Answered step by step
Verified Expert Solution
Question
1 Approved Answer
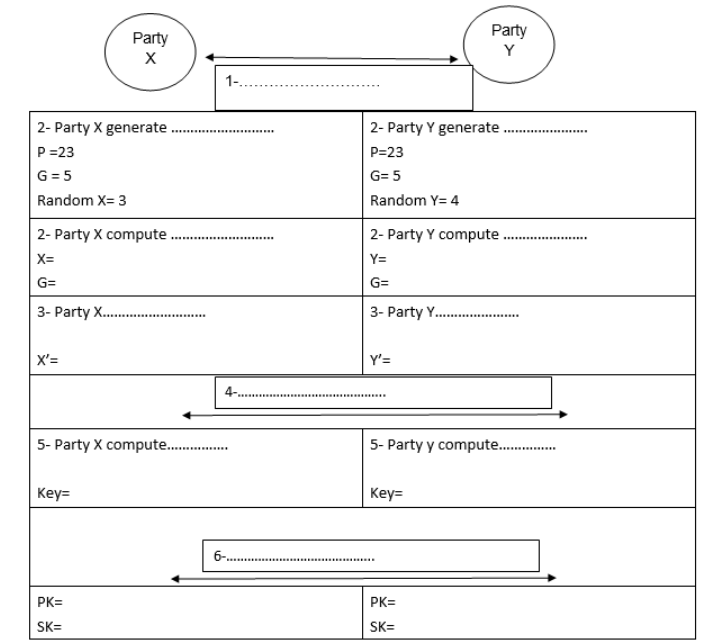
Q1: Fill up the blank in the below figure with the answers that explain the process of keying using Diffie-Hellman Key Agreement? Extract the public
Q1:
Fill up the blank in the below figure with the answers that explain the process of keying using Diffie-Hellman Key Agreement?
Extract the public keys (PKs) and secret keys (SKs) .
Consider the following rules: P(Prime) > 2, G(integer)
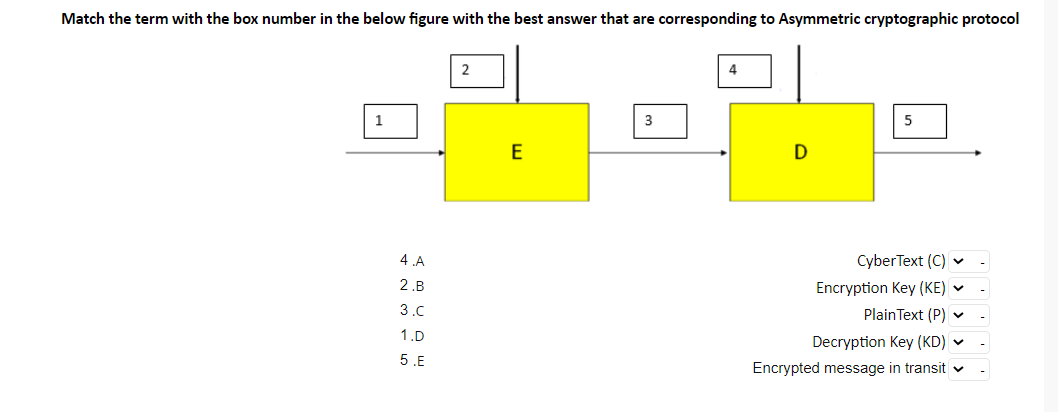
Q2:
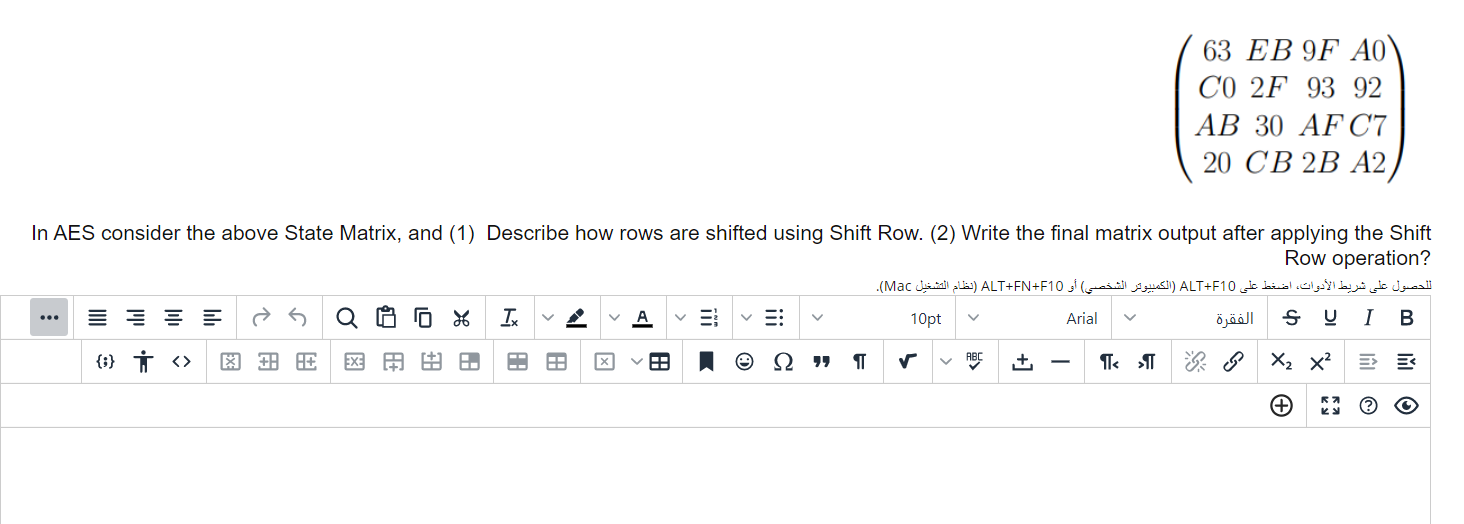
Q3:
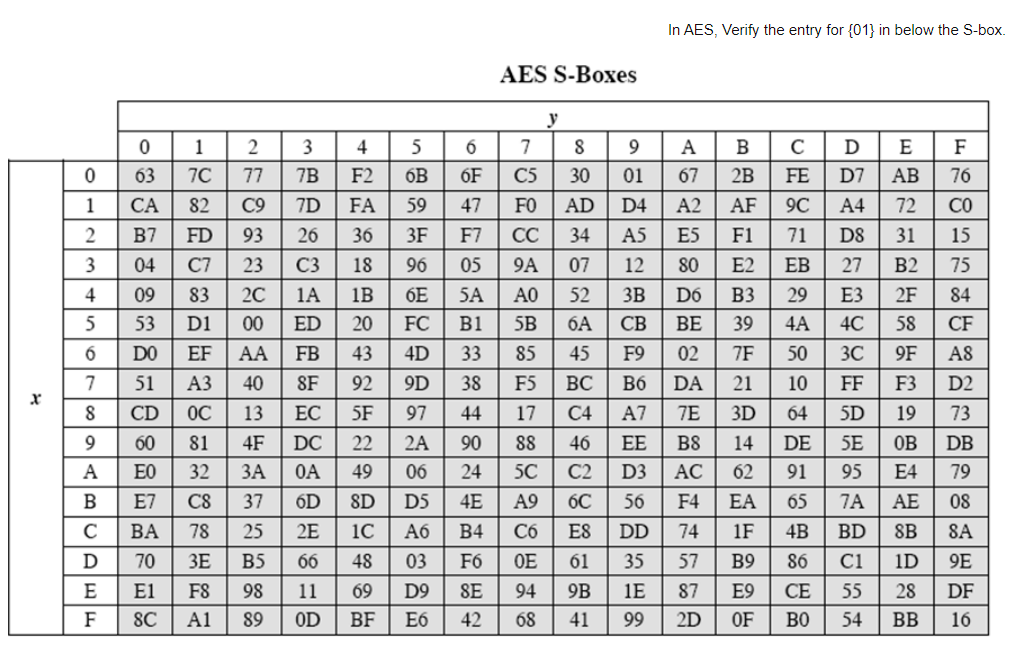
Q4:
Q5:
thats A homework how i give you more information? . thats all i have
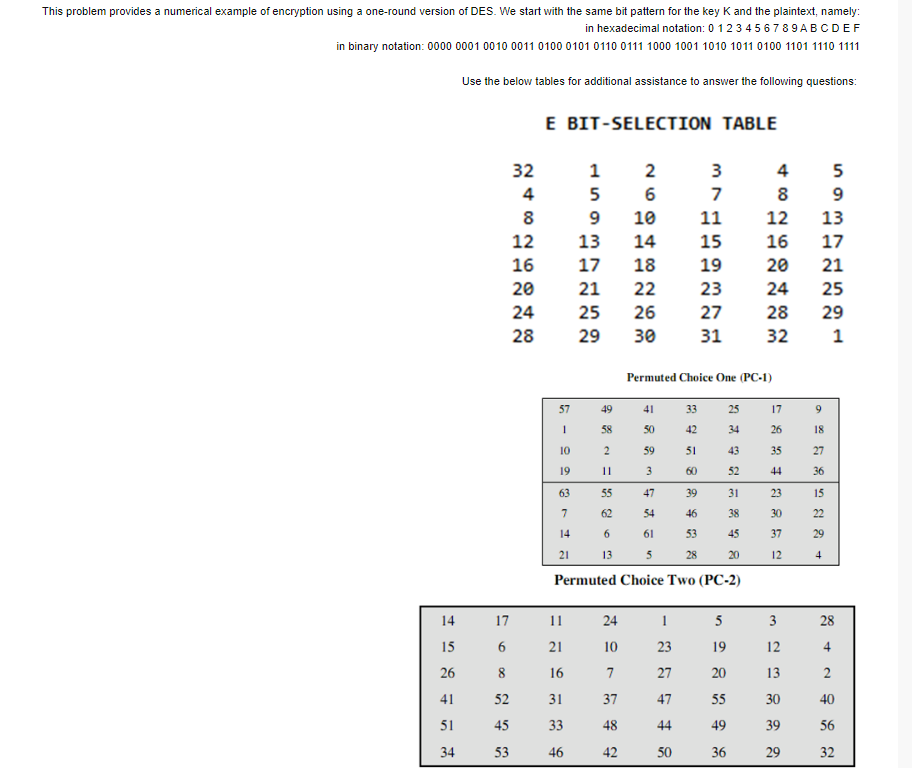
CyberText (C) Encryption Key (KE) PlainText (P) Decryption Key (KD) Encrypted message in transit 63C0AB20EB2F30C9F93AF2BA092C7A2 In AES consider the above State Matrix, and (1) Describe how rows are shifted using Shift Row. (2) Write the final matrix output after applying the Shift Row operation? In AES, Verify the entry for {01} in below the S-box. AES S-Boxes This problem provides a numerical example of encryption using a one-round version of DES. We start with the same bit pattern for the key K and the plaintext, namely: in hexadecimal notation: 0123456789ABCDEF in binary notation: 000000010010001101000101011001111000100110101011010011011101111 Use the below tables for additional assistance to answer the following questions: Permuted Choice One (PC-1) Permuted Choice Two (PC-2)
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


