Answered step by step
Verified Expert Solution
Question
1 Approved Answer
The CISO of a company wishes to create hybrid cryptosystem using RSA and DES. All employees have a private-public key pair ( d - the
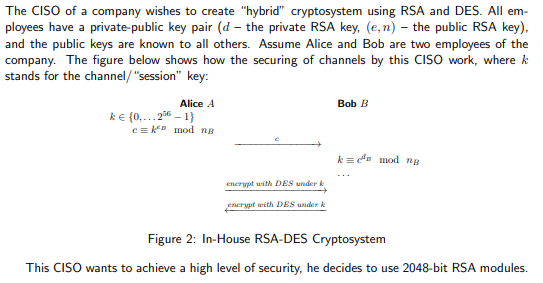

The CISO of a company wishes to create "hybrid" cryptosystem using RSA and DES. All employees have a private-public key pair ( d - the private RSA key, (e,n) - the public RSA key), and the public keys are known to all others. Assume Alice and Bob are two employees of the company. The figure below shows how the securing of channels by this CISO work, where k stands for the channel/ "session" key: Figure 2: In-House RSA-DES Cryptosystem This CISO wants to achieve a high level of security, he decides to use 2048-bit RSA modules. 4. Let k be the DES key chosen by Alice (considered as 56 bit integer), and consider it be written as k=k1k2 where k1 and k2 are two integers of 28 bits. Eve decides to store in a table T[.]thevalueofT[k1]=k1eBmodnB, for each value possible of k1 as per the above, i.e., k1 of of 28 bits. Explain how Eve, who knows/gets Alice's fixed c=k1eBk2eBmodnB (as per the specs of the system), can mount an attack (with this table) in order to recover k. 5. What is the number of modular exponentiations required to calculate the table? What is the size of table ? Once the table is calculated, how many modular exponentiations are necessary to recover the key? 6. In order to reduce the memory-space use, Eve decides to use a hash function h. Consequently, instead of storing the value of k1eBmodnB, she now stores h(k1eBmodnB). What is the size of this new table if the hash function is MD5? At how many collision(s) should she expect? 7. In order to thwart the attack, the CISO suggests using only prime numbers for DES keys, so that it is not possible to find two factors such that k=klk2. Calculate the approximate number of DES keys that satisfy this condition. What are the time and space complexities of an attack by on this schema? 8. Obviously, the system by this CISO is not very well designed. Design something in the same spirit but better
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


