Answered step by step
Verified Expert Solution
Question
1 Approved Answer
The qustion: Apply this algorithm to matrix 3 * 3 and text 0101. Apply algorithm steps and explain step by step (assume matrix values). E

The qustion:
Apply this algorithm to matrix 3 * 3 and text 0101. Apply algorithm steps and explain step by step (assume matrix values).
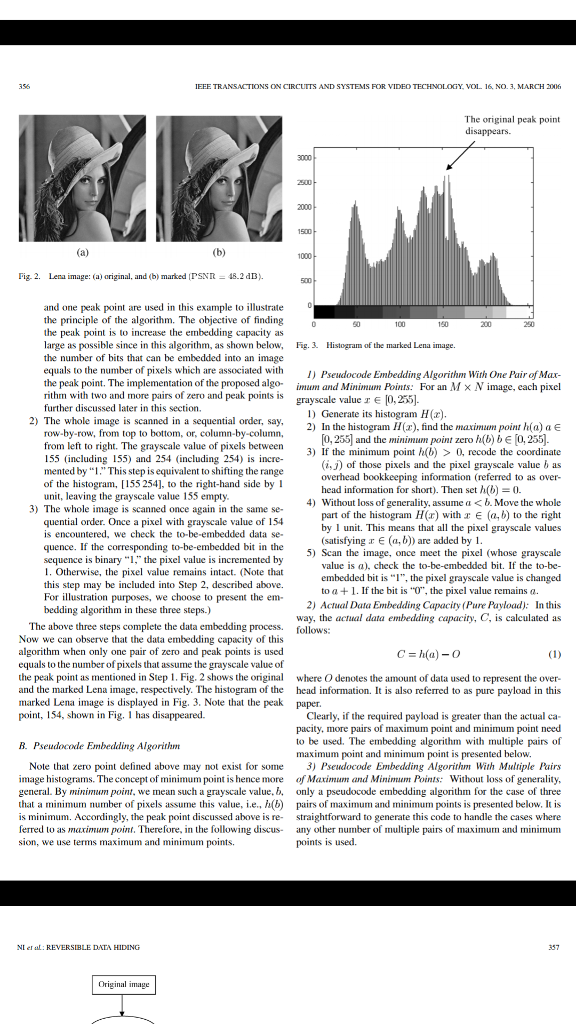
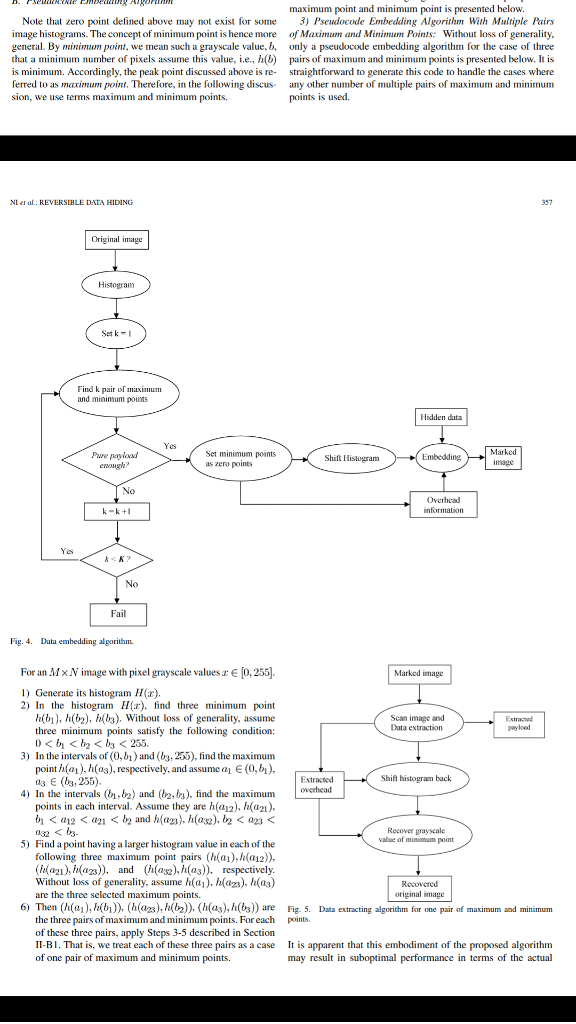
E DATA HIDING Peak point 5]. This observation is valid to all lossless data ms that use modulo 256 addition to achieve ersible marking technique that is suitable for 2oo t of data hiding was presented in [16]. This segments an image into nonoverlapping blocks, luces a discriminating function to classify these 1500 e groups: R(egular), S(ingular), and U(nusable duces a flipping operation, which can convert 000 an S-block and vice versa. A U-block remains 2000 Zero point fipping operation. By assigning, say, binary1 and binary 0 to an S-block, all R-and S-blocks o a chosen sequential order, resulting in a biased he binary numbers of 1 and 0 are not balanced) e. This biased binary sequence is losslessly Fig. Histogram of Lena image. leave space for data embedding and the com- uence is embedded into the cover media as an 250 grayscale image while the PSNR is 38 dB. Even though the ter reconstruction of the original image. In data R- and S-blocks are scanned once again and the ion is applied whenever necessary to make the IS-block sequence coincident with the to-be-em- payload is high, the PSNR is still not high enough. In this paper, we propose a new reversible data embedding technique, which can embed a large amount of data (5-80 kb for a 512 512 8 grayscale image) while keeping a very the overhead data mentioned above. high visual quality for all natural images, specifically, the PSN el and successful in reversible data hiding. marked i not large enough for some applications. Specifi- be higher than 48 dB. It utilizes the zero or the minimum point dding capacity estimated by authors ranges from the a 512 512 8 cover grayscale image when amplitude is 4 (the estimated average PSNR image versus the original image is 39 dB) [16] tested on different types of images, including some commonly m with the method is that when the embedding ses in order to increase the payload, the visual all of the 1096 i arked image will drop severely due to annoying tion of our proposed technique is quite