Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Safaricom 17:20 73% sses.docx 1. (2 points) Many banks issue hardware tokens for authenticating their e-banking customers. These hardware tokens require the user to
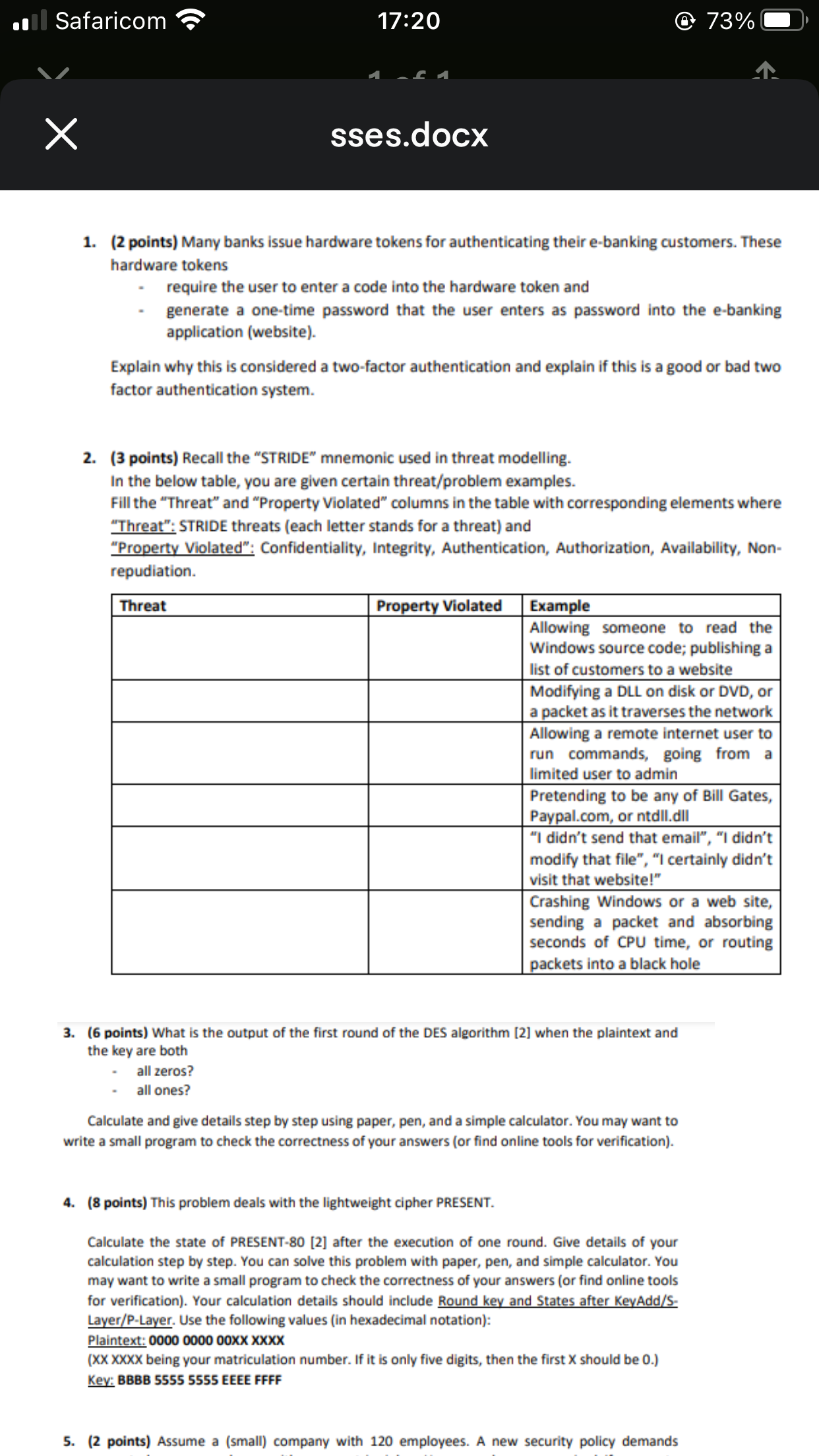
Safaricom 17:20 73% sses.docx 1. (2 points) Many banks issue hardware tokens for authenticating their e-banking customers. These hardware tokens require the user to enter a code into the hardware token and generate a one-time password that the user enters as password into the e-banking application (website). Explain why this is considered a two-factor authentication and explain if this is a good or bad two factor authentication system. 2. (3 points) Recall the "STRIDE" mnemonic used in threat modelling. In the below table, you are given certain threat/problem examples. Fill the "Threat" and "Property Violated" columns in the table with corresponding elements where "Threat": STRIDE threats (each letter stands for a threat) and "Property Violated": Confidentiality, Integrity, Authentication, Authorization, Availability, Non- repudiation. Threat Property Violated Example Allowing someone to read the Windows source code; publishing a list of customers to a website Modifying a DLL on disk or DVD, or a packet as it traverses the network Allowing a remote internet user to run commands, going from a limited user to admin Pretending to be any of Bill Gates, Paypal.com, or ntdll.dll "I didn't send that email", "I didn't modify that file", "I certainly didn't visit that website!" Crashing Windows or a web site, sending a packet and absorbing seconds of CPU time, or routing packets into a black hole 3. (6 points) What is the output of the first round of the DES algorithm [2] when the plaintext and the key are both all zeros? all ones? Calculate and give details step by step using paper, pen, and a simple calculator. You may want to write a small program to check the correctness of your answers (or find online tools for verification). 4. (8 points) This problem deals with the lightweight cipher PRESENT. Calculate the state of PRESENT-80 [2] after the execution of one round. Give details of your calculation step by step. You can solve this problem with paper, pen, and simple calculator. You may want to write a small program to check the correctness of your answers (or find online tools for verification). Your calculation details should include Round key and States after KeyAdd/S- Layer/P-Layer. Use the following values (in hexadecimal notation): Plaintext: 0000 0000 00XX XXXX (XX XXXX being your matriculation number. If it is only five digits, then the first X should be 0.) Key: BBBB 5555 5555 EEEE FFFF 5. (2 points) Assume a (small) company with 120 employees. A new security policy demands
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


