Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Simple decryption Problem Statement You come across a dump of secrets that have a very simple eneryption. Each secret is a simple string that contains
Simple decryption
Problem Statement
You come across a dump of secrets that have a very simple eneryption. Each secret is a simple string that contains combination of or less than unique letters from a to without any spaces or special characters.
The encryption scheme is as follows:
In the final encrypted string, each unique letter appears only once, For each subsequent appearance of the letter, it is denoted by the letter's index in the list of unique letters in the string, ordered by its first appearance.
For example if the secret string is doctorstrange, the encrypted string will be doctrsange
For a given encrypted string str you need to crack the code and figure out the original unencrypted string.
Input Format
Input contains a single string str
Constraints
lengthstr
Total number of unique characters in str will be
Output Format
A single string which is the unencrypted version of encrypted string str If the encrypted string is invalid, ie it cannot be a valid encrypted string as per the above encryption schema, the output should be "invalid code"
Sample Input:
doctrsange
Sample Output:
doctorstrange
tableLetterUntque Characters List,CharacteriDiglt,Unenerypted Stringddcharacter,dcharacter,ccharacter,ctcharacter,tdigit,character,
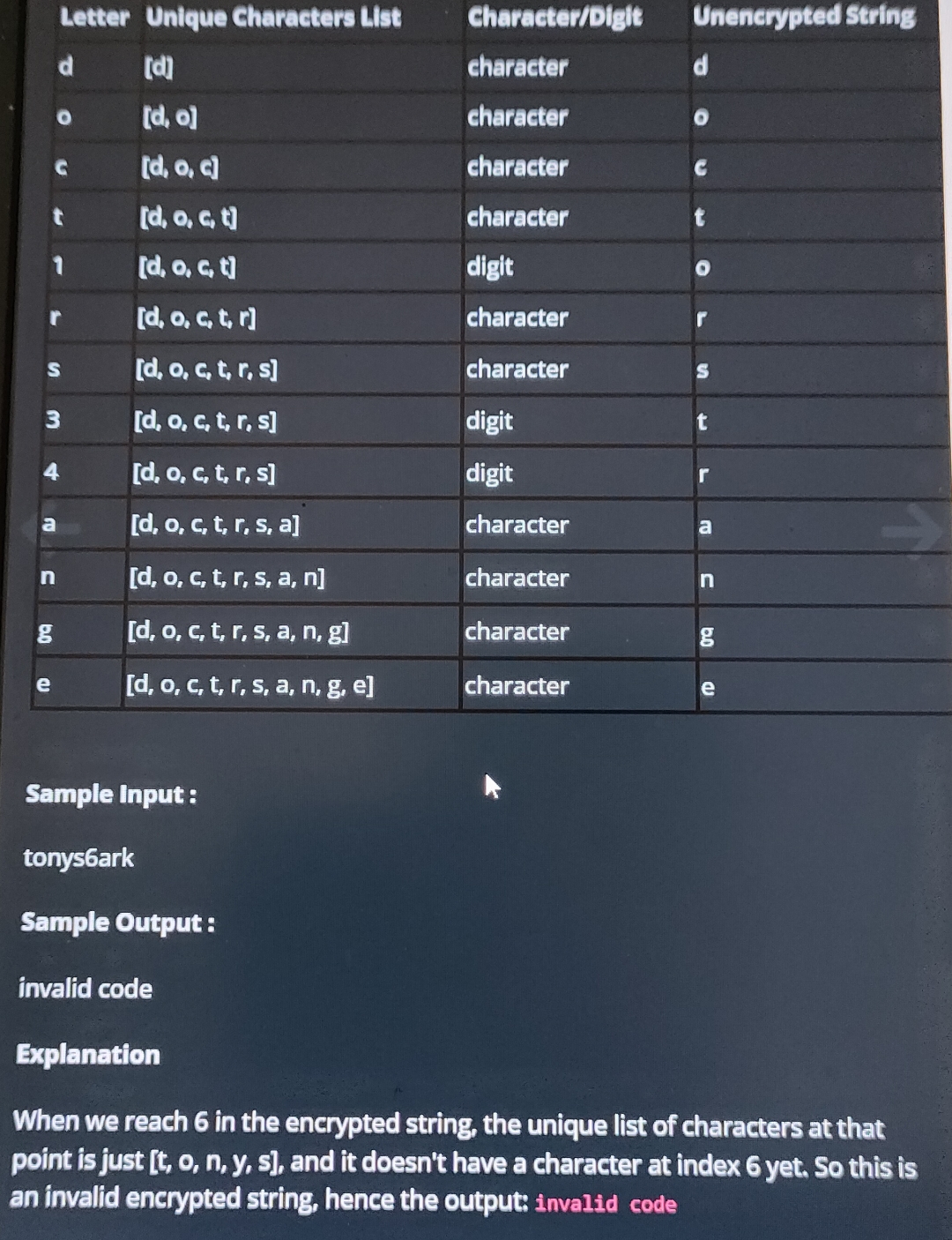
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


