Answered step by step
Verified Expert Solution
Question
1 Approved Answer
RMF Step 3: Implement In RMF Step 3, Controls specified in the security and privacy plans are implemented. [Cybersecurity Framework: PR.IP-1] In this module we
RMF Step 3: Implement
In RMF Step 3, "Controls specified in the security and privacy plans are implemented." [Cybersecurity Framework: PR.IP-1] In this module we will back up a step to draft the Security Assessment Plan (SAP) to define what testing will be conducted in Step 3.
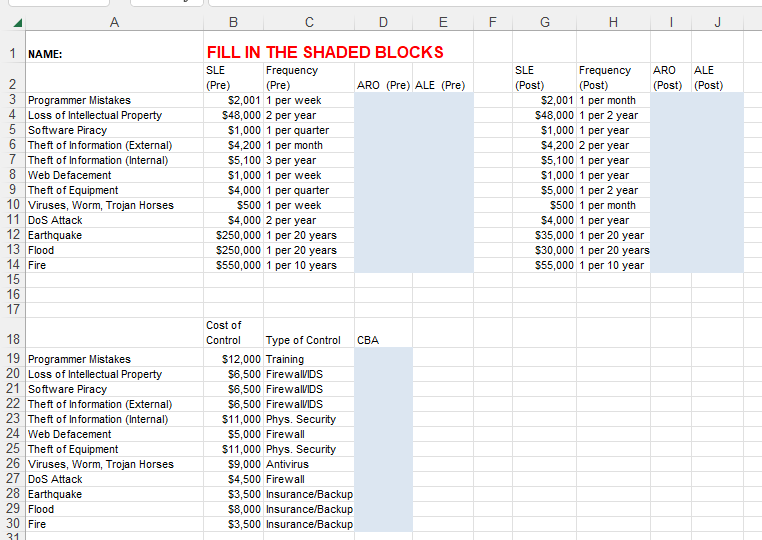
Assignment Requirements
- Download the SAP Template. Part of it has been filled in with the testing you are evaluating in Assignment 6.2.
- Complete the first tab with the information provided in your chosen RMF scenario.
- Based on your systems hardware and software list, use the DISA STIG library to determine which STIGs will be applied in RMF Step 3. Add those to the list on Tab 2.
Submission Requirements
- Format: Microsoft Excel
- Use the assignment link about to submit your spreadsheet
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


