Question: Programming Assignment Write a C program to simulate the behavior of the leaky bucket and token bucket algorithms. When the program is executed, the user
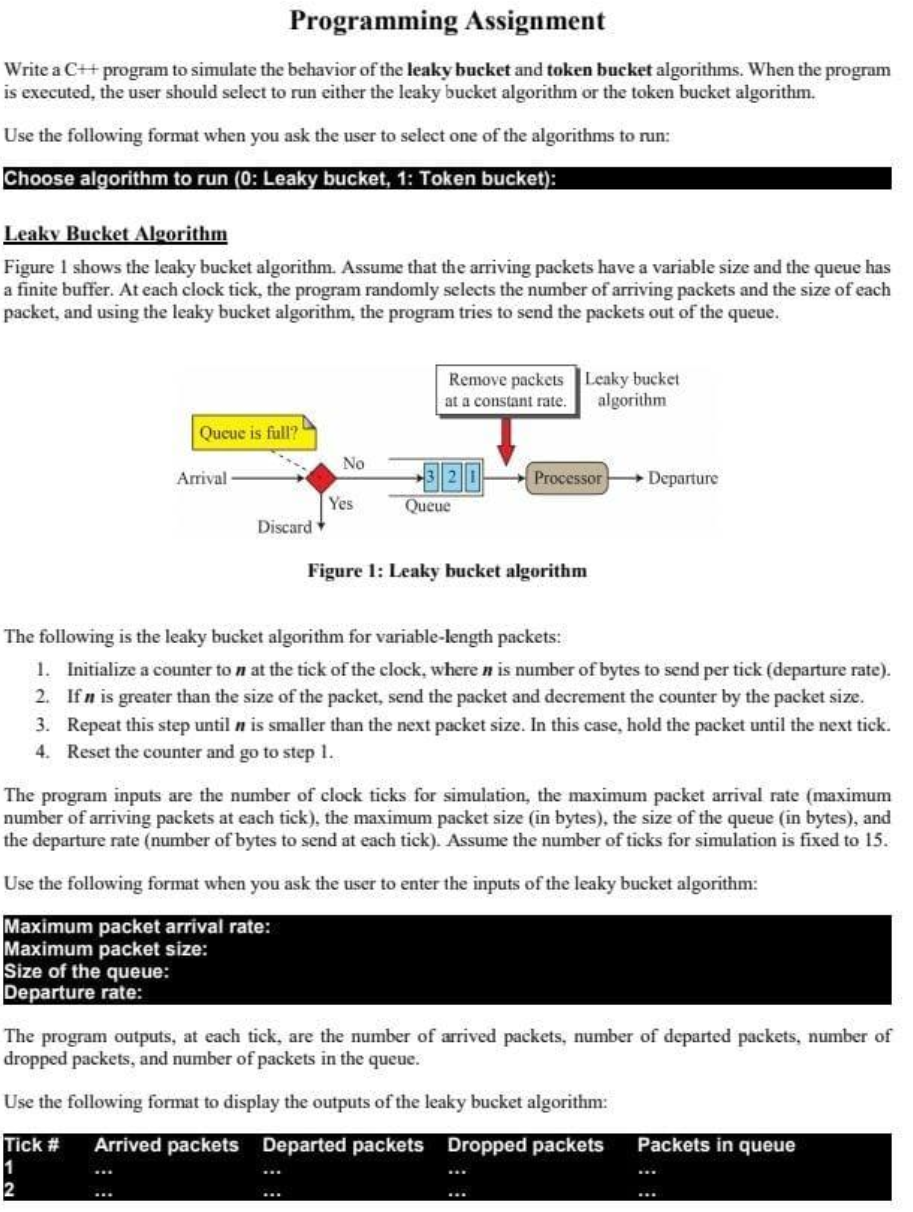
Programming Assignment Write a C program to simulate the behavior of the leaky bucket and token bucket algorithms. When the program is executed, the user should select to run either the leaky bucket algorithm or the token bucket algorithm. Use the following format when you ask the user to select one of the algorithms to run: Choose algorithm to run (0: Leaky bucket, 1: Token bucket): Leaky Bucket Algorithm Figure 1 shows the leaky bucket algorithm. Assume that the arriving packets have a variable size and the queue has a finite buffer. At each clock tick, the program randomly selects the number of arriving packets and the size of each packet, and using the leaky bucket algorithm, the program tries to send the packets out of the queue. Remove packets Leaky bucket at a constant rate. algorithm Qucue is full? No Arrival Processor Departure Yes Queue Discard Figure 1: Leaky bucket algorithm The following is the leaky bucket algorithm for variable-length packets: 1. Initialize a counter to n at the tick of the clock, where n is number of bytes to send per tick (departure rate). 2. Ifn is greater than the size of the packet, send the packet and decrement the counter by the packet size. 3. Repeat this step until n is smaller than the next packet size. In this case, hold the packet until the next tick. 4. Reset the counter and go to step 1. The program inputs are the number of clock ticks for simulation, the maximum packet arrival rate (maximum number of arriving packets at each tick), the maximum packet size (in bytes), the size of the queue (in bytes), and the departure rate (number of bytes to send at each tick). Assume the number of ticks for simulation is fixed to 15. Use the following format when you ask the user to enter the inputs of the leaky bucket algorithm: Maximum packet arrival rate: Maximum packet size: Size of the queue: Departure rate: The program outputs, at each tick, are the number of arrived packets, number of departed packets, number of dropped packets, and number of packets in the queue. Use the following format to display the outputs of the leaky bucket algorithm: Tick # Arrived packets Departed packets Dropped packets Packets in queue 2
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


