








- The current state of the VPN connectivity available at CHI
- Assessment of how important VPN connectivity is to the future of CHI
- Include one paragraph to articulate your current level of technical ability (actual not simulated) in designing, installing, configuring, and using VPN technology.
- Please help me!
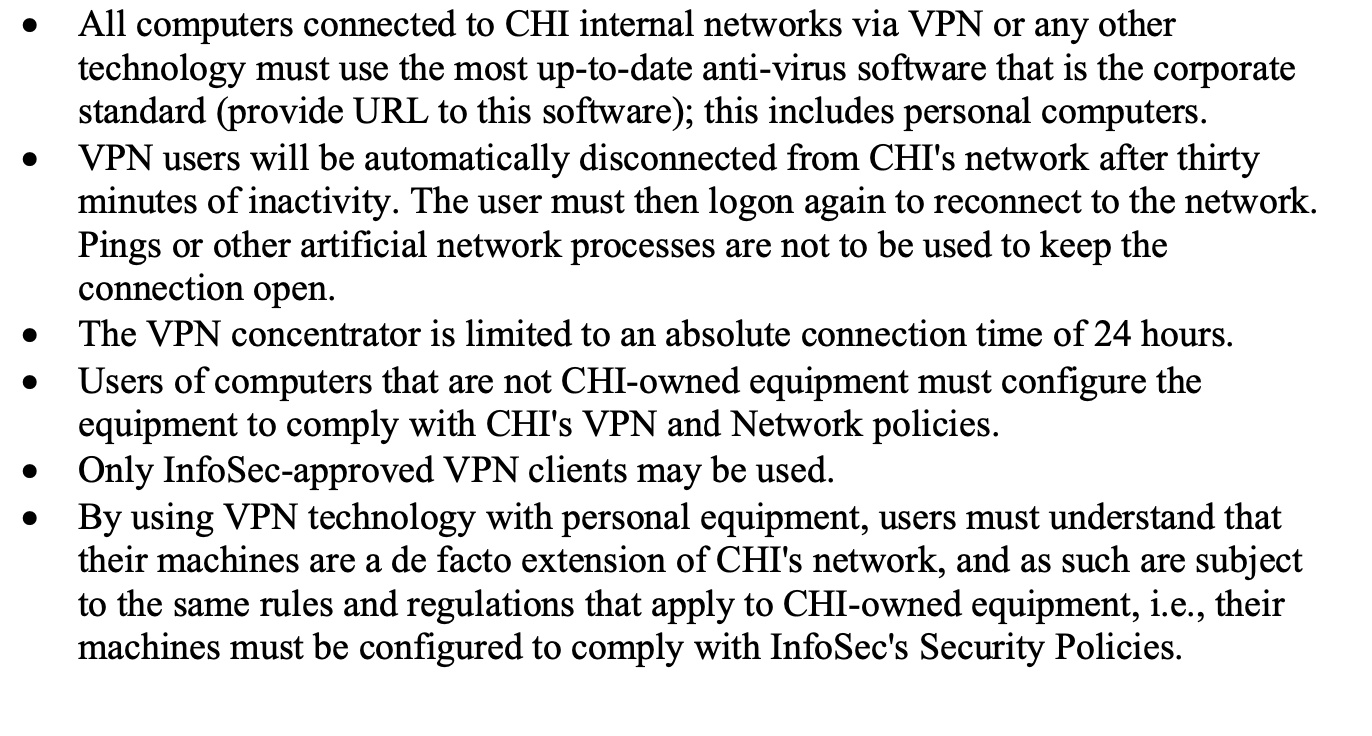
Information Security Roles & Responsibilities: Consolidated Holdings technology resources will proactively track threat activity and work to prohibit or correct such activity. Where unintentional unauthorized access is detected, the affected organization will be advised to correct exploitable vulnerabilities to prevent future occurrences. Where unauthorized access is determined to be intentional it will be assumed to be malicious and an appropriate response will be initiated. All Consolidated Holdings faculty members, staff, students, contractors, agents or other individuals utilizing computer resources, data communication networks, or other information technology infrastructure resources owned or leased by Consolidated Holdings, including any other state agencies having electrical connectivity to the network are subject to this policy. Additionally, any remote access, such as dial up connections, personal Internet Service Provider access or VPN connection, onto the Consolidated Holdings enterprise network or associated domains will have the same effect as direct access via CHI provided equipment or facilities. Virtual Private Network (VPN) Policy 1.0 Purpose The purpose of this policy is to provide guidelines for Remote Access IPSec or L2TP Virtual Private Network (VPN) connections to the CHI corporate network. 2.0 Scope This policy applies to all CHI employees, contractors, consultants, temporaries, and other workers including all personnel affiliated with third parties utilizing VPNs to access the CHI network. This policy applies to implementations of VPN that are directed through an IPSec Concentrator. 3.0 Policy Approved CHI employees and authorized third parties (customers, vendors, etc.) may utilize the benefits of VPNs, which are a "user managed" service. This means that the user is responsible for selecting an Internet Service Provider (ISP), coordinating installation, installing any required software, and paying associated fees. Further details may be found in the Remote Access Policy. Additionally It is the responsibility of employees with VPN privileges to ensure that unauthorized users are not allowed access to CHI internal networks. VPN use is to be controlled using either a one-time password authentication such as a token device or a public/private key system with a strong passphrase. When actively connected to the corporate network, VPNs will force all traffic to and from the PC over the VPN tunnel: all other traffic will be dropped. Dual (split) tunneling is NOT permitted; only one network connection is allowed. VPN gateways will be set up and managed by CHI network operational groups. All computers connected to CHI internal networks via VPN or any other technology must use the most up-to-date anti-virus software that is the corporate standard (provide URL to this software); this includes personal computers. VPN users will be automatically disconnected from CHI's network after thirty minutes of inactivity. The user must then logon again to reconnect to the network. Pings or other artificial network processes are not to be used to keep the connection open. The VPN concentrator is limited to an absolute connection time of 24 hours. Users of computers that are not CHI-owned equipment must configure the equipment to comply with CHI's VPN and Network policies. Only InfoSec-approved VPN clients may be used. By using VPN technology with personal equipment, users must understand that their machines are a de facto extension of CHI's network, and as such are subject to the same rules and regulations that apply to CHI-owned equipment, i.e., their machines must be configured to comply with InfoSec's Security Policies. 4.0 Enforcement Any employee found to be in violation this policy may be subject to disciplinary action, up to and including termination of employment. 5.0 Definitions Term IPSec Concentrator Definition A device in which VPN connections are terminated. 