Programming in Cbomb lab phase_2. Need answers about six numbers. This is bomb lab phase_2. I need help with the answer of the six integers.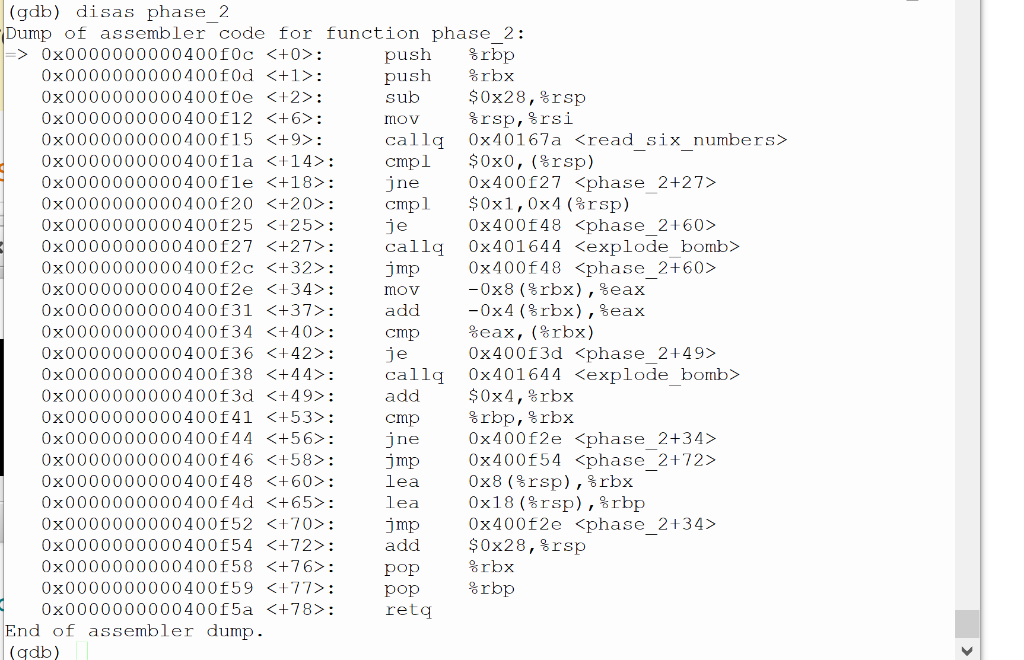
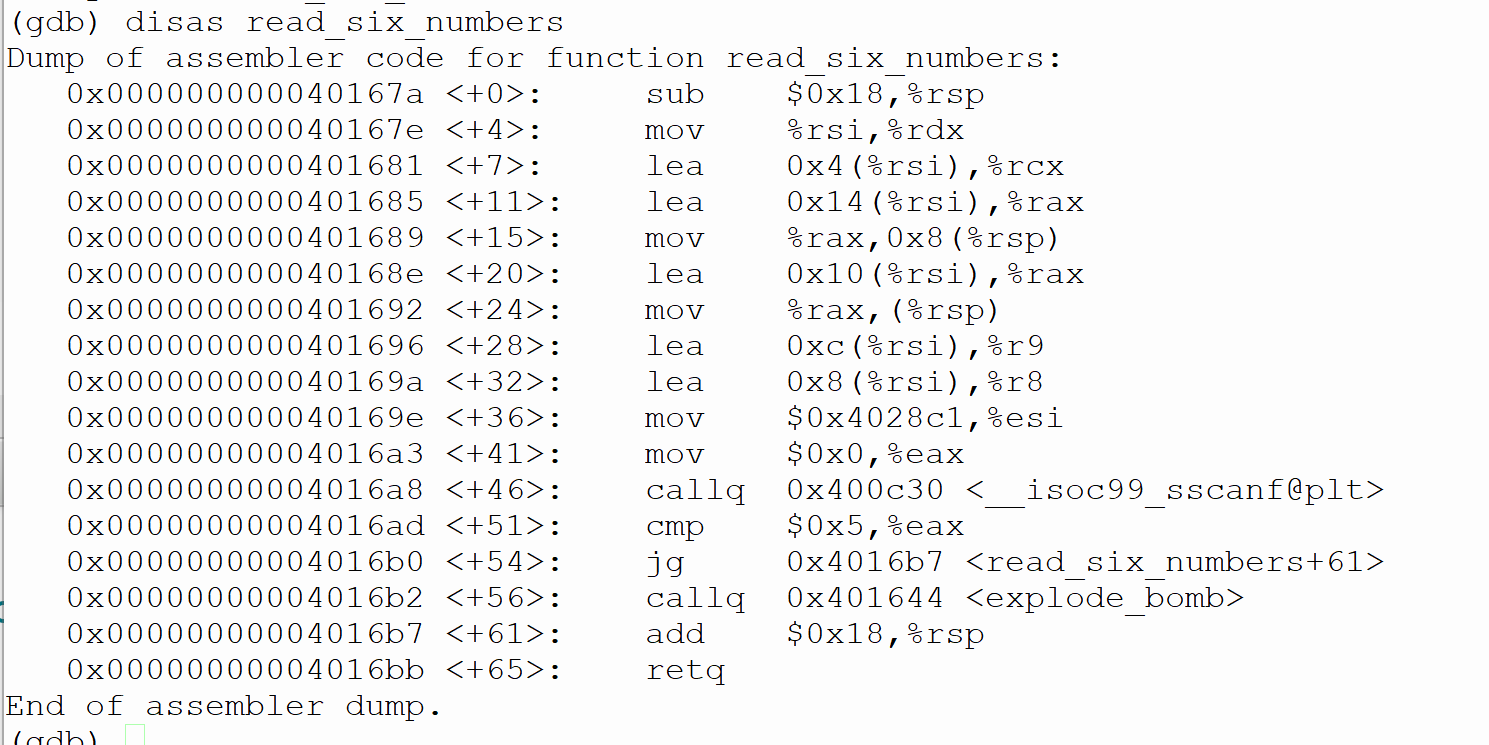
%rbp (gdb) disas phase_2 Dump of assembler code for function phase_2: => 0x0000000000400f0c : push 0x0000000000400f0d : push %rbx Ox0000000000400f0e : sub $0x28, %rsp 0x0000000000400f12 : mov 8rsp, Srsi Ox0000000000400f15 : callq 0x40167a
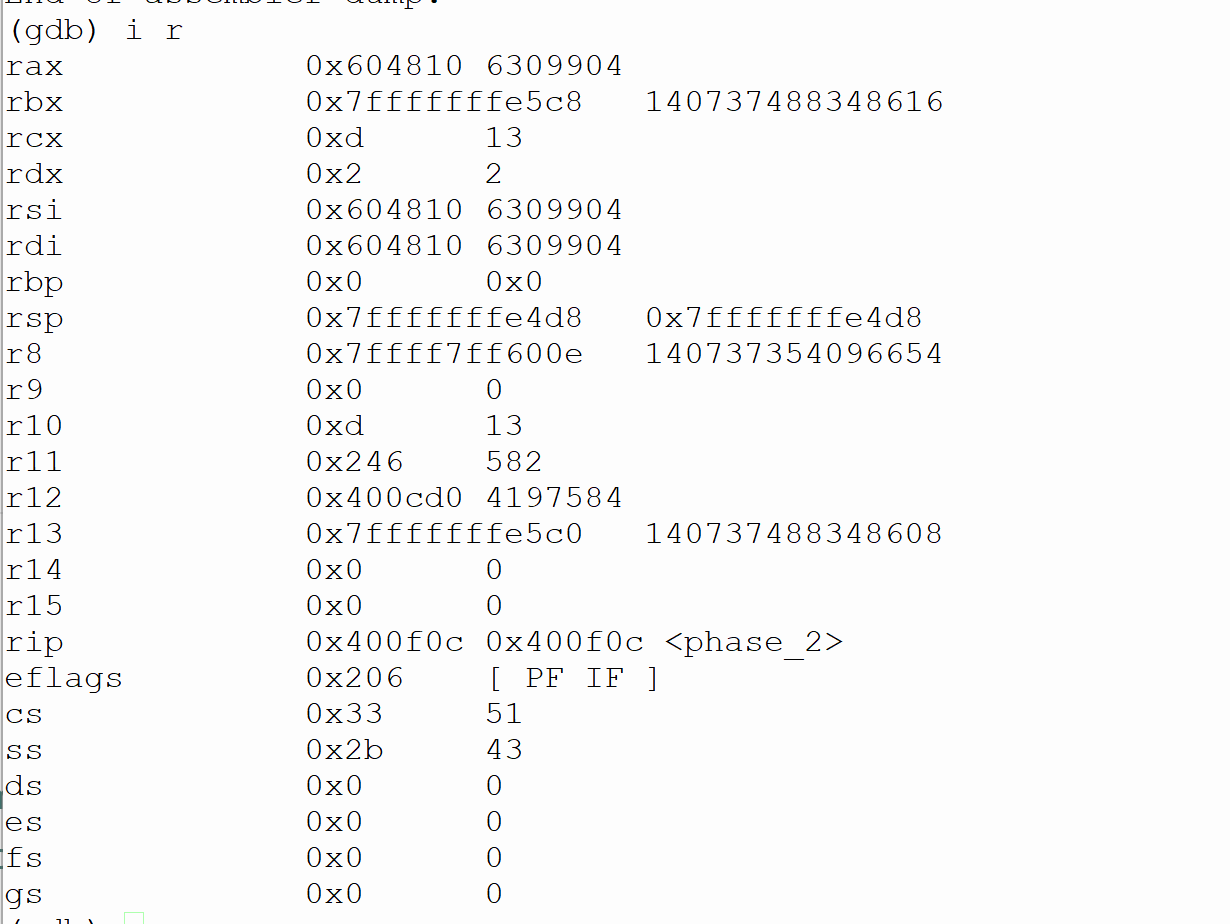
0x0000000000400fla : jne 0x400527 Ox0000000000400f20 : cmpl $0x1, 0x4 (%rsp) 0x0000000000400f25 : je 0x400f48 0x0000000000400827 : callq 0x401644 0x0000000000400f2c : jmp 0x400f48 0x0000000000400f2e : mov -Ox8 (Srbx), Seax Ox0000000000400f31 : add -Ox4 (Srbx), Seax Ox0000000000400f34 : cmp %eax, (&rbx) 0x0000000000400f36 : je 0x400f3d Ox0000000000400738 : calla 0x401644 Ox0000000000400f3d : add $0x4, Srbx 0x0000000000400f41 : cmp Srbp, Srbx Ox0000000000400544 : jne 0x400f2e Ox0000000000400846 : jmp 0x400f54 Ox0000000000400848 : lea Ox8 (Srsp), Srbx Ox0000000000400f4d : lea Ox18 (rsp), %rbp 0x0000000000400f52 : jmp 0x400f2e