Answered step by step
Verified Expert Solution
Question
1 Approved Answer
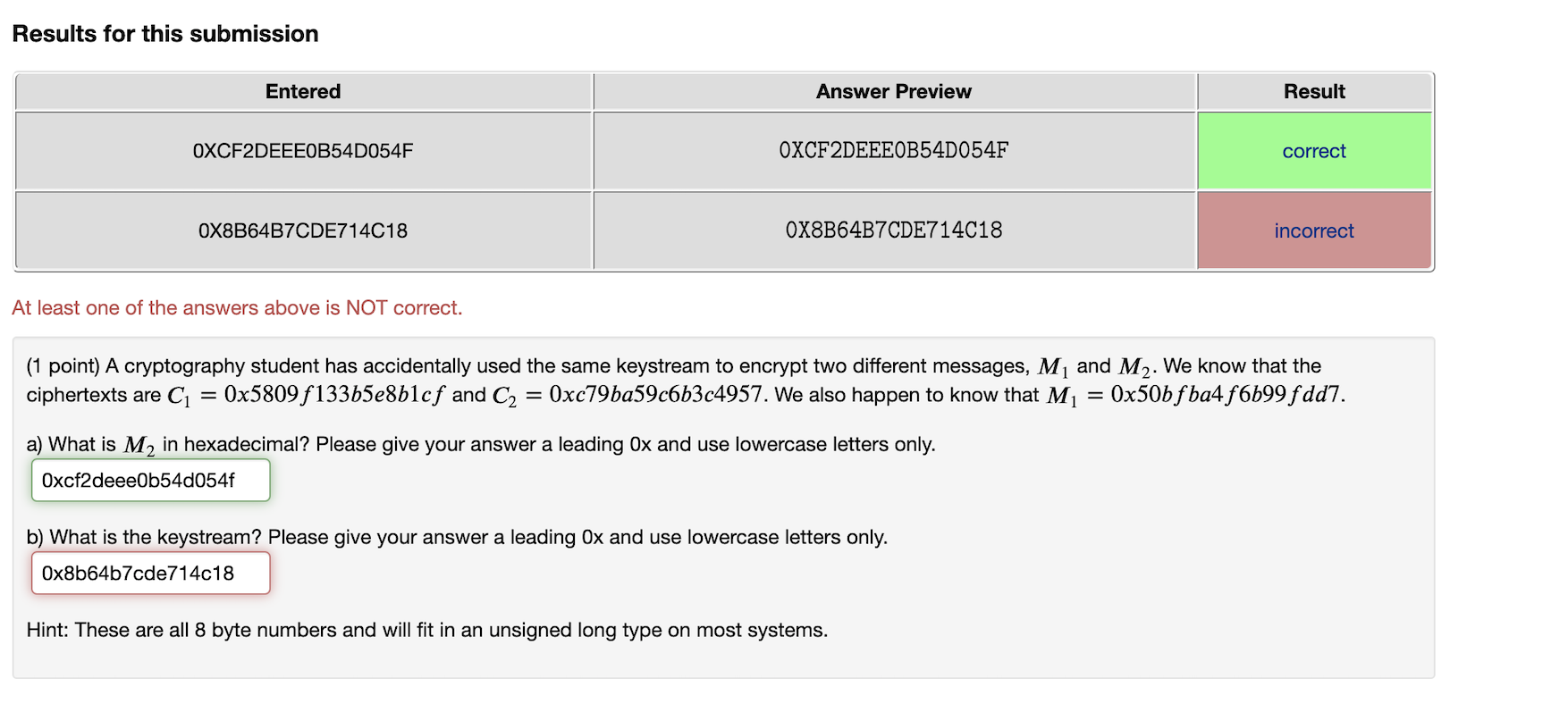
Results for this submission Entered Answer Preview Result OXCF2DEEEOB54D054F OXCF2DEEEOB54D054F correct OX8B64B7CDE714018 OX8B64B7CDE714018 incorrect At least one of the answers above is NOT correct. (1
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


