Question
solve Data Structures and Algorithms (a) Describe an efficient algorithm to determine whether two finite line segments in a plane intersect. You may assume that
solve
Data Structures and Algorithms (a) Describe an efficient algorithm to determine whether two finite line segments in a plane intersect. You may assume that the end points of each line are given as x-y coordinates. [8 marks] (b) Show that the complexity of the Graham scan used in the algorithm is O(n) and that the algorithm as a whole has complexity O(n log n). [8 marks] (c) Discuss how it is possible to eliminate many of the points before the convex hull algorithm is entered. [4 marks] 2 Computer Design The ARM processor allows the second operand to be shifted by an arbitrary amount. In order to improve the performance, a six-stage pipeline is proposed with the following stages: instruction decode and shift execute memory register fetch register fetch operand 2 access write back (a) What are control hazards and how could they be resolved in the above pipeline? [4 marks] (b) What are data hazards and how could they be resolved in the above pipeline? [4 marks] (c) What are feed-forward paths and where could they be added to the above pipeline to improve performance? [6 marks] (d) Why might a branch instruction result in pipeline bubbles and how many bubbles will appear in the above pipeline as a result of taking a branch instruction? [6 marks] 2 CST.2004.13.3 3 Digital Communication I (a) Define the terms latency and capacity as applied to communication channels. [2 marks] (b) Is there a strict relation between the two? [1 mark] (c) Show how the latency of a channel can have a direct effect on the capacity of a higher-layer channel which uses it. [10 marks] (d) How can the capacity of the higher-layer channel be improved (keeping the characteristics of the underlying channel unchanged)? [4 marks] (e) In what circumstances might these improvements have only limited benefit? [3 marks] 3 [TURN OVER CST.2004.13.4 4 Distributed Systems A network-based service manages persistent objects. The service must enforce an access control policy to protect the objects. (a) Discuss how this access control might best be implemented for the following example of objects and policy components: Objects: Files in a University Department's file service, operating behind a firewall. Policy: The owner may specify read, write and execute rights in terms of principals and groups. [4 marks] (b) Discuss how this access control might best be implemented for two of the following examples: (i) Objects: Files in a commercial, distributed, Internet-based file service. Policy: The owner may authorise other principals to download the file. (ii) Objects: Sales data relating to a company. Policy: Those employed in the Sales Departments of all branches of the company worldwide may read the data. (iii) Objects: Electronic health records (EHRs) in a nationwide service. Policy: The owner (patient) may read from its own EHR. A qualified and employed doctor may read and write the EHR of a patient registered with him/her. (iv) Object: The solution to online coursework. Policy: The coursework setter has read and write access. A candidate has no access until after the marks have been published. [8 marks each] 4 CST.2004.13.5 5 Computer Graphics and Image Processing (a) Explain why display devices appear to be able to reproduce (almost) all the colours of the spectrum using only red, green and blue light. [4 marks] (b) Describe an algorithm (other than thresholding) which will convert a greyscale image (8 bits per pixel) to a bi-level black and white image (1 bit per pixel), with the same number of pixels, while retaining as much detail as possible. [8 marks] (c) Explain what specular and diffuse reflection are in the real world. State and explain equations for calculating approximations to both in a computer. [8 marks] 5 [TURN OVER CST.2004.13.6 6 Compiler Construction (a) Explain the differences (illustrating each with a small program) between (i) static and dynamic binding (scoping); [4 marks] (ii) static and dynamic typing. [2 marks] (b) Java is sometimes said to be "dynamically typed" in that a variable whose type is (class) C can be assigned a value of (class) D provided that D extends C; conversely a variable of type D can be assigned a value of type C using a cast. By considering storage layouts, explain why the former assignment is always valid and the latter sometimes invalid. [4 marks] (c) A new programming language has the notion of "statically scoped exceptions" in which the program exception foo; void f() { try { void g() { raise foo; } try { g(); } except (foo) { C2 } } except (foo) { C1 } } would execute C1 rather than C2 as the former was in scope at the raise point. By analogy with statically scoped variables, or otherwise, explain how such exceptions might be implemented on a stack. [10 marks] 6 CST.2004.13.7 7 Artificial Intelligence In the following, N is a feedforward neural network architecture taking a vector x T = ( x1 x2 xn ) of n inputs. The complete collection of weights for the network is denoted w and the output produced by the network when applied to input x using weights w is denoted N(w, x). The number of outputs is arbitrary. We have a sequence s of m labelled training examples s = ((x1, l1),(x2, l2), . . . ,(xm, lm)) where the li denote vectors of desired outputs. Let E(w; (xi , li)) denote some measure of the error that N makes when applied to the ith labelled training example. Assuming that each node in the network computes a weighted summation of its inputs, followed by an activation function, such that the node j in the network computes a function g w (j) 0 + X k i=1 w (j) i input(i) ! of its k inputs, where g is some activation function, derive in full the backpropagation algorithm for calculating the gradient ?E ?w = ?E ?w1 ?E ?w2 ?E ?wW T for the ith labelled example, where w1, . . . , wW denotes the complete collection of W weights in the network. [20 marks] 7 [TURN OVER CST.2004.13.8 8 Databases (a) Define the operators of the core relational algebra. [5 marks] (b) Let R be a relation with schema (A1, . . . , An, B1, . . . , Bm) and S be a relation with schema (B1, . . . , Bm). The quotient of R and S, written R S, is the set of tuples t over attributes (A1, . . . , An) such that for every tuple s in S, the tuple ts (i.e. the concatenation of tuples t and s) is a member of R. Define the quotient operator using the operators of the core relational algebra. [8 marks] (c

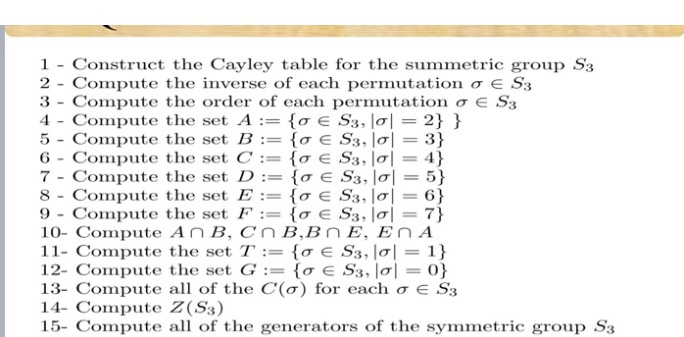
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


