Question: Question 3 [40 points] In cryptography, a simple substitution cypher is a method of encryption in which each letter of a phrase is replaced by
Question 3 [40 points] In cryptography, a simple substitution cypher is a method of encryption in which each letter of a phrase is replaced by a dierent letter or sequence of letters. The phrase can then be decrypted by performing the inverse of the substitution. In this question, we will implement a simple substitution cypher in which a character (letter, number, or special symbol) is substituted by a two-digit number between 00 and 99 (inclusive). For example, the letter `a' could be encrypted to become the number `06', or the special symbol `!' could become the number `57'. We will use a dictionary to store the mapping between each character and its corresponding en- crypted form. That is, the keys of the dictionary will be the regular characters (letters, numbers and special symbols), and the values will be the encrypted forms of the characters (the two-digit numbers between 00 and 99). Your code should implement the following ve functions for this question. Name: create cypher dictionary Parameters: No parameters. Return value: A dictionary where each key is a regular character and each value is a random two-digit number between 00 and 99, inclusive. What it should do: At the top of the code provided to you, the string LETTERS is dened. This string contains all the letters, numbers and special symbols that should be keys in the dictionary. You will have to loop over this string, and generate a two-digit random number between 00 and 99 for each character. The two-digit numbers will be the values in the dictionary; each character (key) will have one two-digit number (value). Note that the numbers 0, 1, 2, ..., 9 should not be values; instead, they should be the numbers 00, 01, 02, ..., 09. Further, note that each character should have a unique random number. That is, if the character `a' maps to the value `57', no other character should map to the value `57'. (You will need to use some sort of loop to keep generating new random numbers until a unique one is found.) Name: encrypt Parameters: A string s. Return value: The encrypted version of the string s. Each character of the original string s should be replaced by its corresponding two-digit number in the cypher dictionary. Name: decrypt Parameters: A string s. Return value: The decrypted version of the string s. Each two-digit number of the encrypted string s should be replaced by its correponding character in the cypher dictionary. Note that here, we have the encrypted form (value in the dictionary), and are looking to nd the regular character (key 7 in the dictionary). To do this, we will need to use the reverse lookup function as seen in class. This function has been provided to you in the included encryption.py le. We will write two further functions to increase the strength of our encryption. One function will repeatedly encrypt the string multiple times. The other function will attempt to decrypt the string, without knowing the number of times it was encrypted (thus defeating the point of the stronger encryption). Name: encrypt multiple times Parameters: A string s and integer value n for the number of times to encrypt the string. Return value: The string s encrypted n times. I.e., the string will be encrypted a rst time, with each character turned into its two-digit representation. Then, the encrypted string will be re- encrypted, with each digit turned into its two-digit representation. (The length of the string will thus double after every encryption.) (Hint: You will have to call your encrypt function multiple times.) Name: decrypt multiple times Parameters: A string s. Return value: The decrypted version of the string s. As we do not know how many times to decrypt the string, we will keep calling decrypt on the string until the string contains a common word in the English language. A list of common words, COMMON WORDS, has been provided for you in the encryption.py le. If, after decrypting once, the string contains any word in this list, then you should immediately return the decrypted string. Otherwise, continue calling decrypt on the string until it does contain one of the common words. (We will assume that the fully decrypted string will always contain at least one common word.) Finally, at the end of the le encryption.py, you will notice some code already written for you. This code asks the user to input a string, then calls the various functions and prints what they return (to produce the examples seen below). You must alter this code so that if the user enters a string that does not contain any of the words in the COMMON WORDS list, then the program should output "Invalid input." and not execute the rest of the code. Otherwise, the program should continue with the rest of the code. (Hint: Think back to Assignment 1 and if/else branches.) Filename You must write this program in a le called encryption.py. 8 Examples (as executed in Thonny) Example 1: >>> %Run encryption.py Enter text to encrypt: abcdef Invalid input. Example 2: >>> %Run encryption.py Enter text to encrypt: The quick brown fox jumps over the lazy dog. Encrypted string: 0766546138001892056159999714256163973761640073940161973354996 c ,! 