
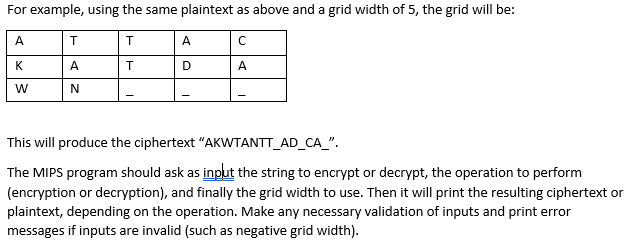
Solve first in CH than design and implement a MIPS program in MARS MIPS simulator, that performs primitive encryption and decryption of text using simple columnar transposition. Text is assumed to be in ASCII, using 1 byte per character. With this algorithm, the unencrypted text known as the plaintext) is written horizontally onto a grid of fixed width, and the encrypted text known as the ciphertext) is read off vertically. Decryption is a matter of writing the ciphertext vertically onto a grid of identical width and then reading the plaintext off horizontally. The grid height is equal to the number of letters divided by the number of columns. The grid width, i.e. the number of columns, is a parameter to this algorithm and represents the secret shared between the two people communicating securely. As an example, if the plaintext is "ATTACKATDAWN" and the grid width of 4, it is written as follows: AWN Reading it vertically will yield the ciphertext "ACDTKATAWATN". To decrypt it, it will have to be written vertically into the same grid (height = 12/4= 3) and read horizontally, to come up with the original plaintext. The above example assumes that the length of 12 characters is an exact multiple of 4, so that a rectangle is perfectly formed. If this is not the case during encryption, the remaining empty cells are filled with random text called "padding". For this task you will use underscores "_" as padding characters. During decryption, the ciphertext length is always an exact multiple of the grid width, otherwise it is considered an error. For example, using the same plaintext as above and a grid width of 5, the grid will be: | A | | K A T D A W NTT This will produce the ciphertext "AKWTANTT_AD_CA_". The MIPS program should ask as input the string to encrypt or decrypt, the operation to perform (encryption or decryption), and finally the grid width to use. Then it will print the resulting ciphertext or plaintext, depending on the operation. Make any necessary validation of inputs and print error messages if inputs are invalid (such as negative grid width). Solve first in CH than design and implement a MIPS program in MARS MIPS simulator, that performs primitive encryption and decryption of text using simple columnar transposition. Text is assumed to be in ASCII, using 1 byte per character. With this algorithm, the unencrypted text known as the plaintext) is written horizontally onto a grid of fixed width, and the encrypted text known as the ciphertext) is read off vertically. Decryption is a matter of writing the ciphertext vertically onto a grid of identical width and then reading the plaintext off horizontally. The grid height is equal to the number of letters divided by the number of columns. The grid width, i.e. the number of columns, is a parameter to this algorithm and represents the secret shared between the two people communicating securely. As an example, if the plaintext is "ATTACKATDAWN" and the grid width of 4, it is written as follows: AWN Reading it vertically will yield the ciphertext "ACDTKATAWATN". To decrypt it, it will have to be written vertically into the same grid (height = 12/4= 3) and read horizontally, to come up with the original plaintext. The above example assumes that the length of 12 characters is an exact multiple of 4, so that a rectangle is perfectly formed. If this is not the case during encryption, the remaining empty cells are filled with random text called "padding". For this task you will use underscores "_" as padding characters. During decryption, the ciphertext length is always an exact multiple of the grid width, otherwise it is considered an error. For example, using the same plaintext as above and a grid width of 5, the grid will be: | A | | K A T D A W NTT This will produce the ciphertext "AKWTANTT_AD_CA_". The MIPS program should ask as input the string to encrypt or decrypt, the operation to perform (encryption or decryption), and finally the grid width to use. Then it will print the resulting ciphertext or plaintext, depending on the operation. Make any necessary validation of inputs and print error messages if inputs are invalid (such as negative grid width)








