Question
Scenario: Bank of the People allows employees to bring their devices to work and use them in the corporate network. They have a Microsoft identity
Scenario:
Bank of the People allows employees to bring their devices to work and use them in the corporate network. They have a Microsoft identity management system for authentication and authorization. A few employees have noticed in the last few days that the onscreen keyboards they use have become slow. Others report that their emails from g mail seem to include an increased number of phishing attacks.
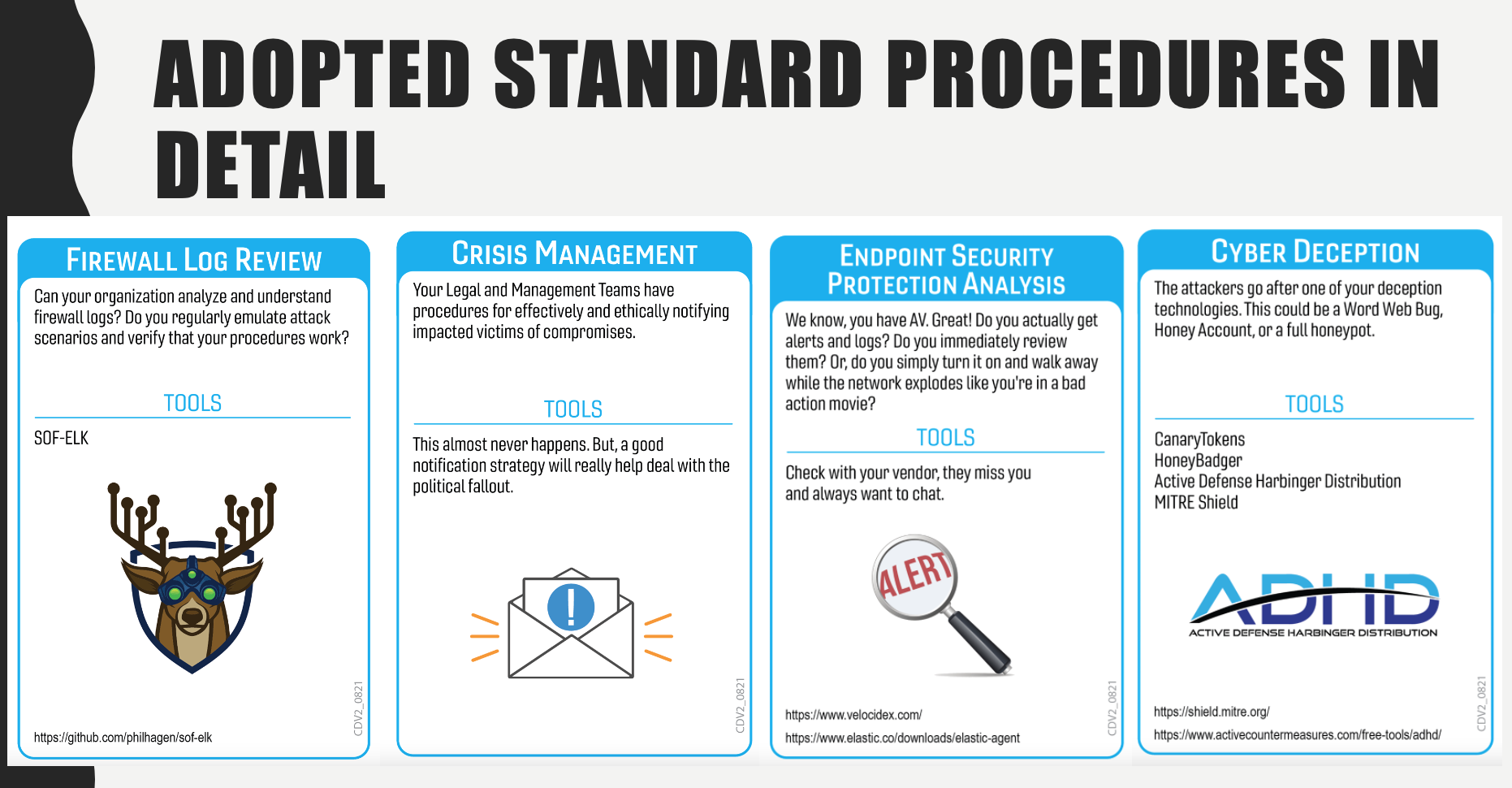
Offer a procedure you recommend to address each. Use at least one non-standard (additional) procedure and explain why is it appropriate.
Initial Compromise
Pivot and Escalation
Command and Control (C2) and Exfiltration
Persistence
Make an estimation and explain what you think happened at each phase. Make a recommendation as to what needs to change in standard procedures as a result of the incident.

Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


