Question: The following security levels and categories are given: Security levels: TOP SECRET > SECRET > CONFIDENTIAL > UNCLASSIFIED Categories: {Regular-Faculty, Adjunct-Faculty, Staff, Grad-Student, Undergrad-Student}
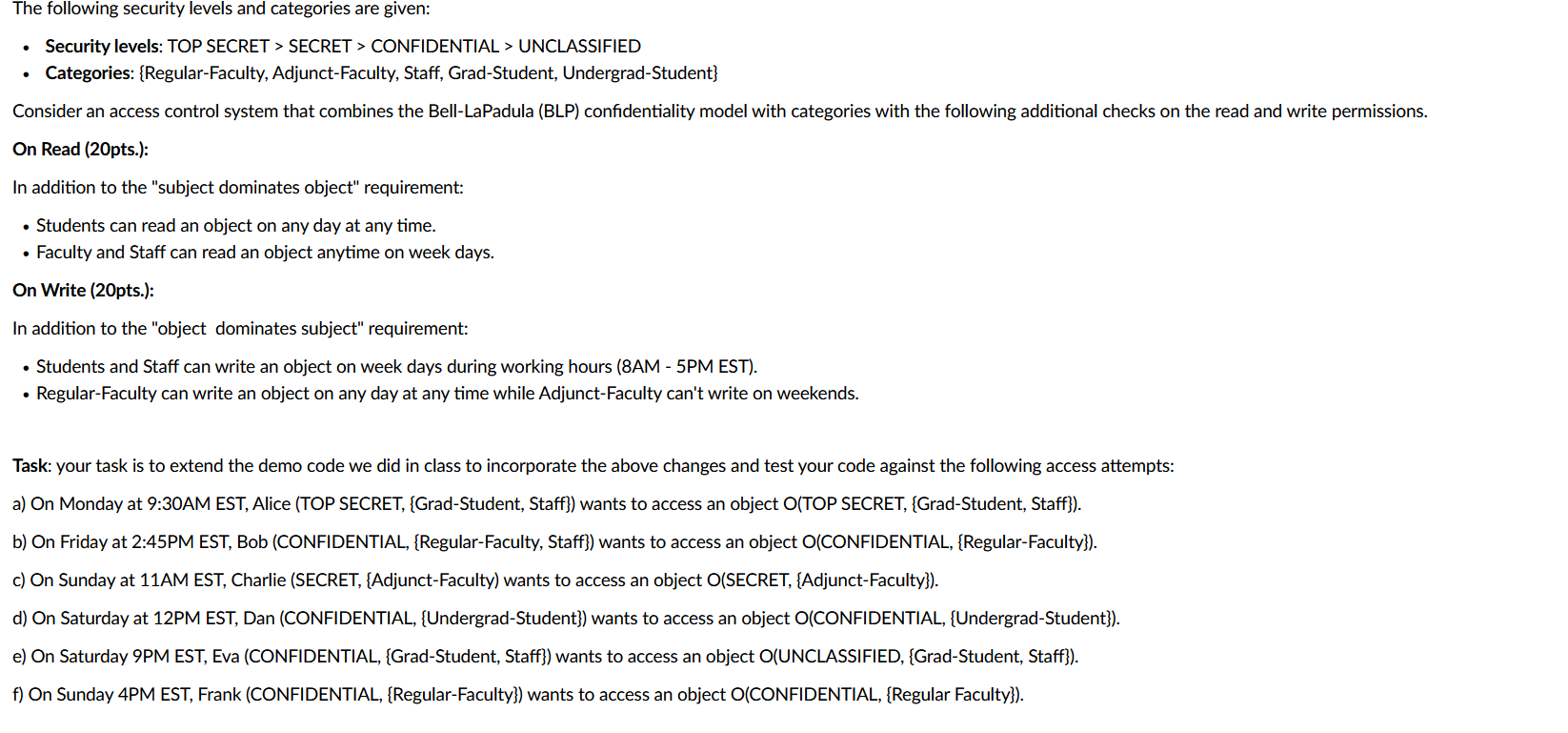
The following security levels and categories are given: Security levels: TOP SECRET > SECRET > CONFIDENTIAL > UNCLASSIFIED Categories: {Regular-Faculty, Adjunct-Faculty, Staff, Grad-Student, Undergrad-Student} Consider an access control system that combines the Bell-LaPadula (BLP) confidentiality model with categories with the following additional checks on the read and write permissions. On Read (20pts.): In addition to the "subject dominates object" requirement: Students can read an object on any day at any time. Faculty and Staff can read an object anytime on week days. On Write (20pts.): In addition to the "object dominates subject" requirement: Students and Staff can write an object on week days during working hours (8AM - 5PM EST). Regular-Faculty can write an object on any day at any time while Adjunct-Faculty can't write on weekends. Task: your task is to extend the demo code we did in class to incorporate the above changes and test your code against the following access attempts: a) On Monday at 9:30AM EST, Alice (TOP SECRET, {Grad-Student, Staff}) wants to access an object O(TOP SECRET, {Grad-Student, Staff}). b) On Friday at 2:45PM EST, Bob (CONFIDENTIAL, {Regular-Faculty, Staff}) wants to access an object O(CONFIDENTIAL, {Regular-Faculty}). c) On Sunday at 11AM EST, Charlie (SECRET, {Adjunct-Faculty) wants to access an object O(SECRET, {Adjunct-Faculty}). d) On Saturday at 12PM EST, Dan (CONFIDENTIAL, {Undergrad-Student}) wants to access an object O(CONFIDENTIAL, {Undergrad-Student}). e) On Saturday 9PM EST, Eva (CONFIDENTIAL, {Grad-Student, Staff}) wants to access an object O(UNCLASSIFIED, {Grad-Student, Staff}). f) On Sunday 4PM EST, Frank (CONFIDENTIAL, {Regular-Faculty}) wants to access an object O(CONFIDENTIAL, {Regular Faculty}).
Step by Step Solution
There are 3 Steps involved in it
To implement the access control system with the BellLaPadula BLP confidentiality model and the addit... View full answer

Get step-by-step solutions from verified subject matter experts


