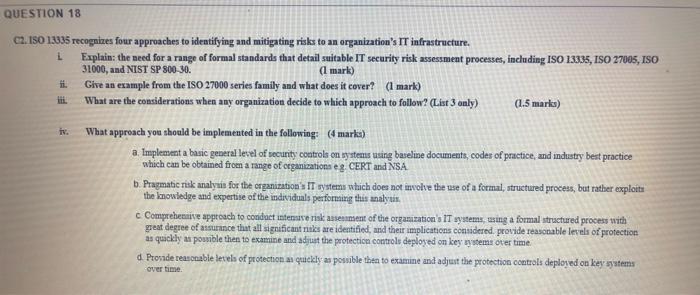
QUESTION 18 C2. ISO 13335 recognizes four approaches to identifying and mitigating risks to an organization's IT infrastructure. L Explain: the need for a range of formal standards that detail suitable IT security risk assessment processes, including ISO 13335, ISO 27005, ISO 31000, and NIST SP 800 30. (1 mark) Give an example from the ISO 27000 series family and what does it cover? (1 mark) What are the considerations when any organization decide to which approach to follow? (List 3 only) (1.5 marks) iv. What approach you should be implemented in the following: (4 marka) a Implement a basic general level of security controla on systems using baseline documents, codes of practice, and industry best practice which can be obtame from a range of organizations eg CERT and NSA b. Pragmatic risk analysis for the organization's IT systems which does not involve the use of a formal, structured process, but rather exploits the knowledge and expertise of the individuals performing this analytis, c Comprehensive approach to conduct intense risk assement of the organization's IT systems, using a formal structured process with great degree of assurance that all significant risks are identified, and their implications considered. provide reasonable levels of protection as quickly as possible then to examine and adjust the protection controls deployed on key systems over time d Provide reasonable levels of protection as quickly as possible then to examine and adjust the protection controls deployed on key systems over time QUESTION 18 C2. ISO 13335 recognizes four approaches to identifying and mitigating risks to an organization's IT infrastructure. L Explain: the need for a range of formal standards that detail suitable IT security risk assessment processes, including ISO 13335, ISO 27005, ISO 31000, and NIST SP 800 30. (1 mark) Give an example from the ISO 27000 series family and what does it cover? (1 mark) What are the considerations when any organization decide to which approach to follow? (List 3 only) (1.5 marks) iv. What approach you should be implemented in the following: (4 marka) a Implement a basic general level of security controla on systems using baseline documents, codes of practice, and industry best practice which can be obtame from a range of organizations eg CERT and NSA b. Pragmatic risk analysis for the organization's IT systems which does not involve the use of a formal, structured process, but rather exploits the knowledge and expertise of the individuals performing this analytis, c Comprehensive approach to conduct intense risk assement of the organization's IT systems, using a formal structured process with great degree of assurance that all significant risks are identified, and their implications considered. provide reasonable levels of protection as quickly as possible then to examine and adjust the protection controls deployed on key systems over time d Provide reasonable levels of protection as quickly as possible then to examine and adjust the protection controls deployed on key systems over time