Ox0000000000400754 : add $0x28, 8rsp 0x0000000000400f58 : pop %rbx Ox0000000000400f59 : pop Srbp 0x0000000000400f5a : reta End of assembler dump. (db) (gdb) disas read_six_numbers Dump of assembler code for function read_six_numbers: 0x000000000040167a : sub $0x18, rsp 0x000000000040167e : mov prsi,%rdx 0x0000000000401681 : lea 0x4 (%rsi), rcx 0x0000000000401685 : lea Ox14(%rsi), rax Ox0000000000401689 : mov %rax, 0x8 (@rsp) Ox000000000040168e : lea Ox10 (%rsi), rax 0x0000000000401692 : mov %rax, (rsp) Ox0000000000401696 : lea 0x8 (prsi), r8 Ox000000000040169e : mov $0x4028c1, cesi Ox00000000004016a3 : mov $0x0, %eax Ox00000000004016a8 : callq 0x400030 0x00000000004016ad : cmp $0x5, %eax 0x000000000040160 : jg 0x4016b7 Ox00000000004016b2 : callq 0x401644 Ox00000000004016b7 : add $0x18,%rsp 0x00000000004016bb : reta End of assembler dump. Ladh (gdb) ir rax rbx rcx rdx rsi rdi rbp rsp r8 r9 r10 r11 r12 r13 r14 r15 rip eflags 0x604810 6309904 Ox7fffffffe5c8 140737488348616 Oxd 13 Ox2 2 0x604810 6309904 0x604810 6309904 Ox0 Ox0 0x7fffffffe4d8 0x7fffffffe4d8 0x7ffff7ff600e 140737354096654 Ox0 0 Oxd 13 0x246 582 0x400cdo 4197584 