Answered step by step
Verified Expert Solution
Question
1 Approved Answer
pls help!! :) Malware is designed to damage or disable the system or data, disrupt or deny operation, gather information that leads to loss of
pls help!! :) 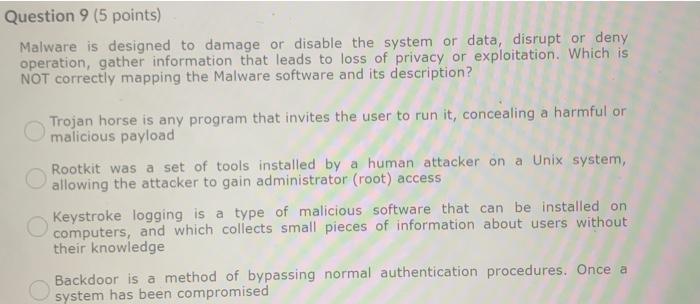
Malware is designed to damage or disable the system or data, disrupt or deny operation, gather information that leads to loss of privacy or exploitation. Which is NOT correctly mapping the Malware software and its description? Trojan horse is any program that invites the user to run it, concealing a harmful or malicious payload Rootkit was a set of tools installed by a human attacker on a Unix system, allowing the attacker to gain administrator (root) access Keystroke logging is a type of malicious software that can be installed on computers, and which collects small pieces of information about users without their knowledge Backdoor is a method of bypassing normal authentication procedures. Once a system has been compromised 
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


