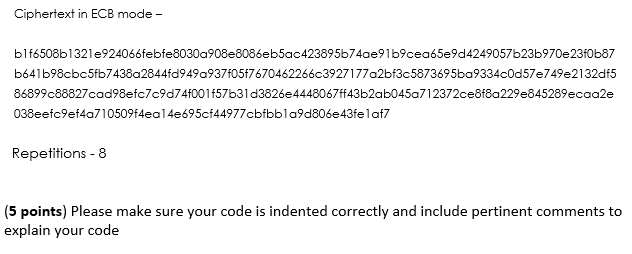
Question 1 (45 points) Martha is a cryptanalyst. She recently intercepted a series of suspicious (and encrypted) communication. Martha is confident that AES-128 in ECB mode was used to encrypt one of the messages. Help Martha confirm her suspicions by determining which ciphertext in the file "ciphertexts.txt" was encrypted using AES in ECB mode and how many repetitions can be found between the individual 16 -byte blocks of ciphertext. You are strongly encouraged to use Python for this assignment. Use the PyCryptodome library for any cryptographic primitives you may require. While the PyCrypto library is popular, please do not use it in this assignment because it has been deprecated. For simplicity, you may assume the following about the ciphertexts in the file. - Only one of the ciphertexts was encrypted using the ECB mode - You may assume that AES- 128 was used so, the block size is 16 bytes - There is one ciphertext per line in the file - No padding was used, and the plaintext was split into several 16-byte blocks. - Some ciphertexts were encrypted using AES in CTR mode or CBC mode. Random initialization vectors (IV) and counter values were used for these modes. - The ciphertexts in "ciphertexts.txt" are hexadecimal encoded. So, you will need to convert the encoded string into binary data to identify the 16-byte blocks. Your code must contain the following methods. - (20 points) countRepetitions that takes a ciphertext as an argument and returns the total number of repetitions between all 16-byte blocks - (20 points) detectECBMode that takes a ciphertext as input, determines if any repetitions occur, and returns a Boolean value indicating if the ciphertext was encryptec using ECB mode Your code must display the ECB encrypted ciphertext encoded in the hexadecimal format followed by the number of repetitions (in the following line). For example, if you encounter ten blocks with the same ciphertext, then there are nine repetitions of the 1st block so, the number of repetitions is 9. Your output should look something like the following. Sample output: blf6508b132le924066febfe8030a908e8086eb5ac423895b74ae91b9cea65e9d4249057b23b970e23f0b87b641b98cbc5fb7438a2844fd949a937f05f7670462266b3927177a2bf3c5873695ba9334c0d57e749e2132df586899c88827cad98efc7c9d74f001f57b31d3826e4448067ff43b2ab045a712372ce8f8a229e845289ecaa2e038eefc9ef4a710509f4eale695cf44977cbfbbla9d806e43felaf7Repetitions-8 (5 points) Please make sure your code is indented correctly and include pertinent comments to explain your code








