The first picture is the application 2 in the problem statement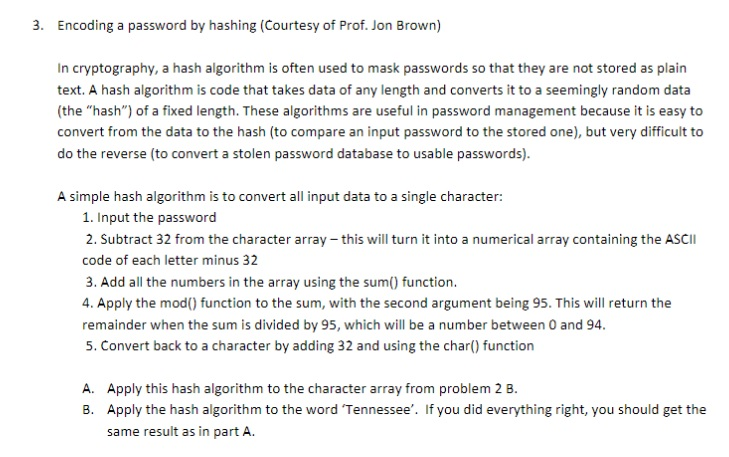
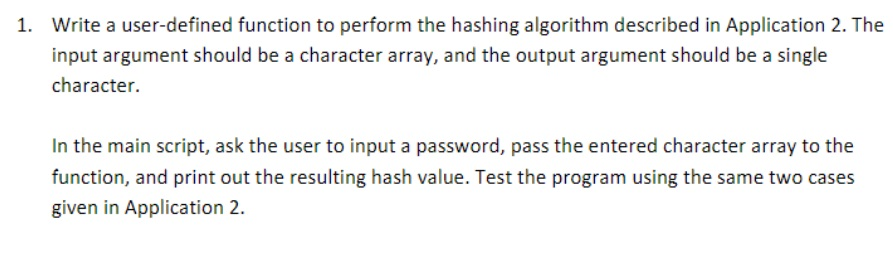
3. Encoding a password by hashing (Courtesy of Prof. Jon Brown) In cryptography, a hash algorithm is often used to mask passwords so that they are not stored as plain text. A hash algorithm is code that takes data of any length and converts it to a seemingly random data (the "hash") of a fixed length. These algorithms are useful in password management because it is easy to convert from the data to the hash (to compare an input password to the stored one), but very difficult to do the reverse (to convert a stolen password database to usable passwords). A simple hash algorithm is to convert all input data to a single character: 1. Input the password 2. Subtract 32 from the character array - this will turn it into a numerical array containing the ASCII code of each letter minus 32 3. Add all the numbers in the array using the sum() function. 4. Apply the mod() function to the sum, with the second argument being 95. This will return the remainder when the sum is divided by 95, which will be a number between 0 and 94. 5. Convert back to a character by adding 32 and using the char() function A. Apply this hash algorithm to the character array from problem 2 B. B. Apply the hash algorithm to the word 'Tennessee'. If you did everything right, you should get the same result as in part A. 1. Write a user-defined function to perform the hashing algorithm described in Application 2. The input argument should be a character array, and the output argument should be a single character. In the main script, ask the user to input a password, pass the entered character array to the function, and print out the resulting hash value. Test the program using the same two cases given in Application 2. 3. Encoding a password by hashing (Courtesy of Prof. Jon Brown) In cryptography, a hash algorithm is often used to mask passwords so that they are not stored as plain text. A hash algorithm is code that takes data of any length and converts it to a seemingly random data (the "hash") of a fixed length. These algorithms are useful in password management because it is easy to convert from the data to the hash (to compare an input password to the stored one), but very difficult to do the reverse (to convert a stolen password database to usable passwords). A simple hash algorithm is to convert all input data to a single character: 1. Input the password 2. Subtract 32 from the character array - this will turn it into a numerical array containing the ASCII code of each letter minus 32 3. Add all the numbers in the array using the sum() function. 4. Apply the mod() function to the sum, with the second argument being 95. This will return the remainder when the sum is divided by 95, which will be a number between 0 and 94. 5. Convert back to a character by adding 32 and using the char() function A. Apply this hash algorithm to the character array from problem 2 B. B. Apply the hash algorithm to the word 'Tennessee'. If you did everything right, you should get the same result as in part A. 1. Write a user-defined function to perform the hashing algorithm described in Application 2. The input argument should be a character array, and the output argument should be a single character. In the main script, ask the user to input a password, pass the entered character array to the function, and print out the resulting hash value. Test the program using the same two cases given in Application 2








