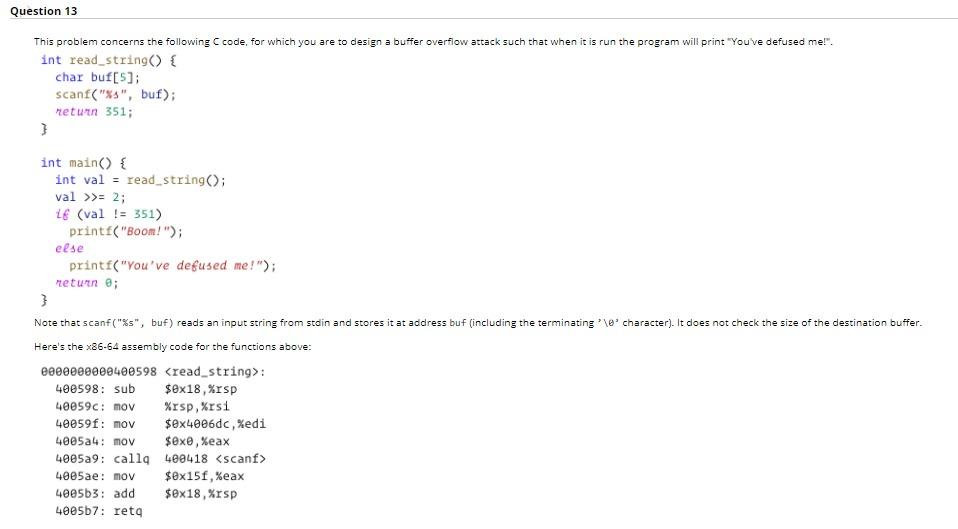
Question 13 This problem concerns the following code, for which you are to design a buffer overflow attack such that when it is run the program will print "Youve defused me!". int read_string() { char buf[5]; scanf("%s", buf); meturn 351; } int main() { int val = read_string(); val >>= 2; 16 (val != 351) printf("Boom!"); else printf("You've defused me!"); return; Note that scanf("%s", buf) reads an input string from stain and stores it at address buf (including the terminating '\e character). It does not check the size of the destination buffer. Here's the x86-64 assembly code for the functions above: Bee0000000400598
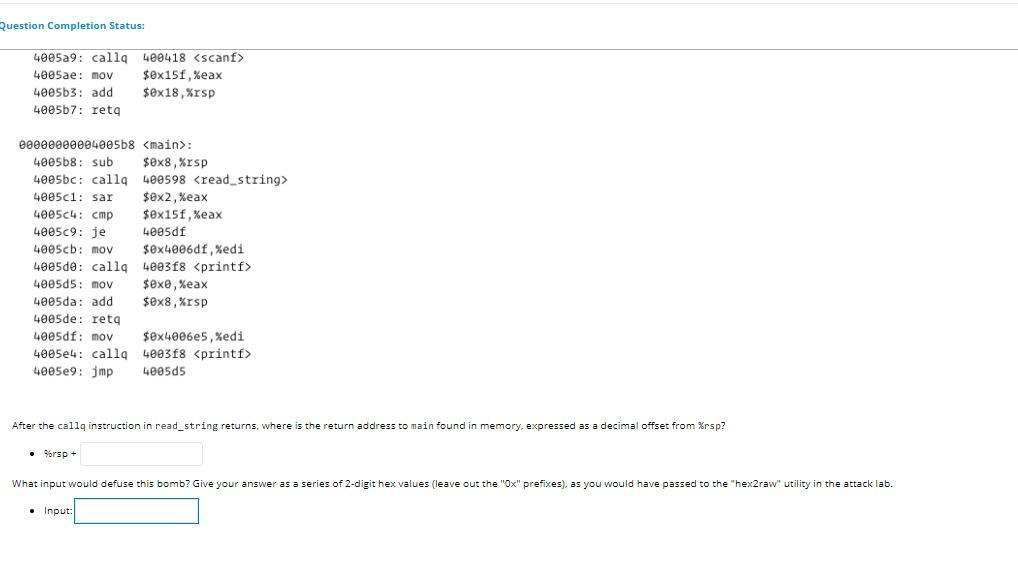
: 400598: sub $ex18, %rsp 40059c: mov %rsp, %rsi 40059f: mov $ex4006dc, Xedi 4005a4: MOV $exe, %eax 4005a9: calla 400418 4005ae: mov $ex15f, Keax 4005b3: add $ex18, Xrsp 4005b7: reta Question Completion Status: 4005a9: calla 400418 4005ae: mov $0x15f, %eax 4005b3: add $0x18, Xrsp 4005b7: reta 00000000004005b8 : 400568: sub $ex8,%rsp 4005bc: calla 400598 4005ci: sar $ex2, %eax 400504: cmp $ex15f, %eax 400509: je 4095df 4005cb: mov $ex40e6df, Xedi 4005de: calla 4003f8 400505: mov $exe, %eax 4005da: add $ex8, %rsp 4005de: reta 4005df: mov $ex4006e5, Xedi 4005e4: calla 4003f8 4005e9: jmp 400505 After the call instruction in read_string returns, where is the return address to main found in memory, expressed as a decimal offset from Xrsp? Sorsp + What input would defuse this bomb? Give your answer as a series of 2-digit hex values (leave out the "0x" prefixes), as you would have passed to the "hex2raw" utility in the attack lab. Input Question 13 This problem concerns the following code, for which you are to design a buffer overflow attack such that when it is run the program will print "Youve defused me!". int read_string() { char buf[5]; scanf("%s", buf); meturn 351; } int main() { int val = read_string(); val >>= 2; 16 (val != 351) printf("Boom!"); else printf("You've defused me!"); return; Note that scanf("%s", buf) reads an input string from stain and stores it at address buf (including the terminating '\e character). It does not check the size of the destination buffer. Here's the x86-64 assembly code for the functions above: Bee0000000400598 : 400598: sub $ex18, %rsp 40059c: mov %rsp, %rsi 40059f: mov $ex4006dc, Xedi 4005a4: MOV $exe, %eax 4005a9: calla 400418 4005ae: mov $ex15f, Keax 4005b3: add $ex18, Xrsp 4005b7: reta Question Completion Status: 4005a9: calla 400418 4005ae: mov $0x15f, %eax 4005b3: add $0x18, Xrsp 4005b7: reta 00000000004005b8 : 400568: sub $ex8,%rsp 4005bc: calla 400598 4005ci: sar $ex2, %eax 400504: cmp $ex15f, %eax 400509: je 4095df 4005cb: mov $ex40e6df, Xedi 4005de: calla 4003f8 400505: mov $exe, %eax 4005da: add $ex8, %rsp 4005de: reta 4005df: mov $ex4006e5, Xedi 4005e4: calla 4003f8 4005e9: jmp 400505 After the call instruction in read_string returns, where is the return address to main found in memory, expressed as a decimal offset from Xrsp? Sorsp + What input would defuse this bomb? Give your answer as a series of 2-digit hex values (leave out the "0x" prefixes), as you would have passed to the "hex2raw" utility in the attack lab. Input








