Answered step by step
Verified Expert Solution
Question
1 Approved Answer
See image: Let F : {0, 1} k {0, 1} m {0, 1} n be a secure PRF (pseudorandom function). Consider the following function families:
See image:
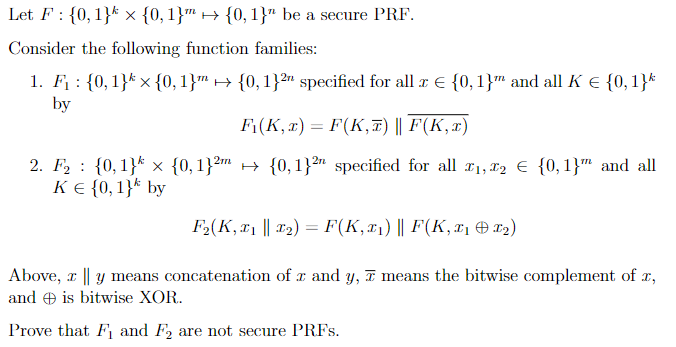
Let F : {0, 1}k {0, 1}m {0, 1}n be a secure PRF (pseudorandom function). Consider the following function families:
1. F1 : {0, 1}k {0, 1}m {0, 1}2n specified for all x {0, 1}m and all K {0, 1}k by
F1(K, x) = F (K, x) F (K, x)
2. F2 : {0, 1}k {0, 1}2m {0, 1}2n specified for all x1, x2 {0, 1}m and all K {0, 1}k by
F2(K, x1 x2) = F (K, x1) F (K, x1 x2)
Above, x y means concatenation of x and y, x means the bitwise complement of x, and is bitwise XOR.
Prove that F1 and F2 are not secure PRFs (pseudorandom functions).
Let F:{0,1}k{0,1}m{0,1}n be a secure PRF. Consider the following function families: 1. F1:{0,1}k{0,1}m{0,1}2n specified for all x{0,1}m and all K{0,1}k by F1(K,x)=F(K,x)F(K,x) 2. F2:{0,1}k{0,1}2m{0,1}2n specified for all x1,x2{0,1}m and all K{0,1}k by F2(K,x1x2)=F(K,x1)F(K,x1x2) Above, xy means concatenation of x and y,x means the bitwise complement of x, and is bitwise XOR. Prove that F1 and F2 are not secure PRFsStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