0x7fffffffe5c0 140737488348608 Ox0 0 Ox0 0 0x400f0c Ox400f0c 0x206 [ PF IF ] Ox33 51 0x2b 43 Ox0 0 Ox0 0 Ox0 Ox0 cs SS ds es fs gs 0 %rbp (gdb) disas phase_2 Dump of assembler code for function phase_2: => 0x0000000000400f0c : push 0x0000000000400f0d : push %rbx Ox0000000000400f0e : sub $0x28, %rsp 0x0000000000400f12 : mov 8rsp, Srsi Ox0000000000400f15 : callq 0x40167a 0x0000000000400fla : jne 0x400527 Ox0000000000400f20 : cmpl $0x1, 0x4 (%rsp) 0x0000000000400f25 : je 0x400f48 0x0000000000400827 : callq 0x401644 0x0000000000400f2c : jmp 0x400f48 0x0000000000400f2e : mov -Ox8 (Srbx), Seax Ox0000000000400f31 : add -Ox4 (Srbx), Seax Ox0000000000400f34 : cmp %eax, (&rbx) 0x0000000000400f36 : je 0x400f3d Ox0000000000400738 : calla 0x401644 Ox0000000000400f3d : add $0x4, Srbx 0x0000000000400f41 : cmp Srbp, Srbx Ox0000000000400544 : jne 0x400f2e Ox0000000000400846 : jmp 0x400f54 Ox0000000000400848 : lea Ox8 (Srsp), Srbx Ox0000000000400f4d : lea Ox18 (rsp), %rbp 0x0000000000400f52 : jmp 0x400f2e Ox0000000000400754 : add $0x28, 8rsp 0x0000000000400f58 : pop %rbx Ox0000000000400f59 : pop Srbp 0x0000000000400f5a : reta End of assembler