169665461919809956156975155 Decrypted string: The quick brown fox jumps over the lazy dog. Encrypted x2 string: 3417626247536227487834342778713634476227477171717117275336 c 476227624871174817622762533434174871533427622771174848475371716227627162624 c 7536227712771783471714762274762711747274747 ,! ,! Decrypted x2 string: The quick brown fox jumps over the lazy dog. Example 3: >>> %Run encryption.py Enter text to encrypt: ,! No, not again. I... why does it say paper jam when there is no paper jam? Encrypted string: 129746612597696198519818255561705555556114669561569754016118696101989561949 c 89454996164987361146654256169665499546118016125976194989454996164987390 ,! ,! Decrypted string: No, not again. I... why does it say paper jam when there is ,! no paper jam? Encrypted x2 string: 273671175362622736477117627162277178472771782778364747476227173447474747474 c 762272753626271476227476271174753342762272778627162273427717871476227715371 c 787153475371716227625371781748622727536262475336476227627162624753717147536 c 2272778342762273647711762277153717871534753717162276253717817487134 ,! ,! ,! ,! Decrypted x2 string: No, not again. I... why does it say paper jam when there ,! is no paper jam? 9![Question 3 [40 points] In cryptography, a simple substitution cypher is a](https://s3.amazonaws.com/si.experts.images/answers/2024/09/66e124690769e_95266e124687223f.jpg)

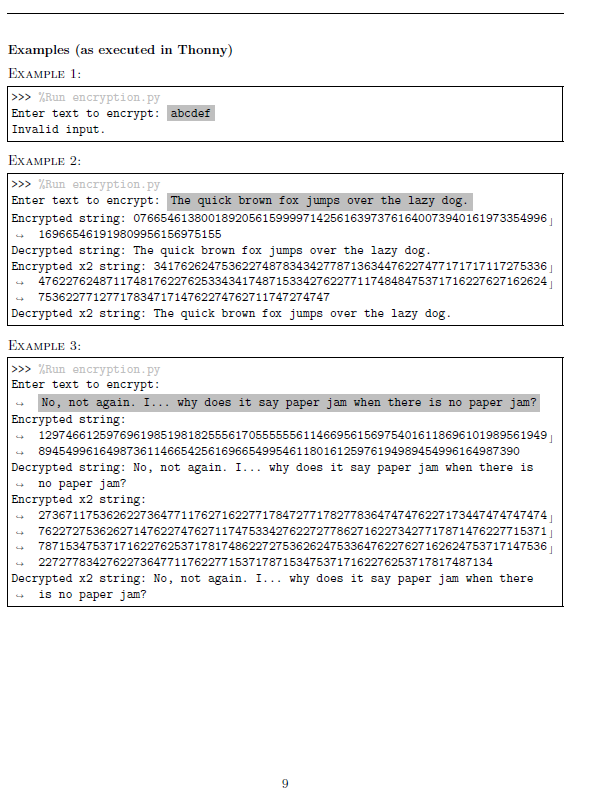
Question 3 (40 points] In cryptography, a simple substitution cypher is a method of encryption in which each letter of a phrase is replaced by a different letter or sequence of letters. The phrase can then be decrypted by performing the inverse of the substitution. In this question, we will implement a simple substitution cypher in which a character (letter, number, or special symbol) is substituted by a two-digit number between 00 and 99 (inclusive). For example, the letter 'a' could be encrypted to become the number '06, or the special symbol ! could become the number 57'. We will use a dictionary to store the mapping between each character and its corresponding en- crypted form. That is, the keys of the dictionary will be the regular characters (letters, numbers and special symbols), and the values will be the encrypted forms of the characters (the two-digit numbers between 00 and 99). Your code should implement the following five functions for this question. Name: create_cypher-dictionary Parameters: No parameters. Return value: A dictionary where each key is a regular character and each value is a random two-digit number between 00 and 99, inclusive. What it should do: At the top of the code provided to you, the string LETTERS is defined. This string contains all the letters, numbers and special symbols that should be keys in the dictionary. You will have to loop over this string, and generate a two-digit random number between 00 and 99 for each character. The two-digit numbers will be the values in the dictionary: each character (key) will have one two-digit number (value). Note that the numbers 0, 1, 2, ..., 9 should not be values; instead, they should be the numbers 00, 01, 02, ..., 09. Further, note that each character should have a unique random number. That is, if the character 'a' maps to the value '57', no other character should map to the value '57'. (You will need to use some sort of loop to keep generating new random numbers until a unique one is found.) Name: encrypt Parameters: A string s. Return value: The encrypted version of the string s. Each character of the original string s should be replaced by its corresponding two-digit number in the cypher dictionary. Name: decrypt Parameters: A string s. Return value: The decrypted version of the string s. Each two-digit number of the encrypted string s should be replaced by its correponding character in the cypher dictionary. Note that here, we have the encrypted form (value in the dictionary), and are looking to find the regular character key in the dictionary). To do this, we will need to use the reverse_lookup function as seen in class. This function has been provided to you in the included encryption.py file. *** We will write two further functions to increase the strength of our encryption. One function will repeatedly encrypt the string multiple times. The other function will attempt to decrypt the string, without knowing the number of times it was encrypted (thus defeating the point of the