Question: Q.1.1 Q.1.2 Q.1.3 Q.1.4 Using an example for each of the different types of social engineering approaches, explain what is and how each can
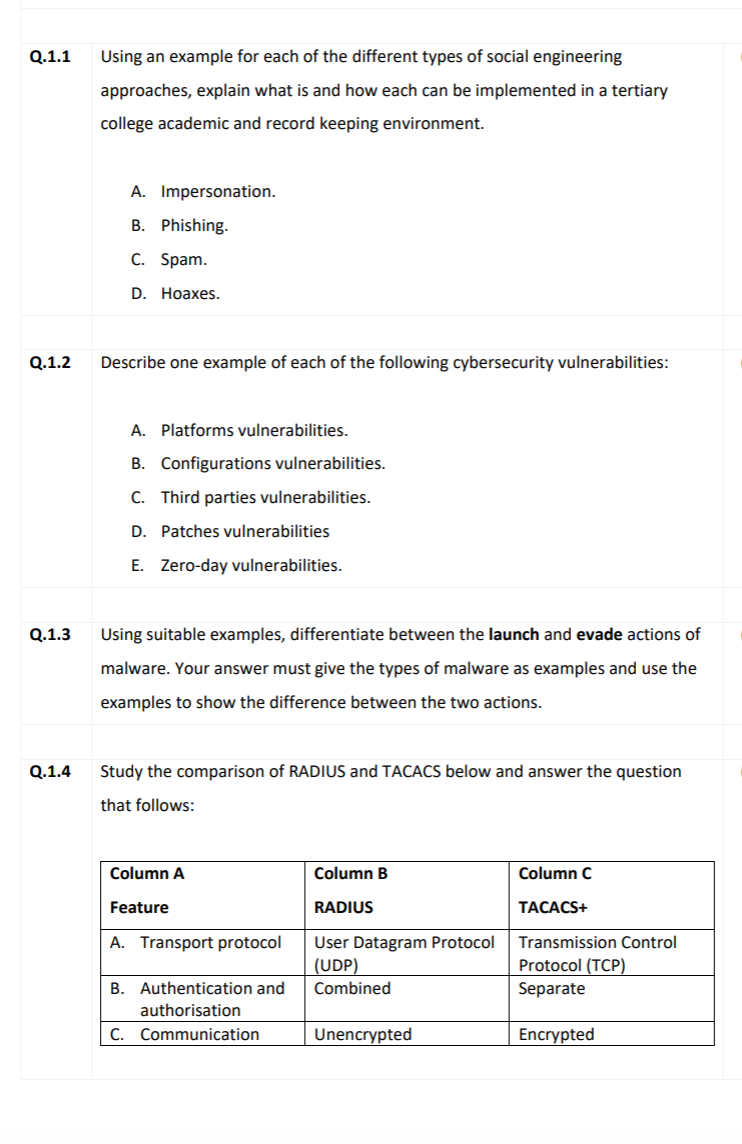
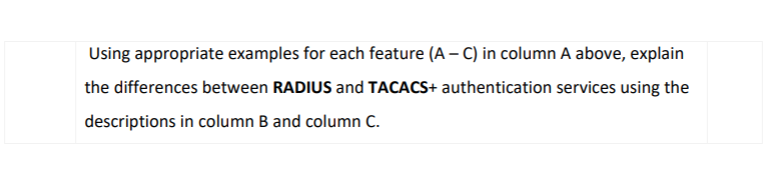
Q.1.1 Q.1.2 Q.1.3 Q.1.4 Using an example for each of the different types of social engineering approaches, explain what is and how each can be implemented in a tertiary college academic and record keeping environment. A. Impersonation. B. Phishing. C. Spam. D. Hoaxes. Describe one example of each of the following cybersecurity vulnerabilities: A. Platforms vulnerabilities. B. Configurations vulnerabilities. C. Third parties vulnerabilities. D. Patches vulnerabilities E. Zero-day vulnerabilities. Using suitable examples, differentiate between the launch and evade actions of malware. Your answer must give the types of malware as examples and use the examples to show the difference between the two actions. Study the comparison of RADIUS and TACACS below and answer the question that follows: Column A Feature A. Transport protocol B. Authentication and authorisation C. Communication Column B RADIUS User Datagram Protocol (UDP) Combined Unencrypted Column C TACACS+ Transmission Control Protocol (TCP) Separate Encrypted Using appropriate examples for each feature (A - C) in column A above, explain the differences between RADIUS and TACACS+ authentication services using the descriptions in column B and column C.
Step by Step Solution
3.40 Rating (162 Votes )
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


