QUESTION 2
-
a) Consider a method train is going to call another method compute. The compute method has two input parameters and three local variables. It also needs to use registers R5, R6, R7 & R8, which are also used by the train method. What steps are necessary within the compute method to protect these registers, to use input parameters and local variables and finally to safely return to the train method?
Note: Assume that a stack is in place and the train method has already pushed the input parameters to stack for the compute method. You are using the 'callee saved' approach.
8 Marks
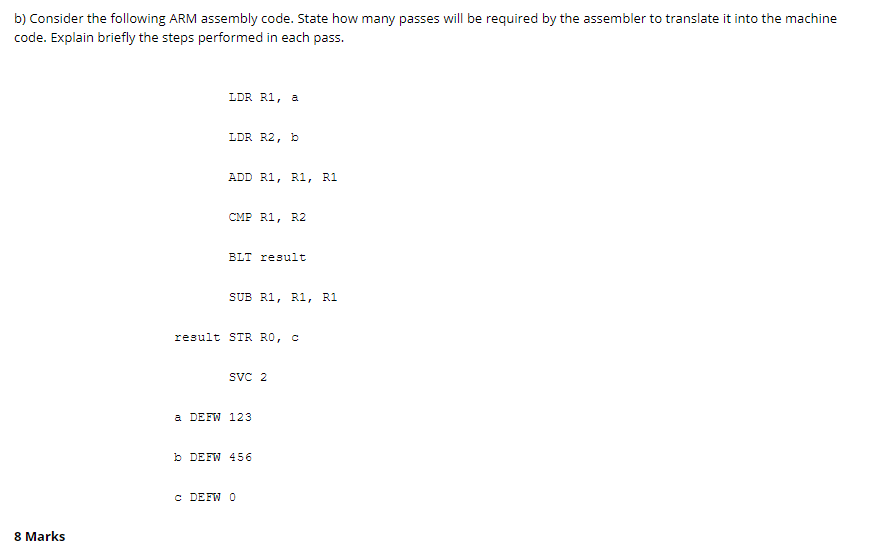
b) Consider the following ARM assembly code. State how many passes will be required by the assembler to translate it into the machine code. Explain briefly the steps performed in each pass.
LDR R1, a
LDR R2, b
ADD R1, R1, R1
CMP R1, R2
BLT result
SUB R1, R1, R1
result STR R0, c
SVC 2
a DEFW 123
b DEFW 456
c DEFW 0
8 Marks
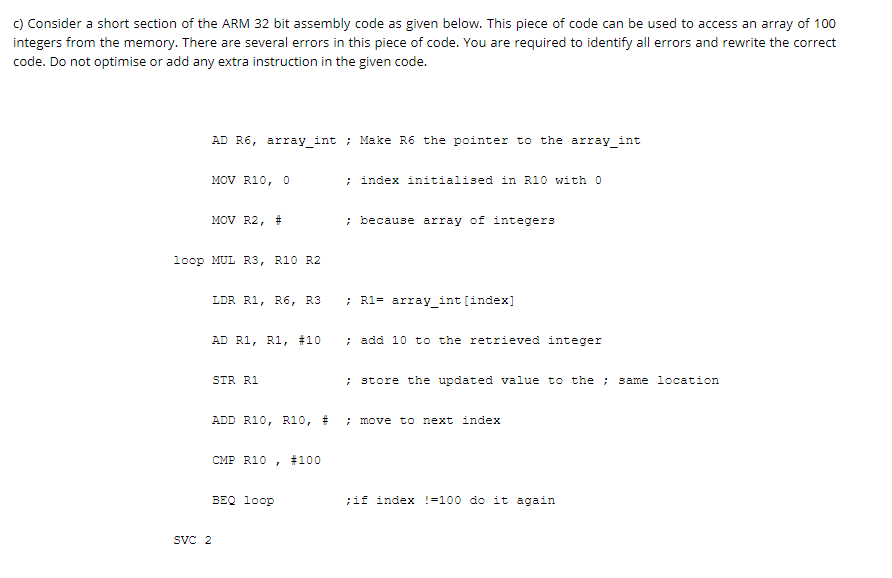
c) Consider a short section of the ARM 32 bit assembly code as given below. This piece of code can be used to access an array of 100 integers from the memory. There are several errors in this piece of code. You are required to identify all errors and rewrite the correct code. Do not optimise or add any extra instruction in the given code.
