Question
Python language Implement a password salt verification system and brute force attack. Given a UID (user id) list from 001 to 101 and corresponding Hash
Python language
Implement a password salt verification system and brute force attack. Given a UID (user id) list from 001 to 101 and corresponding Hash list at the bottom. The hash values are computed by concatenating the password value, which ranges from [0000, 1000], with the salt value, which range from [000, 100], using MD5 hashing.
Hash List:
4a1d6f102cd95fac33853e4d72fe1dc5 e8e7d67256aedc225a072540540d910c 0c6a7629e1fe2eab887de89dd65072d9 0e8b4ee66ad464aee37a934d74088613 6261a6ddd461304eaed4090348d8d117 cfa0000941daff46ebf0ef1950c86db0 e09a3a07abbaa5bf3170e6d297dff065 11dcc98c009eb5b2a9449d05ea8bb381 dfbcb13e80aa4cfb872f987b17879ec8 db8a21330a299c4fcae3534cc7f1e01b 8ec4312533793e33d092978b2c847330 5ac048a9173c4d6257c05cc1a26e1d06 5cfdff9a6b2859ed5aec0808dd50524e 83936eca815f642eb11970208520e2a3 6948e63fc20c099f4837d25a061439bc aa058ea92bebaa364f0153383c202c27 f48edac418318d0580653ed629069a24 6555bd5e2356ae34906cc724994a4b07 a9154393f28581eff2ca3b84b44f8702 89bf097de1f883368ef00e652fa2ae8d 04117ec99be1bcbd9f42da3228685f26 a5eec6aa303a169368cdb7a1b7818be8 e307b0acf8b5896c62ec0372ed3b7a38 594a723309b9b0bf3ca081ef4008c709 d303dd9e216a31f4f3422877b25012c6 fc97bd45eed421fd859d0a57d3c9168c 5689bc7ae71a56ca02f4a6fbeb221a65 ecf00e96b47634d0edd411a3ecd16d45 e2e9fbc8ee758be468a2f3e8164d5995 3f34c28d953d4279e7fec04cddf69d61 7b86f90ffebabff0bc29ed460da38414 9e537436c7751a0f75acee353f4e7fa3 e8e3742add907f94d2534e6c1431c021 74f4d9a79a5a4f17e231008269d8f126 9d016be6b4b7a8e0abbd7e81d48d54ad 926183d9745a0ad9531e339cecc27c32 b7321bde18b5bcabab68dcb2a3b59d8b 89f18f046ac58603900a73c34f5c88ac c9781a494696f39198bd87f863ffd2f1 cba36fe41dd35e38934109092111cb94 8c0f135b3e798427eee61cd59a377895 4d4ab45bff506e6f8b2530a60e4fbc84 093c57314f26e564f1edb847edf691f4 6ca04238450d2d76affc85441bfba832 e05b02d5732d420bb62c3175413b8f45 ecf7f3478a26f387d045956adf3b048b 1d706464afbf3138772167e9cd5ac648 2dfb337ff8cde7515ea3d99d169b6ab3 9c45c74b86973fb81748008496e643ea 2e86861267dfd51df069325ef8586eb1 814a5a817f7cecf59321d7b1b59512eb 760d293372257cd0af2c83d33a69e992 1ad2721523dcc547cbee3d4823c5f9cc 55df2796fee19ddd3860b950350fad28 cf855b8878ca23707b21abb06e6e9bfe 0460cf935180a5fb1bee794d2166dcc8 6ee6e1f98bb64faecf719fdec5935285 711a31e3af8b42f1af1dc30b747a4043 1de0c17431522b41496f4617b34ccbb6 c6ccbdd6e0e99d15738141c0882fc703 21542a4afaa446283d9dac62816b6f4f fe3d4de9a42fc0fbc0c7c7702149ddac f8c74793ea1534a510cd4c43c6724f98 