6.0 Revision History Remote Access: 1.0 Purpose The purpose of this policy is to define standards for connecting to CHI's network from any host. These standards are designed to minimize the potential exposure to CHI from damages which may result from unauthorized use of CHI resources. Damages include the loss of sensitive or company confidential data, intellectual property, damage to public image, damage to critical CHI internal systems, etc. 2.0 Scope This policy applies to all CHI employees, contractors, vendors and agents with a CHI- owned or personally-owned computer or workstation used to connect to the CHI network. This policy applies to remote access connections used to do work on behalf of CHI, including reading or sending email and viewing intranet web resources. Remote access implementations that are covered by this policy include, but are not limited to, dial-in modems, frame relay, ISDN, DSL, VPN, SSH, and cable modems, etc. 3.0 Policy 3.1 General It is the responsibility of CHI employees, contractors, vendors and agents with remote access privileges to CHI's corporate network to ensure that their remote access connection is given the same consideration as the user's on-site connection to CHI. General access to the Internet for recreational use by immediate household members through the CHI Network on personal computers is permitted for employees that have flat-rate services. The CHI employee is responsible to ensure the family member does not violate any CHI policies, does not perform illegal activities, and does not use the access for outside business interests. The CHI employee bears responsibility for the consequences should the access be misused. Please review the following policies for details of protecting information when accessing the corporate network via remote access methods, and acceptable use of CHI's network: Acceptable Encryption Policy Virtual Private Network (VPN) Policy 16 Wireless Communications Policy Acceptable Use Policy For additional information regarding CHI's remote access connection options, including how to order or disconnect service, cost comparisons, troubleshooting, etc., go to the Remote Access Services website. 3.2 Requirements Secure remote access must be strictly controlled. Control will be enforced via one- time password authentication or public/private keys with strong pass-phrases. For information on creating a strong pass-phrase see the Password Policy. At no time should any CHI employee provide their login or email password to anyone, not even family members. CHI employees and contractors with remote access privileges must ensure that their CHI-owned or personal computer or workstation, which is remotely connected to CHI's corporate network, is not connected to any other network at the same time, with the exception of personal networks that are under the complete control of the user. CHI employees and contractors with remote access privileges to CHI's corporate network must not use non-CHI email accounts (i.e., Hotmail, Yahoo, AOL), or other external resources to conduct CHI business, thereby ensuring that official business is never confused with personal business. Routers for dedicated ISDN lines configured for access to the CHI network must meet minimum authentication requirements of CHAP. Reconfiguration of a home user's equipment for the purpose of split-tunneling or dual homing is not permitted at any time. Frame Relay must meet minimum authentication requirements of DLCI standards. Non-standard hardware configurations must be approved by Remote Access Services, and InfoSec must approve security configurations for access to hardware. All hosts that are connected to CHI internal networks via remote access technologies must use the most up-to-date anti-virus software (place url to corporate software site here), this includes personal computers. Third party connections must comply with requirements as stated in the Third Party Agreement. nal equipment that is used to connect to CHI's networks must meet the requirements of CHI-owned equipment for remote access. Organizations or individuals who wish to implement non-standard Remote Access solutions to the CHI production network must obtain prior approval from Remote Access Services and InfoSec. 4.0 Enforcement Any employee found to be in violation this policy may be subject to disciplinary action, up to and including termination of employment. 