. If the user previously selected d' and entered files for reading (code.txt) and writing (plain.txt), then the output is slightly different, ciphertext is printed before plaintext: Ciphertext: KHOOR! KRZ DUH BRX? Plaintext: HELLO! HOW ARE YOU? Would you like to encode or decode the message? Type E to encode, D to decode, or Q to quit: The program also writes the plaintext to the file previously chosen by the user. You should check the content of the selected file plain.txt. If the user enters 'q' from the menu, then the program prints the following message and terminates: Goodbye! If the user does not enter a valid input the program could reprint the prompts or write a message that notifies about the wrong input (This implementation is optional, your program will not be checked for invalid input). Remember that first you have to create a text file (for example, message.txt) that will be used for reading. The file should be located in the same directory as the main program cipher.py. A file that will be used for writing (for example, code.txt or plain.txt) does not have to be created in advance, it can be created when you open it for writing. Programming Approaches Please, read the following code carefully. You can copy it to the Python IDLE or other editor and add the missing functions and the main program. Some functions are already implemented. As always write a header in the beginning of the program: # assignment: programming assignment 4 # author: (put your full name here) # date: (put the date you finished working on the program) # file: cipher.py is a program that (put the description of the program) # input: (put input description) # output: (put output description) # read text from a file and return text as a string def readfile(): write your code here return message # write a string (message) to a file def writefile(message): write your code here # make a list (tuple) of letters in the English alphabet def make_alphabet(): alphabet for i in range (26): char = i + 65 alphabet += (chr(char), ) #print (alphabet) return alphabet # encode text letter by letter using a Caesar cipher # return a list of encoded symbols def encode(plaintext): plaintext = plaintext.upper() shift = 3 ciphertext [] alphabet = make_alphabet) length = len(alphabet) for char in plaintext: found = False for i in range(length): if char -- alphabet[i]: letter - alphabet[(i + shift) % length] ciphertext.append(letter) found = True break if not found: ciphertext.append(char) return ciphertext # decode text letter by letter using a Caesar cipher # return a list of decoded symbols # check how the function encode() is implemented # your implementation of the function decode() can be very similar # to the implementation of the function encode() def decode(text): shift = -3 plaintext - [] write your code here return plaintext # convert a list into a string # for example, the list ("A", "B", "C"] to the string "ABC" or # the list ("H", "0", "W", "A", "R", "E" "Y", "0", "U", "?"] to the string "HOW ARE YOU?" def to_string(text): S = 1 write your code here returns # main program write your code here After you implement your cipher.py you can decode the following message: "ZRXOG BRX WHOO PH, SOHDVH, ZKLFK ZDBL RXJKW WR JR IURP KHUH?""WKDW GHSHQGV D JRG GHDO RQ ZKHUH BRX ZDQW WR JHW WR" VDLG WKH FDW."L GRQ'W PXFK FDUH ZKHUH-" VDLG DOLFH."WKHQ LW GRHVQ'W PDWWHU ZKLFK ZDB BRX JR," VDLG WKH FDW."- VR ORQJ DV LJHW VRPHZKHUH," DOLFH DGGHG DV DO HASODQDWLRQ."RK, BRX'UH VXUH WR GR WKDW," VDLG WKH FDW, "LI BRX RQOB ZDON ORQJ HQRXJK." The example of the output in the IDLE shell is shown below (the input is the same as in the ex1 file and output is very similar to ex1.out, the only difference is the absence of input data). Remember extra newlines are not shown and should not matter! Would you like to encode or decode the message? Type E to encode, D to decode, or Q to quit: e Please enter a file for reading: message.txt Please enter a file for writing: code.txt Plaintext: HELLO! HOW ARE YOU? Ciphertext: KHOOR! KRZ DUH BRX? Would you like to encode or decode the message? Type E to encode, D to decode, or Q to quit: d Please enter a file for reading: code.txt Please enter a file for writing: plain.txt Ciphertext: KHOOR! KRZ DUH BRX? Plaintext: HELLO! HOW ARE YOU? Would you like to encode or decode the message? Type E to encode, D to decode, or Q to quit: a Goodbye! Source named correctly 3 yes no Uses lists 3 yes no Uses string methods 3 yes no Uses while loops 3 yes no Uses if-else or elif 3 yes no Uses exceptions yes no Uses files 3 yes no Uses functions: 4 functions 3 functions 1-2 functions no 4 points 3 points 1-2 points readfile, writefile, decode, to_string
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


