

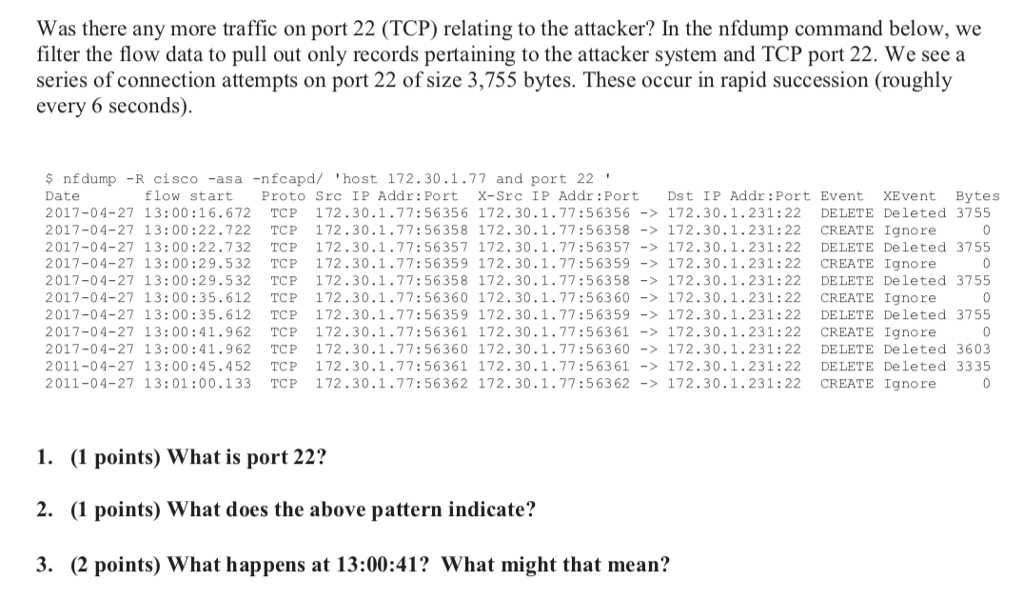
The Curious Mr. X The Case: While a fugitive in Mexico, Mr. X remotely infiltrates the Arctic Nuclear Fusion Research Facility (ANFRF) lab network over the Internet. Sadly, Mr. X is not yet very stealthy Unfortunately for Mr. X, the ANFRF network is instrumented to capture flow record data. Security staff notice port scanning from his external IP address, 172.30.1.77, beginning at 12:51:46 in the Cisco ASA flow record logs. His activities are discovered and analyzed - by you! Challenge: You are the forensic investigator. Your mission is to: Identify any compromised systems Determine what the attacker found out about the network architecture Evaluate the risk of data exfiltration Since the Arctic Nuclear Fusion Research Facility stores a lot of confidential information, management is highly concerned about the risk of data exfiltration. If you find suspicious traffic, provide an analysis of the risk that Secret Information was compromised. Be sure to carefully justify your conclusions Network: The Arctic Nuclear Fusion Research Facility network consists of three segments Internal network: 192.168.30.0/24 DMZ: 10.30.30.0/24 The "Internet": 172.30.1.0/24 Note that for the purposes of this lab, we are treating the 172.30.1.0/24 subnet as "the Internet" In real life, this is a reserved non-routable IP address space.] Evidence: Security staff at ANFRF collects network flow data from a Cisco ASA switch/firewall that connects all three subnets at the perimeter. The flow record data is exported in Cisco's NetFlow v9 format to a collector running nfcapd. In addition, the Cisco ASA is also configured with a SPAN port that monitors the Internal and DMZ subnets. There is an Argus listener connected to the SPAN port, which retains flow record data in Argus format from the two subnets (192.168.30.0/24 and 10.30.30.0/24). The data you are provided came from two files cisco-asa-nfcapd.zip-A zip archive containing flow records from the perimeter Cisco ASA, stored by the nfdump collector utility (nfcapd) in 5-minute increments argus-collector.ra -An Argus archive containing flow record data collected from the Internal and DMZ subnets via a SPAN port. Note: As you will see in the flow record data, there is a time skew of approximately 8 seconds between the Cisco ASA and the Argus listener. In addition, be aware that Network Address Translation (NAT) is used on this network. The DMZ IP The Curious Mr. X The Case: While a fugitive in Mexico, Mr. X remotely infiltrates the Arctic Nuclear Fusion Research Facility (ANFRF) lab network over the Internet. Sadly, Mr. X is not yet very stealthy Unfortunately for Mr. X, the ANFRF network is instrumented to capture flow record data. Security staff notice port scanning from his external IP address, 172.30.1.77, beginning at 12:51:46 in the Cisco ASA flow record logs. His activities are discovered and analyzed - by you! Challenge: You are the forensic investigator. Your mission is to: Identify any compromised systems Determine what the attacker found out about the network architecture Evaluate the risk of data exfiltration Since the Arctic Nuclear Fusion Research Facility stores a lot of confidential information, management is highly concerned about the risk of data exfiltration. If you find suspicious traffic, provide an analysis of the risk that Secret Information was compromised. Be sure to carefully justify your conclusions Network: The Arctic Nuclear Fusion Research Facility network consists of three segments Internal network: 192.168.30.0/24 DMZ: 10.30.30.0/24 The "Internet": 172.30.1.0/24 Note that for the purposes of this lab, we are treating the 172.30.1.0/24 subnet as "the Internet" In real life, this is a reserved non-routable IP address space.] Evidence: Security staff at ANFRF collects network flow data from a Cisco ASA switch/firewall that connects all three subnets at the perimeter. The flow record data is exported in Cisco's NetFlow v9 format to a collector running nfcapd. In addition, the Cisco ASA is also configured with a SPAN port that monitors the Internal and DMZ subnets. There is an Argus listener connected to the SPAN port, which retains flow record data in Argus format from the two subnets (192.168.30.0/24 and 10.30.30.0/24). The data you are provided came from two files cisco-asa-nfcapd.zip-A zip archive containing flow records from the perimeter Cisco ASA, stored by the nfdump collector utility (nfcapd) in 5-minute increments argus-collector.ra -An Argus archive containing flow record data collected from the Internal and DMZ subnets via a SPAN port. Note: As you will see in the flow record data, there is a time skew of approximately 8 seconds between the Cisco ASA and the Argus listener. In addition, be aware that Network Address Translation (NAT) is used on this network. The DMZ IP