5.0 Definitions Term Cable Modem Definition Cable companies such as AT&T Broadband provide Internet access over Cable TV coaxial cable. A cable modem accepts this coaxial cable and can receive data from the Internet at over 1.5 Mbps. Cable CHAP Dial-in Modem Dual Homing is currently available only in certain communities. Challenge Handshake Authentication Protocol is an authentication method that uses a one-way hashing function. DLCIData Link Connection Identifier (DLCI) is a unique number assigned to a Permanent Virtual Circuit (PVC) end point in a frame relay network. DLCI identifies a particular PVC endpoint within a user's access channel in a frame relay network, and has local significance only to that channel. A peripheral device that connects computers to each other for sending communications via the telephone lines. The modem modulates the digital data of computers into analog signals to send over the telephone lines, then demodulates back into digital signals to be read by the computer on the other end; thus the name "modem" for modulator/demodulator. Having concurrent connectivity to more than one network from a computer or network device. Examples include: Being logged into the Corporate network via a local Ethernet connection, and dialing into AOL or other Internet service provider (ISP). Being on a CHI- provided Remote Access home network, and connecting to another network, such as a spouse's remote access. Configuring an ISDN router to dial into CHI and an ISP, depending on packet destination. Digital Subscriber Line (DSL) is a form of high-speed Internet access competing with cable modems. DSL works over standard phone lines and supports data speeds of over 2 Mbps downstream (to the user) and slower speeds upstream (to the Internet). A method of communication that incrementally can go from the speed of an ISDN to the speed of a T1 line. Frame Relay has a flat- rate billing charge instead of a per time usage. Frame Relay connects via the telephone company's network. DSL Frame Relay ISDN Remote Access via the telephone company's network. There are two flavors of Integrated Services Digital Network or ISDN: BRI and PRI. BRI is used for home office/remote access. BRI has two "Bearers channels at 64kbit (aggregate 128kb) and 1 D channel for signaling info. | Any access to CHI's corporate network through a non-CHI controlled network, device, or medium. Simultaneous direct access to a non-CHI network (such as the Internet, or a home network) from a remote device (PC, PDA, WAP phone, etc.) while connected into CHI's corporate network via a VPN tunnel. VPN Virtual Private Network (VPN) is a method for accessing a remote network via "tunneling" through the Internet. Split-tunneling 6.0 Revision History Information Security Roles & Responsibilities: Consolidated Holdings technology resources will proactively track threat activity and work to prohibit or correct such activity. Where unintentional unauthorized access is detected, the affected organization will be advised to correct exploitable vulnerabilities to prevent future occurrences. Where unauthorized access is determined to be intentional it will be assumed to be malicious and an appropriate response will be initiated. All Consolidated Holdings faculty members, staff, students, contractors, agents or other individuals utilizing computer resources, data communication networks, or other information technology infrastructure resources owned or leased by Consolidated Holdings, including any other state agencies having electrical connectivity to the network are subject to this policy. Additionally, any remote access, such as dial up connections, personal Internet Service Provider access or VPN connection, onto the Consolidated Holdings enterprise network or associated domains will have the same effect as direct access via CHI provided equipment or facilities. Virtual Private Network (VPN) Policy 1.0 Purpose The purpose of this policy is to provide guidelines for Remote Access IPSec or L2TP Virtual Private Network (VPN) connections to the CHI corporate network. 2.0 Scope This policy applies to all CHI employees, contractors, consultants, temporaries, and other workers including all personnel affiliated with third parties utilizing VPNs to access the CHI network. This policy applies to implementations of VPN that are directed through an IPSec Concentrator. 