AD R6, array_int ; Make R6 the pointer to the array_int
MOV R10, 0 ; index initialised in R10 with 0
MOV R2, # ; because array of integers
loop MUL R3, R10 R2
LDR R1, R6, R3 ; R1= array_int[index]
AD R1, R1, #10 ; add 10 to the retrieved integer
STR R1 ; store the updated value to the ; same location
ADD R10, R10, # ; move to next index
CMP R10 , #100
BEQ loop ;if index !=100 do it again
SVC 2 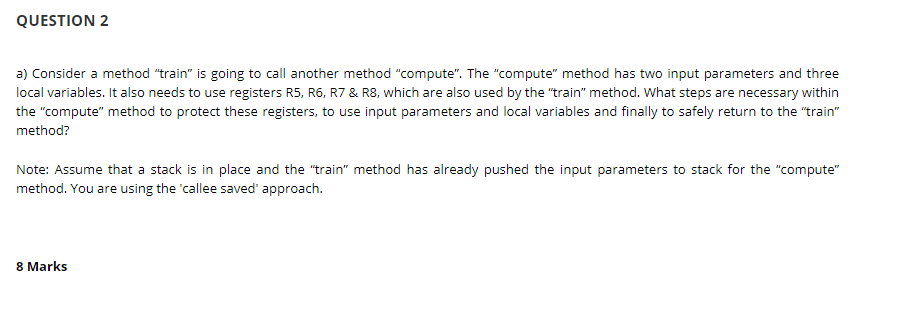
QUESTION 2 a) Consider a method "train" is going to call another method "compute". The "compute" method has two input parameters and three local variables. It also needs to use registers R5, R6, R7 & R8, which are also used by the "train" method. What steps are necessary within the "compute" method to protect these registers, to use input parameters and local variables and finally to safely return to the "train" method? Note: Assume that a stack is in place and the "train" method has already pushed the input parameters to stack for the "compute" method. You are using the 'callee saved' approach. 8 Marks b) Consider the following ARM assembly code. State how many passes will be required by the assembler to translate it into the machine code. Explain briefly the steps performed in each pass. LDR R1, a LDR R2, b ADD R1, R1, R1 CMP R1, R2 BLT result SUB RI, R1, R1 result STR RO, C SVC 2 a DEFW 123 bo DEFW 456 C DEB 0 8 Marks c) Consider a short section of the ARM 32 bit assembly code as given below. This piece of code can be used to access an array of 100 integers from the memory. There are several errors in this piece of code. You are required to identify all errors and rewrite the correct code. Do not optimise or add any extra instruction in the given code. AD R6, array_int ; Make R6 the pointer to the array_int MOV R10, 0 ; index initialised in R10 with o MOV R2, # ; because array of integers loop MUL R3, R10 R2 LDR R1, R6, R3 ; Ri= array_int[index] AD R1, Ri, #10 ; add 10 to the retrieved integer STR R1 ; store the updated value to the ; same location ADD R10, R10, # ; move to next index CMP R10 #100 BEQ loop ;if index !=100 do it again SVC 2 QUESTION 2 a) Consider a method "train" is going to call another method "compute". The "compute" method has two input parameters and three local variables. It also needs to use registers R5, R6, R7 & R8, which are also used by the "train" method. What steps are necessary within the "compute" method to protect these registers, to use input parameters and local variables and finally to safely return to the "train" method? Note: Assume that a stack is in place and the "train" method has already pushed the input parameters to stack for the "compute" method. You are using the 'callee saved' approach. 8 Marks b) Consider the following ARM assembly code. State how many passes will be required by the assembler to translate it into the machine code. Explain briefly the steps performed in each pass. LDR R1, a LDR R2, b ADD R1, R1, R1 CMP R1, R2 BLT result SUB RI, R1, R1 result STR RO, C SVC 2 a DEFW 123 bo DEFW 456 C DEB 0 8 Marks c) Consider a short section of the ARM 32 bit assembly code as given below. This piece of code can be used to access an array of 100 integers from the memory. There are several errors in this piece of code. You are required to identify all errors and rewrite the correct code. Do not optimise or add any extra instruction in the given code. AD R6, array_int ; Make R6 the pointer to the array_int MOV R10, 0 ; index initialised in R10 with o MOV R2, # ; because array of integers loop MUL R3, R10 R2 LDR R1, R6, R3 ; Ri= array_int[index] AD R1, Ri, #10 ; add 10 to the retrieved integer STR R1 ; store the updated value to the ; same location ADD R10, R10, # ; move to next index CMP R10 #100 BEQ loop ;if index !=100 do it again SVC 2