stronger encryption). Name: encrypt_multiple times Parameters: A string s and integer value n for the number of times to encrypt the string. Return value: The string s encrypted n times. I.e., the string will be encrypted a first time, with each character turned into its two-digit representation. Then, the encrypted string will be re- encrypted, with each digit turned into its two-digit representation. (The length of the string will thus double after every encryption.) (Hint: You will have to call your encrypt function multiple times.) Name: decrypt_multiple times Parameters: A string s. Return value: The decrypted version of the string s. As we do not know how many times to decrypt the string, we will keep calling decrypt on the string until the string contains a common word in the English language. A list of common words, COMMON_WORDS, has been provided for you in the encryption.py file. If, after decrypting once, the string contains any word in this list, then you should immediately return the decrypted string. Otherwise, continue calling decrypt on the string until it does contain one of the common words. (We will assume that the fully decrypted string will always contain at least one common word.) Finally, at the end of the file encryption.py, you will notice some code already written for you. This code asks the user to input a string, then calls the various functions and prints what they return (to produce the examples seen below). You must alter this code so that if the user enters a string that does not contain any of the words in the COMMON_WORDS list, then the program should output "Invalid input." and not execute the rest of the code. Otherwise, the program should continue with the rest of the code. (Hint: Think back to Assignment 1 and if/else branches.) Filename You must write this program in a file called encryption.py. Examples (as executed in Thonny) EXAMPLE 1: >>> Run encryption.py Enter text to encrypt: abcdef Invalid input. EXAMPLE 2: >>>> %Run encryption.py Enter text to encrypt: The quick brown fox jumps over the lazy dog. Encrypted string: 0766546138001892056159999714256163973761640073940161973354996 4 169665461919809956156975155 Decrypted string: The quick brown fox jumps over the lazy dog. Encrypted x2 string: 3417626247536227487834342778713634476227477171717117275336 - 476227624871174817622762533434174871533427622771174848475371716227627162624 4 7536227712771783471714762274762711747274747 Decrypted x2 string: The quick brown fox jumps over the lazy dog. EXAMPLE 3: >>> %Run encryption.py Enter text to encrypt: - No, not again. I... why does it say paper jam when there is no paper jam? Encrypted string: 4 129746612597696198519818255561705555556114669561569754016118696101989561949 4 89454996164987361146654256169665499546118016125976194989454996164987390 Decrypted string: No, not again. I... why does it say paper jam when there is - no paper jam? Encrypted x2 string: 273671175362622736477117627162277178472771782778364747476227173447474747474 - 762272753626271476227476271174753342762272778627162273427717871476227715371] 4 787153475371716227625371781748622727536262475336476227627162624753717147536 - 2272778342762273647711762277153717871534753717162276253717817487134 Decrypted x2 string: No, not again. I... why does it say paper jam when there 4 is no paper jam? Question 3 (40 points] In cryptography, a simple substitution cypher is a method of encryption in which each letter of a phrase is replaced by a different letter or sequence of letters. The phrase can then be decrypted by performing the inverse of the substitution. In this question, we will implement a simple substitution cypher in which a character (letter, number, or special symbol) is substituted by a two-digit number between 00 and 99 (inclusive). For example, the letter 'a' could be encrypted to become the number '06, or the special symbol ! could become the number 57'. We will use a dictionary to store the mapping between each character and its corresponding en- crypted form. That is, the keys of the dictionary will be the regular characters (letters, numbers and special symbols), and the values will be the encrypted forms of the characters (the two-digit numbers between 00 and 99). Your code should implement the following five functions for this question. Name: create_cypher-dictionary Parameters: No parameters. Return value: A dictionary where each key is a regular character and each value is a random two-digit number between 00 and 99, inclusive. What it should do: At the top of the code provided to you, the string LETTERS is defined. This string contains all the letters, numbers and special symbols that should be keys in the dictionary. You will have to loop over this string, and generate a two-digit random number between 00 and 99 for each character. The two-digit numbers will be the values in the