3911e13c8f3345418ec1e756e0cc2325 170df1ce6c4cf82375cdf5751324666f 06c47b7fcf6fac367bd36a833a9ac627 eb42658c3b74e64470f1ce96dca09a97 8ac8b25c4ffdd19f40be9e9f121a8400 864287113da1db156d23553e91af2bca 8a1e10f94d0478895afc263478f5367f 8d361f8aa92bd601f06a0f050533edab f0ef3ea13c7f4d2a21a59d3daae7b73e 2ead2c8aec52e72dc872df8a9989517c 35b9853368c995b693cf0d0bafed0a03 8b981b46577e36238d238c88fd5502af e5c6d48896c5b988be046f8a48951f83 49868b6ce89f70b6b9b9e8c7cc1999c2 a288f9ce0700f58d67f8ad727fd6d7e8 5c3c31e58e5cbeabd7985226cf121152 986c5cbeb003ffa0751fcaacf650794c 766d04efe8bfbfbc59bd5dd3be786450 8016329915a96453c55c92f7ee06498f ea3a2dd7805e8ba5b7a3935971d37b48 5f6930065352317503ed73554b4270aa 6c2a30349ab3254936aa5eb587706a7f a52703e5c0850231e1b3f357a3b2eb11 380b6a7fc5116344ded301fe43add105 74140677f7e93c0faf8a40c21ac21d77 69a3a2c54b7c26c51b58983d092debf8 189c892a88ad58ed15210ee2168a2d77 690b0614d891d57c4300cba80e85a234 00662a81551bacf3f8dd738e2f429eef 9774c80bb94fa9dd404519895403e113 e8294e389ce622c139aa4d7c498763de 7a59c3ad66de26084c3085d98b8393f8 cf0bfe66bc5e6fc77a9db06699a8d6c0 6a2c733c6cc3fc8a548386d9daac24d2 8e7f3ac790fbdc624e01d9ec50071752 3b3542579462ba4654040def945b11ce 0105db564c086d336422b4a033862018
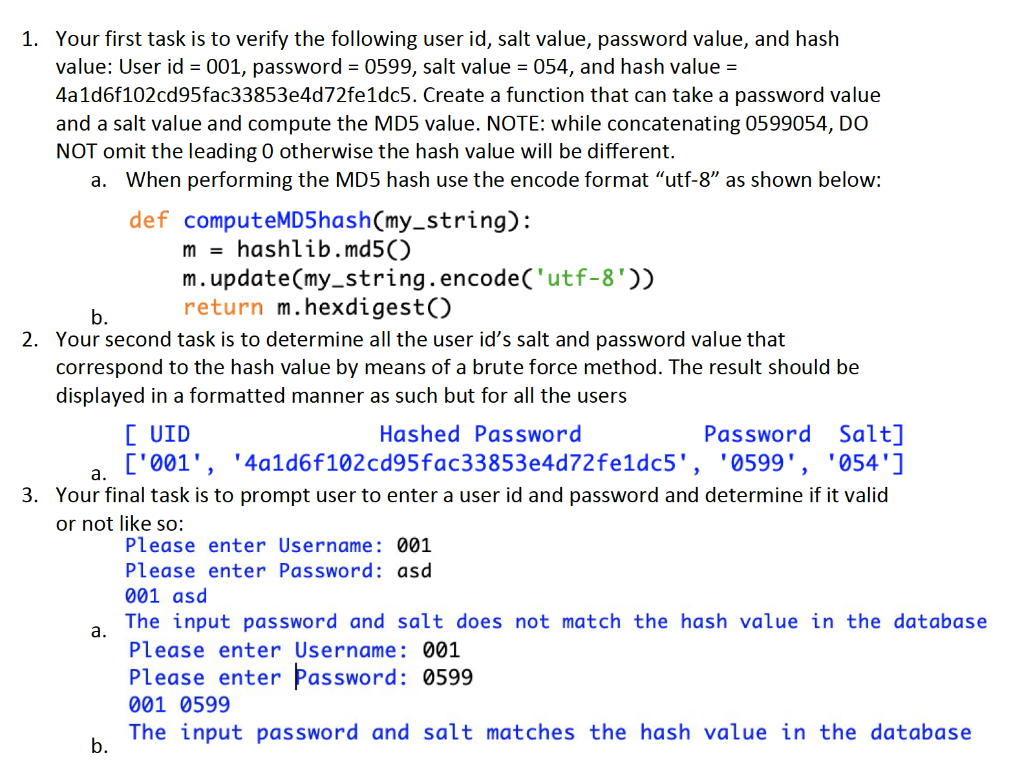
1. Your first task is to verify the following user id, salt value, password value, and hash value: User id = 001, password = 0599, salt value = 054, and hash value = 4a1d6f102cd95fac33853e4d72fe1dc5. Create a function that can take a password value and a salt value and compute the MD5 value. NOTE: while concatenating 0599054, DO NOT omit the leading 0 otherwise the hash value will be different. a. When performing the MD5 hash use the encode format "utf-8" as shown below: def computeMD5hash(my_string): m = hashlib.md5 m.update(my_string.encode('utf-8')) return m.hexdigest() 2. Your second task is to determine all the user id's salt and password value that correspond to the hash value by means of a brute force method. The result should be displayed in a formatted manner as such but for all the users [UID Hashed Password Password Salt] a. ['001', '4a1d6f102cd95fac33853e4d72fe1dc5', '0599', '054'] 3. Your final task is to prompt user to enter a user id and password and determine if it valid or not like so: Please enter Username: 001 Please enter Password: asd 001 asd The input password and salt does not match the hash value in the database Please enter Username: 001 Please enter Password: 0599 001 0599 The input password and salt matches the hash value in the databaseStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


