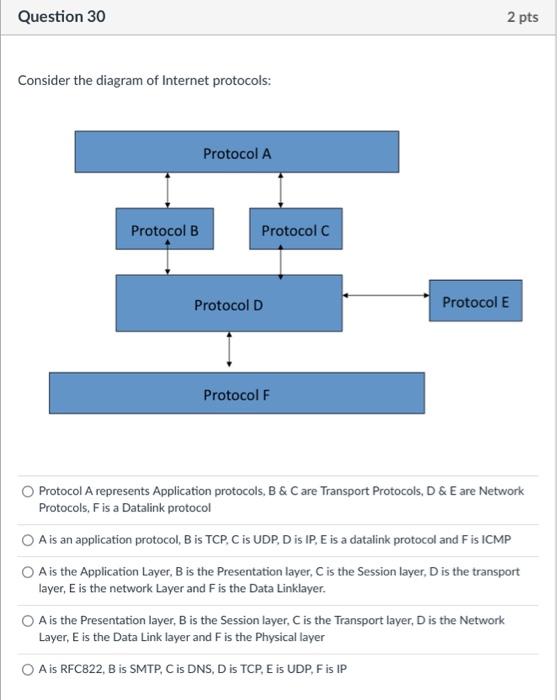
TCP uses a 3 way handshake to implement a connection open. Which best describes this process? The TCP open involves three computers, the client, the server and the router. The TCP open involves three steps, the request to open (SYN) the reply (ACK, SYN) and the final acknowledgement (ACK) which enable both parties to establish the sequence numbering to be used. The TCP open involves three steps, the request to open (SYN), the Acknowledgement (ACK) and the end of open (FIN). The TCP open involves three steps which require the Application layer, the Transport Layer and the Network Layer. The TCP open involves the three protocols TCP, UDP and IP. A UDP datagram contains a 16 bit checksum value. This checksum is used for: The checksum is ignored as UDP is an unreliable delivery method so no checksum is required The checksum validates that the whole UDP datagram has not been corrupted before delivery The checksum validates that the UDP datagram header has not been corrupted before delivery The checksum validates the UDP source and destination fields have not been corrupted before delivery There is no checksum in a UDP datagram; its a trick question Explain, in your own words, how the traceroute (or Tracert on windows) command works, ensuring you reference the features of the IP protocol that are used by the tool. Networks can be connected by different kinds of boxes, known as repeaters, bridges, routers, relays and gateways. Which of the following best describes how they differ? The size of the box indicates which kind of interconnection it is. Larger boxes have more functionality and are higher up the ISO layered model, (for example a gateway) whereas smaller boxes have less functionality (for example a repeater). The higher layer interconnection boxes contain more software and are thus able to operate at higher speeds than pure electrical switches such as repeaters. You should select the interconnect that operates at the correct performance for your network. Routers are not used in the home but are purely used on the main internet backbones. The size of the network is determined by the nature of the interconnection, with the repeater having limitations to the length of cable and number of nodes it can support. Interconnections for physical layers occur under the floor, which is why computer rooms have false floors. Application level gateways operate at a higher level and are thus located at the top of the machine cabinets. Consider the diagram of Internet protocols: Protocol A represents Application protocols, B \& C are Transport Protocols, D \& E are Network Protocols, F is a Datalink protocol A is an application protocol, B is TCP, C is UDP, D is IP, E is a datalink protocol and F is ICMP A is the Application Layer, B is the Presentation layer, C is the Session layer, D is the transport layer, E is the network Layer and F is the Data Linklayer. A is the Presentation layer, B is the Session layer, C is the Transport layer, D is the Network Layer, E is the Data Link layer and F is the Physical layer A is RFC822, B is SMTP, C is DNS, D is TCP, E is UDP, F is IP