dictionary: each character (key) will have one two-digit number (value). Note that the numbers 0, 1, 2, ..., 9 should not be values; instead, they should be the numbers 00, 01, 02, ..., 09. Further, note that each character should have a unique random number. That is, if the character 'a' maps to the value '57', no other character should map to the value '57'. (You will need to use some sort of loop to keep generating new random numbers until a unique one is found.) Name: encrypt Parameters: A string s. Return value: The encrypted version of the string s. Each character of the original string s should be replaced by its corresponding two-digit number in the cypher dictionary. Name: decrypt Parameters: A string s. Return value: The decrypted version of the string s. Each two-digit number of the encrypted string s should be replaced by its correponding character in the cypher dictionary. Note that here, we have the encrypted form (value in the dictionary), and are looking to find the regular character key in the dictionary). To do this, we will need to use the reverse_lookup function as seen in class. This function has been provided to you in the included encryption.py file. *** We will write two further functions to increase the strength of our encryption. One function will repeatedly encrypt the string multiple times. The other function will attempt to decrypt the string, without knowing the number of times it was encrypted (thus defeating the point of the stronger encryption). Name: encrypt_multiple times Parameters: A string s and integer value n for the number of times to encrypt the string. Return value: The string s encrypted n times. I.e., the string will be encrypted a first time, with each character turned into its two-digit representation. Then, the encrypted string will be re- encrypted, with each digit turned into its two-digit representation. (The length of the string will thus double after every encryption.) (Hint: You will have to call your encrypt function multiple times.) Name: decrypt_multiple times Parameters: A string s. Return value: The decrypted version of the string s. As we do not know how many times to decrypt the string, we will keep calling decrypt on the string until the string contains a common word in the English language. A list of common words, COMMON_WORDS, has been provided for you in the encryption.py file. If, after decrypting once, the string contains any word in this list, then you should immediately return the decrypted string. Otherwise, continue calling decrypt on the string until it does contain one of the common words. (We will assume that the fully decrypted string will always contain at least one common word.) Finally, at the end of the file encryption.py, you will notice some code already written for you. This code asks the user to input a string, then calls the various functions and prints what they return (to produce the examples seen below). You must alter this code so that if the user enters a string that does not contain any of the words in the COMMON_WORDS list, then the program should output "Invalid input." and not execute the rest of the code. Otherwise, the program should continue with the rest of the code. (Hint: Think back to Assignment 1 and if/else branches.) Filename You must write this program in a file called encryption.py. Examples (as executed in Thonny) EXAMPLE 1: >>> Run encryption.py Enter text to encrypt: abcdef Invalid input. EXAMPLE 2: >>>> %Run encryption.py Enter text to encrypt: The quick brown fox jumps over the lazy dog. Encrypted string: 0766546138001892056159999714256163973761640073940161973354996 4 169665461919809956156975155 Decrypted string: The quick brown fox jumps over the lazy dog. Encrypted x2 string: 3417626247536227487834342778713634476227477171717117275336 - 476227624871174817622762533434174871533427622771174848475371716227627162624 4 7536227712771783471714762274762711747274747 Decrypted x2 string: The quick brown fox jumps over the lazy dog. EXAMPLE 3: >>> %Run encryption.py Enter text to encrypt: - No, not again. I... why does it say paper jam when there is no paper jam? Encrypted string: 4 129746612597696198519818255561705555556114669561569754016118696101989561949 4 89454996164987361146654256169665499546118016125976194989454996164987390 Decrypted string: No, not again. I... why does it say paper jam when there is - no paper jam? Encrypted x2 string: 273671175362622736477117627162277178472771782778364747476227173447474747474 - 762272753626271476227476271174753342762272778627162273427717871476227715371] 4 787153475371716227625371781748622727536262475336476227627162624753717147536 - 2272778342762273647711762277153717871534753717162276253717817487134 Decrypted x2 string: No, not again. I... why does it say paper jam when there 4 is no paper jam
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


