Answered step by step
Verified Expert Solution
Question
1 Approved Answer
solve: begin{tabular}{|c|c|c|c|} hline Scenario & multicolumn{3}{|c|}{begin{tabular}{l} You have recently started work for an engineering design company. They have a small network of computers in
solve: 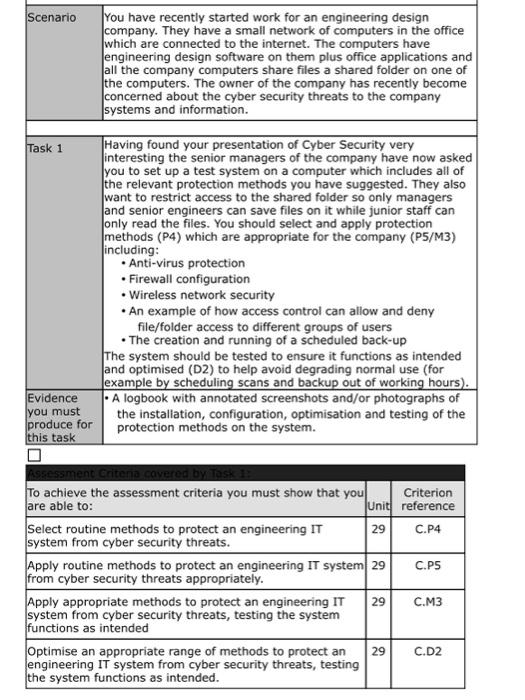
\begin{tabular}{|c|c|c|c|} \hline Scenario & \multicolumn{3}{|c|}{\begin{tabular}{l} You have recently started work for an engineering design \\ company. They have a small network of computers in the office \\ which are connected to the internet. The computers have \\ engineering design software on them plus office applications and \\ all the company computers share files a shared folder on one of \\ the computers. The owner of the company has recently become \\ concerned about the cyber security threats to the company \\ systems and information. \end{tabular}} \\ \hline Task 1 & \multicolumn{3}{|c|}{\begin{tabular}{l} Having found your presentation of Cyber Security very \\ interesting the senior managers of the company have now asked \\ you to set up a test system on a computer which includes all of \\ the relevant protection methods you have suggested. They also \\ want to restrict access to the shared folder so only managers \\ and senior engineers can save files on it while junior staff can \\ only read the files. You should select and apply protection \\ methods (P4) which are appropriate for the company (P5/M3) \\ including: \\ - Anti-virus protection \\ - Firewall configuration \\ - Wireless network security \\ - An example of how access control can allow and deny \\ file/folder access to different groups of users \\ - The creation and running of a scheduled back-up \\ The system should be tested to ensure it functions as intended \\ and optimised (D2) to help avoid degrading normal use (for \\ example by scheduling scans and backup out of working hours). \end{tabular}} \\ \hline \begin{tabular}{l} Evidence \\ you must \\ produce for \\ this task \\ \end{tabular} & \multicolumn{3}{|c|}{\begin{tabular}{l} A logbook with annotated screenshots and/or photographs of \\ the installation, configuration, optimisation and testing of the \\ protection methods on the system. \end{tabular}} \\ \hline \multicolumn{4}{|l|}{} \\ \hline \multicolumn{2}{|c|}{\begin{tabular}{l} To achieve the assessment criteria you must show that you \\ are able to: \end{tabular}} & Unit & \\ \hline \multicolumn{2}{|c|}{\begin{tabular}{l} Select routine methods to protect an engineering IT \\ system from cyber security threats. \end{tabular}} & 29 & C.P4 \\ \hline \multicolumn{2}{|c|}{\begin{tabular}{l} Apply routine methods to protect an engineering IT system \\ from cyber security threats appropriately. \end{tabular}} & 29 & C.PS \\ \hline \multicolumn{2}{|c|}{\begin{tabular}{l} Apply appropriate methods to protect an engineering IT \\ system from cyber security threats, testing the system \\ functions as intended \end{tabular}} & 29 & C.M3 \\ \hline \multicolumn{2}{|c|}{\begin{tabular}{l} Optimise an appropriate range of methods to protect an \\ engineering IT system from cyber security threats, testing \\ the system functions as intended. \end{tabular}} & 29 & C.D2 \\ \hline \end{tabular} 
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


