Question
The entire network is on a standard 192.168.0.0/24 subnet. You have been given administrator account credentials to the primary servers and network devices. During an
The entire network is on a standard 192.168.0.0/24 subnet. You have been given administrator account credentials to the primary servers and network devices.
During an assessment of the network you have spotted a machine that does not meet the standard naming conventions of the other systems. Running nmap from the Linux administrative machine that you were given access to fails to return any information on the offending system. The primary access point router (and firewall) is running DD-WRT (and thus iptables) presumably to save this small business some money compared to standard corporate solutions. Accessing the router via ssh with the given credentials, issuing:
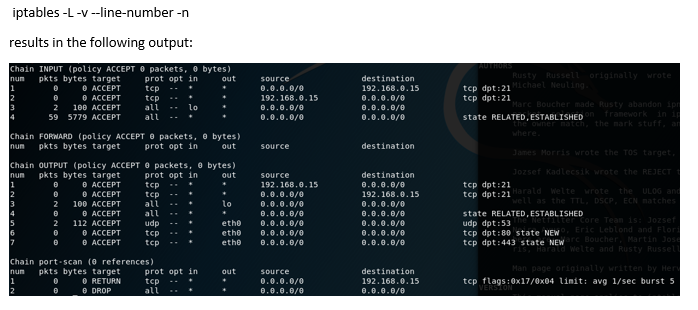
iptables -L -v --line-number -n
1. What is the likely IP address of the rogue machine?
2. Waht is the suspected protocol that the rogue machine is likely exploiting and what was the attacker likely doing with it?
3.Give 3 iptables commands that would allow your nmap scan to work?
4. How would you accomplish the above (3) in 1 command WITHOUT messing up any other possible neccesary block or allow rules i.e -iptable-F not acceptable?
5 Descript any faults in the above iptables rules NOT including the FORWARDING chain rule set?
iptables -L-v--line-number-n results in the following output: Chain INPUT (policy ACCEPT 0 packets, bytes) num pkts bytes target prot opt in tep tcp ali destination 192.168.0.15 ?.?.0.0/0 out tep dpt:21 tep dpt 21 state RELATED , ESTABLISHED 0 ACCEPT 0 ACCEPT 0.0.0.0/e 192. 168 .0 , 15 2 100 ACCEPT lo 59 5779 ACCEPTall 0.0.0.0/0 0.0.0.0/0 Chain FORWARD (policy ACCEPT 0 packets, bytes) num pkts bytes target prot opt in ot source destination Chain ouTPUT (policy ACCEPT packets, 0 bytes) num pkts bytes target prot opt in t source destination tcp dpt:21 tep dpt:21 192, 168.9.15 e e ACCEPT tcp tep 192.168.0.15 0.0.0.0/e 0 ACCEPT 0.0.0.0/0 0.0.0.0/e Lo 2100 ACCEPT 0 ACCEPT 2 112 ACCEPT 0 ACCEPT all state RELATED ,ESTABLISHED udp dpt:53 tcp dpt:80 state NEW tcp dpt:443 state NEW udp tcp eth 0.0.0.0/0 eth ,0.0.0/0 0.0.0.0/0 ?.?.0.0/0 Chain port-scan (e references) num pkts bytes target prot opt in ut tcp source 0.0.0.0/0 destination 192.168.0.15 O RETURN 8 DROP tcp flags:0x17/0x04 linit: avg 1/sec burst 5 iptables -L-v--line-number-n results in the following output: Chain INPUT (policy ACCEPT 0 packets, bytes) num pkts bytes target prot opt in tep tcp ali destination 192.168.0.15 ?.?.0.0/0 out tep dpt:21 tep dpt 21 state RELATED , ESTABLISHED 0 ACCEPT 0 ACCEPT 0.0.0.0/e 192. 168 .0 , 15 2 100 ACCEPT lo 59 5779 ACCEPTall 0.0.0.0/0 0.0.0.0/0 Chain FORWARD (policy ACCEPT 0 packets, bytes) num pkts bytes target prot opt in ot source destination Chain ouTPUT (policy ACCEPT packets, 0 bytes) num pkts bytes target prot opt in t source destination tcp dpt:21 tep dpt:21 192, 168.9.15 e e ACCEPT tcp tep 192.168.0.15 0.0.0.0/e 0 ACCEPT 0.0.0.0/0 0.0.0.0/e Lo 2100 ACCEPT 0 ACCEPT 2 112 ACCEPT 0 ACCEPT all state RELATED ,ESTABLISHED udp dpt:53 tcp dpt:80 state NEW tcp dpt:443 state NEW udp tcp eth 0.0.0.0/0 eth ,0.0.0/0 0.0.0.0/0 ?.?.0.0/0 Chain port-scan (e references) num pkts bytes target prot opt in ut tcp source 0.0.0.0/0 destination 192.168.0.15 O RETURN 8 DROP tcp flags:0x17/0x04 linit: avg 1/sec burst 5Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