3.0 Policy Approved CHI employees and authorized third parties (customers, vendors, etc.) may utilize the benefits of VPNs, which are a "user managed" service. This means that the user is responsible for selecting an Internet Service Provider (ISP), coordinating installation, installing any required software, and paying associated fees. Further details may be found in the Remote Access Policy. Additionally It is the responsibility of employees with VPN privileges to ensure that unauthorized users are not allowed access to CHI internal networks. VPN use is to be controlled using either a one-time password authentication such as a token device or a public/private key system with a strong passphrase. When actively connected to the corporate network, VPNs will force all traffic to and from the PC over the VPN tunnel: all other traffic will be dropped. Dual (split) tunneling is NOT permitted; only one network connection is allowed. VPN gateways will be set up and managed by CHI network operational groups. All computers connected to CHI internal networks via VPN or any other technology must use the most up-to-date anti-virus software that is the corporate standard (provide URL to this software); this includes personal computers. VPN users will be automatically disconnected from CHI's network after thirty minutes of inactivity. The user must then logon again to reconnect to the network. Pings or other artificial network processes are not to be used to keep the connection open. The VPN concentrator is limited to an absolute connection time of 24 hours. Users of computers that are not CHI-owned equipment must configure the equipment to comply with CHI's VPN and Network policies. Only InfoSec-approved VPN clients may be used. By using VPN technology with personal equipment, users must understand that their machines are a de facto extension of CHI's network, and as such are subject to the same rules and regulations that apply to CHI-owned equipment, i.e., their machines must be configured to comply with InfoSec's Security Policies. 4.0 Enforcement Any employee found to be in violation this policy may be subject to disciplinary action, up to and including termination of employment. 5.0 Definitions Term IPSec Concentrator Definition A device in which VPN connections are terminated. 6.0 Revision History Remote Access: 1.0 Purpose The purpose of this policy is to define standards for connecting to CHI's network from any host. These standards are designed to minimize the potential exposure to CHI from damages which may result from unauthorized use of CHI resources. Damages include the loss of sensitive or company confidential data, intellectual property, damage to public image, damage to critical CHI internal systems, etc. 2.0 Scope This policy applies to all CHI employees, contractors, vendors and agents with a CHI- owned or personally-owned computer or workstation used to connect to the CHI network. This policy applies to remote access connections used to do work on behalf of CHI, including reading or sending email and viewing intranet web resources. Remote access implementations that are covered by this policy include, but are not limited to, dial-in modems, frame relay, ISDN, DSL, VPN, SSH, and cable modems, etc. 3.0 Policy 3.1 General It is the responsibility of CHI employees, contractors, vendors and agents with remote access privileges to CHI's corporate network to ensure that their remote access connection is given the same consideration as the user's on-site connection to CHI. General access to the Internet for recreational use by immediate household members through the CHI Network on personal computers is permitted for employees that have flat-rate services. The CHI employee is responsible to ensure the family member does not violate any CHI policies, does not perform illegal activities, and does not use the access for outside business interests. The CHI employee bears responsibility for the consequences should the access be misused. Please review the following policies for details of protecting information when accessing the corporate network via remote access methods, and acceptable use of CHI's network: Acceptable Encryption Policy Virtual Private Network (VPN) Policy 16 Wireless Communications Policy Acceptable Use Policy For additional information regarding CHI's remote access connection options, including how to order or disconnect service, cost comparisons, troubleshooting, etc., go to the Remote Access Services website. 