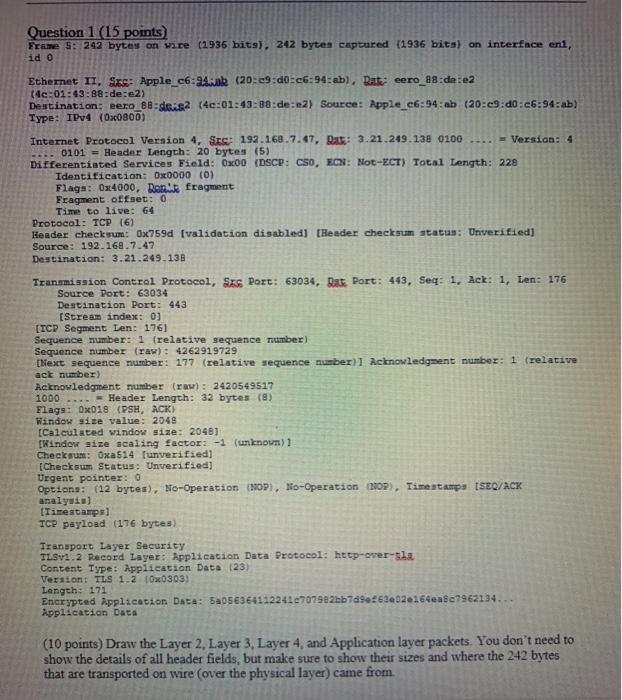
Question 1 (15 points) Frame 5: 242 bytes on ware (1936 bits), 242 bytes captured (1936 bits) on interface eni, ido Ethernet II, Sixe: Apple_c6:94.ak (20:09:d0:c6:94:ab). Rat: eero_08:de:e2 (40:01:43:88:de:2) Destination: eero_88de2 (40:01:43:38:de:e2) Source: Apple_c6:94: ab (20:e9:d0:c6:94:ab) Type: IPv4 (0X0800) Internet Protocol Version 4, SES: 192.168.7.47, Das: 3.21.249.138 0100 ... - Version: 4 0101 = Header Length: 20 bytes (5) Differentiated Services Field: 0x00 (DSCP: CSO, EON: Not-ECT) Total Length: 228 Identification: 0x0000 (0) Flags: 02:4000, Don't fragment Fragment offset: 0 Time to live: 64 Protocol: TCP (6) Header checkwum: 0x759d (validation disabled[Header checksum status: Unverified) Source: 192.168.7.47 Destination: 3.21.249.138 Transmission Control Protocol, Sxs Port: 63034, Bare Port:443, Seq: 1. Ack: 1, Len: 176 Source Port: 63034 Destination Port:443 (Stream index: 0] (ICP Segment Len: 1761 Sequence number: 1 [relative sequence number Sequence number (raw): 4262919729 [Next sequence number: 177 (relative sequence number}] Acknowledgment number: 1 (relative ack number) Acknowledgment number (raw)2420549517 1000 .... = Header Length: 32 bytes (8) Flags : 0x018 (PSH, ACK) Window size value: 2048 (Calculated window size: 2048) [Rindow size scaling factor: -1 (unknown) 1 Checksum: Oxa514 Iunverified] Checksum Status: Unverified) Urgent pointer: 0 Options: (12 bytes), No-Operation (N), No-Operation 102), Timestamp (SEO/ACK analysis [Timestamps) TCP payload (176 bytes) Transport Layer Security TLSv1.2 Record Layer: Application Data Protocol: http-er-sla Content Type: Application Data (23) Version: TLS 1.2 Ox0303) Length: 171 Enerypted application Data: 50563641122417079e2bb749e53e02e164ea8c7962134... Application Data (10 points) Draw the Layer 2 Layer 3. Layer 4, and Application layer packets. You don't need to show the details of all header fields, but make sure to show their sizes and where the 242 bytes that are transported on wire (over the physical layer) came from. Question 1 (15 points) Frame 5: 242 bytes on ware (1936 bits), 242 bytes captured (1936 bits) on interface eni, ido Ethernet II, Sixe: Apple_c6:94.ak (20:09:d0:c6:94:ab). Rat: eero_08:de:e2 (40:01:43:88:de:2) Destination: eero_88de2 (40:01:43:38:de:e2) Source: Apple_c6:94: ab (20:e9:d0:c6:94:ab) Type: IPv4 (0X0800) Internet Protocol Version 4, SES: 192.168.7.47, Das: 3.21.249.138 0100 ... - Version: 4 0101 = Header Length: 20 bytes (5) Differentiated Services Field: 0x00 (DSCP: CSO, EON: Not-ECT) Total Length: 228 Identification: 0x0000 (0) Flags: 02:4000, Don't fragment Fragment offset: 0 Time to live: 64 Protocol: TCP (6) Header checkwum: 0x759d (validation disabled[Header checksum status: Unverified) Source: 192.168.7.47 Destination: 3.21.249.138 Transmission Control Protocol, Sxs Port: 63034, Bare Port:443, Seq: 1. Ack: 1, Len: 176 Source Port: 63034 Destination Port:443 (Stream index: 0] (ICP Segment Len: 1761 Sequence number: 1 [relative sequence number Sequence number (raw): 4262919729 [Next sequence number: 177 (relative sequence number}] Acknowledgment number: 1 (relative ack number) Acknowledgment number (raw)2420549517 1000 .... = Header Length: 32 bytes (8) Flags : 0x018 (PSH, ACK) Window size value: 2048 (Calculated window size: 2048) [Rindow size scaling factor: -1 (unknown) 1 Checksum: Oxa514 Iunverified] Checksum Status: Unverified) Urgent pointer: 0 Options: (12 bytes), No-Operation (N), No-Operation 102), Timestamp (SEO/ACK analysis [Timestamps) TCP payload (176 bytes) Transport Layer Security TLSv1.2 Record Layer: Application Data Protocol: http-er-sla Content Type: Application Data (23) Version: TLS 1.2 Ox0303) Length: 171 Enerypted application Data: 50563641122417079e2bb749e53e02e164ea8c7962134... Application Data (10 points) Draw the Layer 2 Layer 3. Layer 4, and Application layer packets. You don't need to show the details of all header fields, but make sure to show their sizes and where the 242 bytes that are transported on wire (over the physical layer) came from