dump. (db) (gdb) disas read_six_numbers Dump of assembler code for function read_six_numbers: 0x000000000040167a : sub $0x18, rsp 0x000000000040167e : mov prsi,%rdx 0x0000000000401681 : lea 0x4 (%rsi), rcx 0x0000000000401685 : lea Ox14(%rsi), rax Ox0000000000401689 : mov %rax, 0x8 (@rsp) Ox000000000040168e : lea Ox10 (%rsi), rax 0x0000000000401692 : mov %rax, (rsp) Ox0000000000401696 : lea 0x8 (prsi), r8 Ox000000000040169e : mov $0x4028c1, cesi Ox00000000004016a3 : mov $0x0, %eax Ox00000000004016a8 : callq 0x400030 0x00000000004016ad : cmp $0x5, %eax 0x000000000040160 : jg 0x4016b7 Ox00000000004016b2 : callq 0x401644 Ox00000000004016b7 : add $0x18,%rsp 0x00000000004016bb : reta End of assembler dump. Ladh (gdb) ir rax rbx rcx rdx rsi rdi rbp rsp r8 r9 r10 r11 r12 r13 r14 r15 rip eflags 0x604810 6309904 Ox7fffffffe5c8 140737488348616 Oxd 13 Ox2 2 0x604810 6309904 0x604810 6309904 Ox0 Ox0 0x7fffffffe4d8 0x7fffffffe4d8 0x7ffff7ff600e 140737354096654 Ox0 0 Oxd 13 0x246 582 0x400cdo 4197584 0x7fffffffe5c0 140737488348608 Ox0 0 Ox0 0 0x400f0c Ox400f0c 0x206 [ PF IF ] Ox33 51 0x2b 43 Ox0 0 Ox0 0 Ox0 Ox0 cs SS ds es fs gs 0