3.2 Requirements Secure remote access must be strictly controlled. Control will be enforced via one- time password authentication or public/private keys with strong pass-phrases. For information on creating a strong pass-phrase see the Password Policy. At no time should any CHI employee provide their login or email password to anyone, not even family members. CHI employees and contractors with remote access privileges must ensure that their CHI-owned or personal computer or workstation, which is remotely connected to CHI's corporate network, is not connected to any other network at the same time, with the exception of personal networks that are under the complete control of the user. CHI employees and contractors with remote access privileges to CHI's corporate network must not use non-CHI email accounts (i.e., Hotmail, Yahoo, AOL), or other external resources to conduct CHI business, thereby ensuring that official business is never confused with personal business. Routers for dedicated ISDN lines configured for access to the CHI network must meet minimum authentication requirements of CHAP. Reconfiguration of a home user's equipment for the purpose of split-tunneling or dual homing is not permitted at any time. Frame Relay must meet minimum authentication requirements of DLCI standards. Non-standard hardware configurations must be approved by Remote Access Services, and InfoSec must approve security configurations for access to hardware. All hosts that are connected to CHI internal networks via remote access technologies must use the most up-to-date anti-virus software (place url to corporate software site here), this includes personal computers. Third party connections must comply with requirements as stated in the Third Party Agreement. nal equipment that is used to connect to CHI's networks must meet the requirements of CHI-owned equipment for remote access. Organizations or individuals who wish to implement non-standard Remote Access solutions to the CHI production network must obtain prior approval from Remote Access Services and InfoSec. 4.0 Enforcement Any employee found to be in violation this policy may be subject to disciplinary action, up to and including termination of employment. 5.0 Definitions Term Cable Modem Definition Cable companies such as AT&T Broadband provide Internet access over Cable TV coaxial cable. A cable modem accepts this coaxial cable and can receive data from the Internet at over 1.5 Mbps. Cable CHAP Dial-in Modem Dual Homing is currently available only in certain communities. Challenge Handshake Authentication Protocol is an authentication method that uses a one-way hashing function. DLCIData Link Connection Identifier (DLCI) is a unique number assigned to a Permanent Virtual Circuit (PVC) end point in a frame relay network. DLCI identifies a particular PVC endpoint within a user's access channel in a frame relay network, and has local significance only to that channel. A peripheral device that connects computers to each other for sending communications via the telephone lines. The modem modulates the digital data of computers into analog signals to send over the telephone lines, then demodulates back into digital signals to be read by the computer on the other end; thus the name "modem" for modulator/demodulator. Having concurrent connectivity to more than one network from a computer or network device. Examples include: Being logged into the Corporate network via a local Ethernet connection, and dialing into AOL or other Internet service provider (ISP). Being on a CHI- provided Remote Access home network, and connecting to another network, such as a spouse's remote access. Configuring an ISDN router to dial into CHI and an ISP, depending on packet destination. Digital Subscriber Line (DSL) is a form of high-speed Internet access competing with cable modems. DSL works over standard phone lines and supports data speeds of over 2 Mbps downstream (to the user) and slower speeds upstream (to the Internet). A method of communication that incrementally can go from the speed of an ISDN to the speed of a T1 line. Frame Relay has a flat- rate billing charge instead of a per time usage. Frame Relay connects via the telephone company's network. DSL Frame Relay ISDN Remote Access via the telephone company's network. There are two flavors of Integrated Services Digital Network or ISDN: BRI and PRI. BRI is used for home office/remote access. BRI has two "Bearers channels at 64kbit (aggregate 128kb) and 1 D channel for signaling info. | Any access to CHI's corporate network through a non-CHI controlled network, device, or medium. Simultaneous direct access to a non-CHI network (such as the Internet, or a home network) from a remote device (PC, PDA, WAP phone, etc.) while connected into CHI's corporate network via a VPN tunnel. VPN Virtual Private Network (VPN) is a method for accessing a remote network via "tunneling" through the Internet. Split-tunneling 6.0 Revision History
















