Question
Programming assignment - you may use C, C++, or Java Implement insertion, deletion and search for a hash table by using the double hashing method
Programming assignment - you may use C, C++, or Java
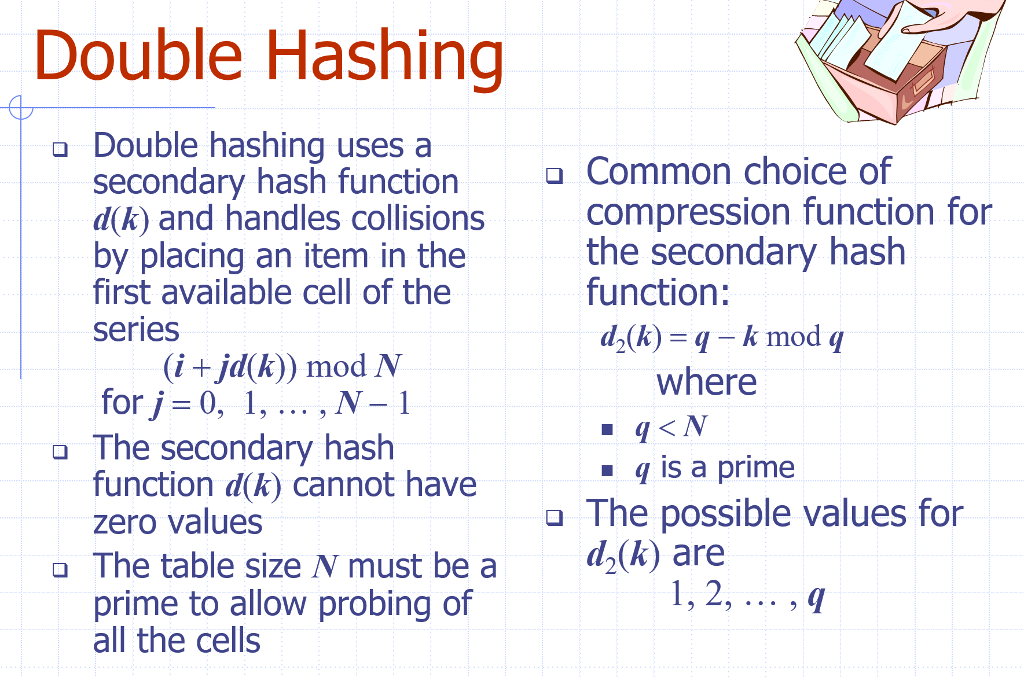
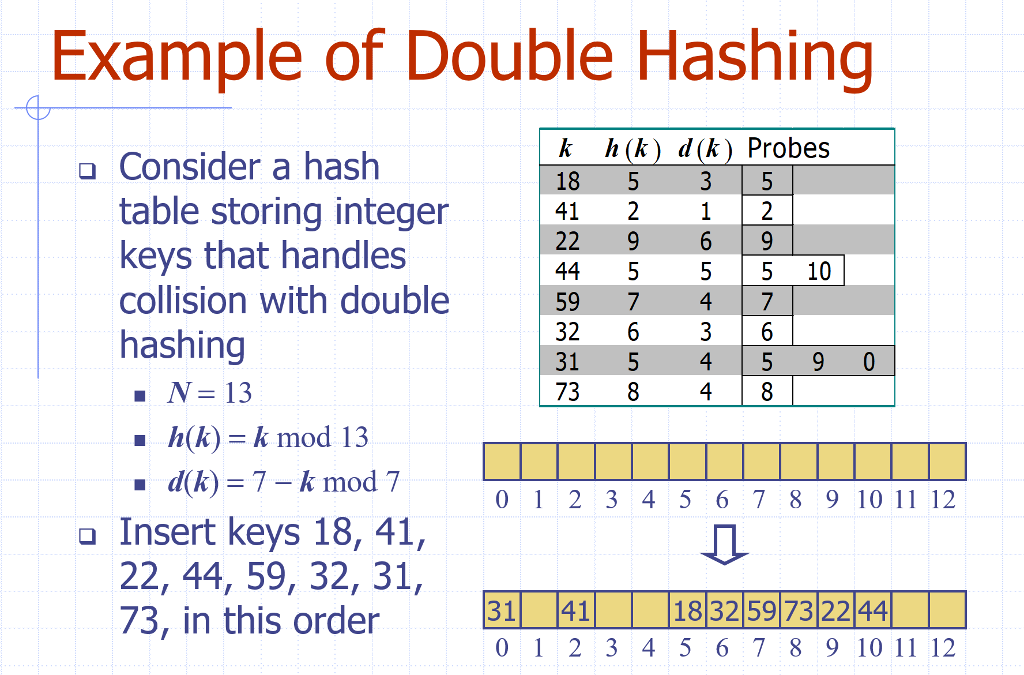
Implement insertion, deletion and search for a hash table by using the double hashing method as defined in class. Suppose your double hashing is h(k) = i + jd(k) mod N and d(k) = q k mod q, then pick q the largest prime less than N.
Input:
A sequence of integers to be randomly generated (file input)
Sample input format: 13 7 1.in 3.in 5.in 3.del 7.in 9.in 11.in 12.in 2.in 1.sch 15.in
The first and second integers are, N and q values, respectively.
Note that stop your input once the hash table is full.
Output:
Two sets of outputs to be displayed, one for before the operation, another for after the operation.
In each set of output, each entry to be displayed on a new line possibly with more than one key.
Note that output of a sch is to be found or not found.
If a duplicate is inserted display duplicate key.
Sample output format (in case of the chaining):
0:
1: 1
2: 2 15
3:
4:
5: 5
6:
7: 7
8:
9:
10:
11: 11
12: 12
Note that 2.in will output duplicate on the screen and 1.sch will output found.
A command line user interface has to be provided as follows:
Enter your input file name:
Display the input before: /* display the input integers following a statement */
Display the output after the operation: /* display the resulting output on the screen */
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


