Answered step by step
Verified Expert Solution
Question
1 Approved Answer
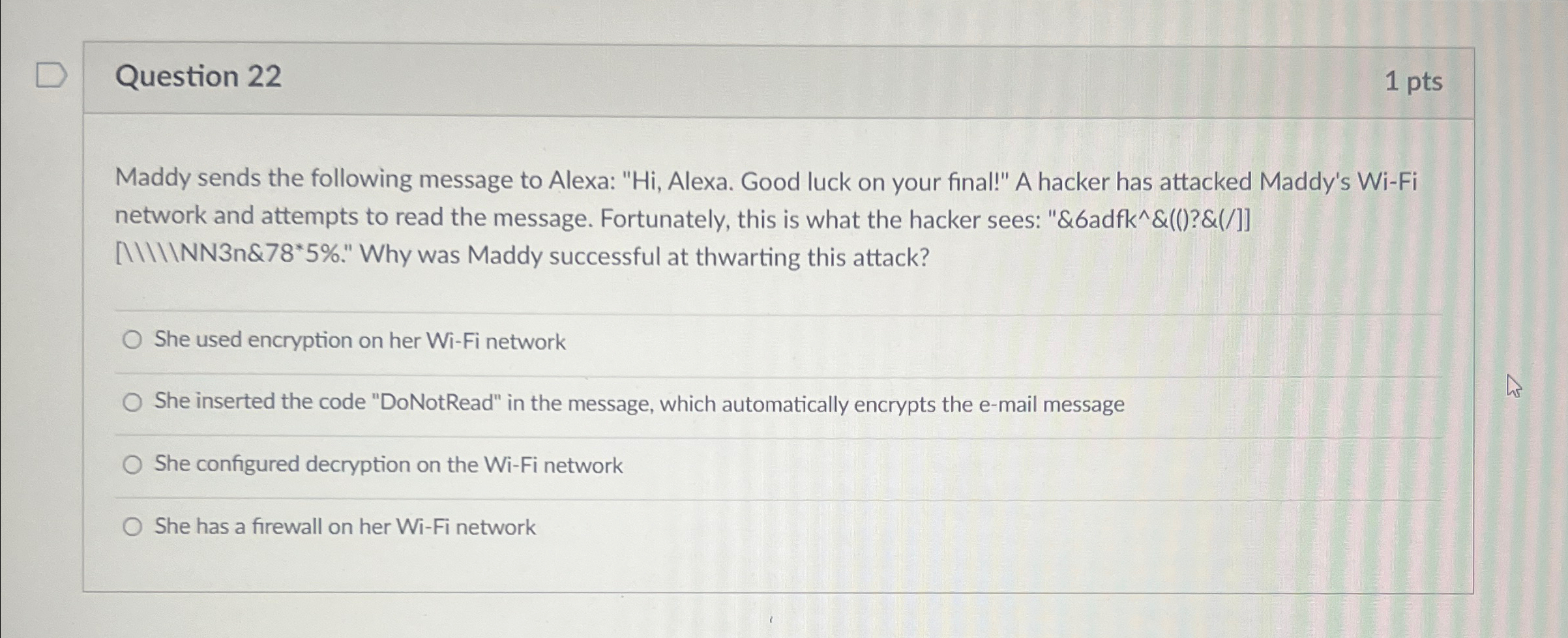
Question 2 2 1 pts Maddy sends the following message to Alexa: Hi , Alexa. Good luck on your final! A hacker has attacked
Question
pts
Maddy sends the following message to Alexa: Hi Alexa. Good luck on your final!" A hacker has attacked Maddy's WiFi network and attempts to read the message. Fortunately, this is what the hacker sees: &adfk &&IIIIINNn& Why was Maddy successful at thwarting this attack?
She used encryption on her WiFi network
She inserted the code "DoNotRead" in the message, which automatically encrypts the email message
She configured decryption on the WiFi network
She has a firewall on her WiFi network
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


