Question
Q1-Which of the following would be BEST to establish between organizations to define the responsibilities of each party outline the key deliverables and include monetary
Q1-Which of the following would be BEST to establish between organizations to define the responsibilities of each party outline the key deliverables and include monetary penalties for breaches to manage third-party risk? A. An ARO B. An MOU C. An SLA D. A BPA ..............................................................
Q2-A security analyst is looking for a solution to help communicate to the leadership team the seventy levels of the organizations vulnerabilities. Which of the following would BEST meet this need? A. CVE B. SIEM C. SOAR D. CVSS ..............................................................
Q3-An organization has hired a security analyst to perform a penetration test. The analyst captures 1Gb worth of inbound network traffic to the server and transfer the pcap back to the machine for analysis. Which of the following tools should the analyst use to further review the pcap? A. Nmap B. cURL C. Netcat D. Wireshark
..............................................................
Q4-Under GDPR, which of the following is MOST responsible for the protection of privacy and website user rights? A. The data protection officer B. The data processor C. The data owner D. The data controller
..............................................................
Q5-Employees are having issues accessing the company's website. Some employees report very slow performance, while others cannot the website at all. The web and security administrators search the logs and find millions of half-open connections to port 443 on the web server. Further analysis reveals thousands of different source IPs initiating this traffic. Which of the following attacks is MOST likely occurring? A. DDoS B. Man-in-the-middle C. MAC flooding D. Domain hijacking
..............................................................
Q6-A security analyst receives a SIEM alert that someone logged in to the appadmin test account, which is only used for the early detection of attacks. The security analyst then reviews the following application log: 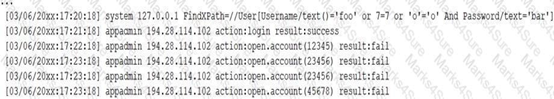 Which of the following can the security analyst conclude? A. A replay attack is being conducted against the application.
Which of the following can the security analyst conclude? A. A replay attack is being conducted against the application.
B. An injection attack is being conducted against a user authentication system.
C. A service account password may have been changed, resulting in continuous faile logins within the application. D. A credentialed vulnerability scanner attack is testing several CVEs against the application.
..............................................................
Q7-A security analyst is investigation an incident that was first reported as an issue connecting to network shares and the internet, While reviewing logs and tool output, the analyst sees the following:  Which of the following attacks has occurred? A.IP conflict B. Pass-the-hash C. MAC flooding D. Directory traversal E. ARP poisoning
Which of the following attacks has occurred? A.IP conflict B. Pass-the-hash C. MAC flooding D. Directory traversal E. ARP poisoning
..............................................................
Q8-During an incident response, a security analyst observes the following log entry on the web server.  Which of the following BEST describes the type of attack the analyst is experience? A. SQL injection B. Cross-site scripting C. Pass-the-hash D. Directory traversal
Which of the following BEST describes the type of attack the analyst is experience? A. SQL injection B. Cross-site scripting C. Pass-the-hash D. Directory traversal
..............................................................
Q9-A public relations team will be taking a group of guest on a tour through the facility of a large e-commerce company. The day before the tour, the company sends out an email to employees to ensure all whiteboars are cleaned and all desks are cleared. The company is MOST likely trying to protect against. A. Loss of proprietary information B. Damage to the companys reputation C. Social engineering D. Credential exposure
PASSWOBO Marks /textale ASMarks [03/06/20xx:17:20:18) system 127.0.0.1 FindXPath=//User (Username/text()='foo' or 7-7 or [03/06/20xx:17:21:18) appaamn 194.28.114.102 action: login result:success [03/06/20xx:17:22:18] appadmin 194.28.114.102 action:open account (12345) result:fail (03/06/20xx:17:23:18] appadmin 194.28.114.102 action:open account (23456) result:fail [03/06/20xx:17:23:18) appadmin 194.28.114.102 action:open.account (23456) result:fail [03/06/20xx:17:23:18] appadmin 194.28.114.102 action:open account (45678) result:fail Sure 084Sure Marksas Marks Marks Tko 22 saaress 20.0.0.3 10.0.0.114 20.0.0.115 10.0.0.216 10.0.0.117 Physical address 20-18-21-ad-24-be 01-31-a3-cd-23-ab 00-18-22-ad-24-be 00-19-08-ba-07-da 01-12-21-ca-11-ad 622 http://vam, conpanyaits. cb/product_info.php?stor..../..../etc/pasand #78/8.1 Hosti www.companysite.com
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


