Question: solve by Understand transport layer protocols TCP/UDP a. Suppose you have the following 2 bytes: 11011100 and 01100101. What is the 1s complement of the
solve by Understand transport layer protocols TCP/UDP
a. Suppose you have the following 2 bytes: 11011100 and 01100101. What is the 1s complement of the sum of these 2 bytes?
b. Suppose you have the following 2 bytes: 10011010 and 01100101. What is the 1s complement of the sum of these 2 bytes?
c. For the bytes in part (a), give an example where one bit is flipped in each of the 2 bytes and yet the 1s complement doesn't change.
d. Suppose that the UDP receiver computes the Internet checksum for the received UDP segment and finds that it matches the value carried in the checksum field. Can the receiver be absolutely certain that no bit errors have occurred? Explain.
Problem 2
a. Are there are any differences between the receiver side of protocol rdt3.0. and the receiver side of protocol rdt2.2? If any, please explain how you will modify the FSM of the receiver side of protocol rdt2.2 to become the FSM of the receiver side of protocol rdt3.0?
b. Please give a trace similar to that used in Figure 3.16, of the operation of protocol rdt3.0 when a data packet is garbled and the acknowledgment for that data packet is garbed as well.
Problem 3
a. Answer true or false to the following questions and briefly justify your answer:
i. With the SR protocol, it is possible for the sender to receive an ACK for a packet that falls outside of its current window.
ii. With GBN, it is possible for the sender to receive an ACK for a packet that falls outside of its current window.
iii. The alternating-bit protocol is the same as the SR protocol with a sender and receiver window size of 1.
iv. The alternating-bit protocol is the same as the GBN protocol with a sender and receiver window size of 1.
b. Why does an application using UDP rather TCP have more control of what data is sent in the segment?
c. Why does an application using UDP rather TCP have more control of when a segment is sent?
Problem 4 Consider transferring an enormous file of L bytes from Host A to Host B. Assume an MSS of 570 bytes.
a. What is the maximum value of L such that TCP sequence numbers are not exhausted? Recall that the TCP sequence number field has four bytes.
b. For the L you obtained in (a), find how long it takes to transmit the file. Assume that a total of 80 bytes of transport, network, and data-link header are added to each segment before the resulting packet is sent out over a 200 Mbps link. Ignore flow control and congestion control so A can pump out the segments back to back and continuously. Note: 1 byte = 8 bits. 1Mbps = 106 bits/sec
Problem 5 Hosts A and B are communicating over a TCP connection, and Host B has already received from Host A all bytes up through byte 145. Suppose Host A then sends two segments to Host B back-to-back. The first and second segments contain 100 and 50 bytes of data respectively. In the first segment, the sequence number is 146, the source port number is 302, and the destination port number is 80. Host B sends an acknowledgment whenever it receives a segment from Host A.
a. In the second segment sent from Host A to B, what are the sequence number, source port number, and destination port number?
b. If the first segment arrives before the second segment, in the acknowledgment of the first arriving segments, what is the ACK number, the source port number, and the destination port number?
c. If the second segment arrives before the first segment, in the ACK of the first arriving segment, what is the ACK number?
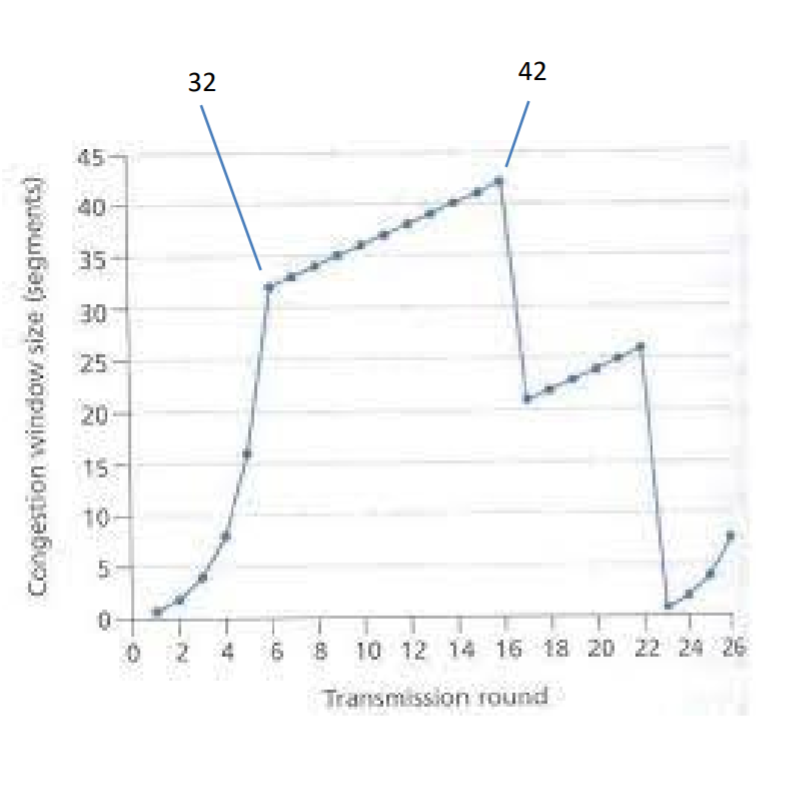
Problem 6 Consider the figure below Assuming TCP Reno is the protocol experiencing the behavior shown in the figure, answer the following question. In all cases, you should provide a short discussion justifying your answer.
a. Identify the intervals of time when TCP slow start is operating.
b. Identify the intervals of time when TCP congestion avoidance is operating.
c. After the 16th transmission round, is segment loss detected by a triple duplicate ACK or by a timeout?
d. After the 22nd transmission round, is segment loss detected by a triple duplicate ACK or by a timeout?
e. What is the initial value of ssthresh at the first transmission round?
CoursHeroTranscribedText
Congestion window size (segments) 5 15 10 5 32 4 42 6 8 10 12 14 16 18 20 22 24 26 Transmission round
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


