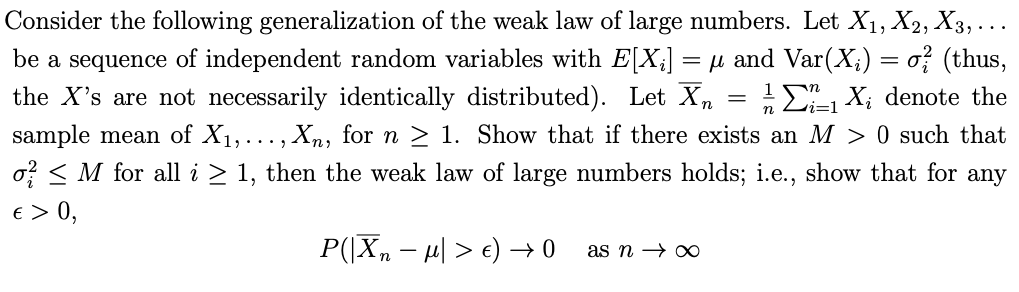
Question
Question: Snort - Network Intrusion Detection & Prevention System Using two computers on the same network that also can see the Internet, set up the
Question:
Snort - Network Intrusion Detection & Prevention System
Using two computers on the same network that also can see the Internet, set up the Snort IDS software on one of these computers. Install Snort, configured to run with several sample rulesets. Your other virtual machine is a Linux computer with NMAP installed which will be used to conduct a port scan against the Windows computer running Snort.
For official documentation, please visit: https://www.snort.org/
For an older video demonstration, please visit: https://www.youtube.com/watch?v=RwWM0srLSg0&t=15s
The following instructions are intended to be general in nature. You may change them as needed to achieve a similar result. You may need to spend considerable time troubleshooting. Do the best you can and submit your outcome. I'm much more interested in your showing me what you can do instead of what you can't do.
Perform the following two exercises. Create Word document and write up these exercises explaining all your steps and presenting screen prints of your command line inputs and outputs.
1. On your Windows VM run Snort with the full set of rules.
On the second computer run a full NMAP scan (-v -A) against the computer running Snort.
Capture all packets generated by this NMAP scan and identify the alerts that were created. In your paper show a couple of the alert text messages.
To run Snort, open a command prompt (cmd) in Administrator mode, change to the C:\Snort\Bin directory (cd\snort\bin) and type the following command, which runs a set of rules from the local.rules file.
snort -i2 -c c:\snort\etc\snort.conf -l c:\snort\log
Allow 15-30 seconds for the program to completely load. You will see numerous warning messages display as Snort starts up. These are normal messages for this project.
After Snort completes its startup, you should see the message "Commencing Packet Processing (Pid=###)"
Note: In the command above, the -I1 (dash eye one) designates the interface number of your virtual machine's network card. The "-l" near the end of the command is a "dash lower case L". Its purpose is to direct the output to a log directory - in this example to c:\snort\log.
Note: In order to use NMAP to scan your Windows/Snort computer you will need to use its IP v4 address. On your Windows computer, open a command prompt and type: ipconfig and make note of the IP v4 address.
On your Linux computer, type:
nmap -v -A ##.###.###.##
Replace the # with the Windows IP address.
To stop Snort, press CTRL/C
The generated log files will be stored in C:\Snort\Log
? To view the "alert.ids" file use NotePad++ ?
To view the "snort.log.####" file use Wireshark.
2. On your Windows VM, run Snort in sniffer mode (no rules folder designated in the command and v switch for verbose to print to screen).
To run snort in sniffer mode, type: snort -v and press [Enter].
As an alternative you could run Wireshark for a period sufficient to see some of the common benign packets that could be expected over a short period of time arriving at this computer (you could also simply surf the web to generate benign packets).
After capturing this traffic for a short period of time, choose two unique packets you saw with the sniffer and craft two rules that would trigger alerts when these benign packets hit the Snort computer.
See Chapter 14 of your textbook for help with local rule options, or visit:
http://www.hackingarticles.in/configuring-snort-rules-beginners-guide/
Be specific in your rules and avoid using generic rules such as "any" and "!" if possible.
In the "local" rules that you craft, insert your name and a description in the title (msg: option) so that it will appear when messages are sent to the alerts.ids file.
Run the configuration for a time sufficient enough to catch several instances of these packets.
For your report, write few sentences about what you did to capture any specific network traffic of your choice. Include command-line syntax, and send your alert.ids file to Blackboard.
report may be a Microsoft Word document (or saved as a pdf), and should include several screen prints.
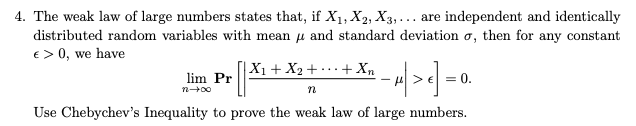

Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