simple and the execution crease the payload dramatically, a new lossless time is rather short. Although the proposed lossless data hiding hnique [17] based on integer wavelet transform technique is applied to stil images, i is also applicable to videos I (a second generation wavelet transform, which which consist of a sequence of i ind-off errors) was developed recently. Because The rest of the paper is organized as follows. The proposed decorrelation capability of wavelet transform, algorithm and its characteristics are described in Section II. Ex it plane compression of IWT coeficients in perimental results are presented in Section III, and conclusions subbands creates more space for data hiding. are drawn in Sections IV two to five imes payload as large as that in lly, its payload ranges from 15 to 94 kb for a 8 grayscale image at the same (39 dB) PSNR images compared with the original images. To ible data hiding, a histogram algonthm. pre-processing to prevent over/underflow. This ification causes, however, a relatively low PSNR some important issues including data embedding capacity are image versus the original image though there addressed. artifacts. It is noted that reversible data hiding ig. the of the marked image versus the original image is guaranteed to of the histogram (defined below) and slightly modifies the pixel grayscale values to embed data. This technique can be applied to virtually all types of images. Up to now, it has been successfully used images, medical images, texture images, aerial images, and mages in CorelDRAW database. The computa- mages. We first use the "Lena" image as an example to illustrate our modifications algorithm. Then the dada emhedding and extracting of the pro- posed algorithm are presented in terms of pseudocode. Finally For a given grayscale image, say, the Lena image (512 x 512 8). we first generate its histogram as shown in Fig. creasing attention recently, and more algorithms loped. A very recent example is the technique 1. The main idea is that in the embedding phase, Al Using an quantized and the residual r is obtained. With One Zero Point and One Peak Po In the histogram, we first find a zero poin, and then a peak point, A zero point corresponds to the grayscale value which no pixel in the given image assumes, e.g. h(255) as shown in Fig. 1. A peak point corresponds to the grayscale value which the maximum number of pixels in the given image assumes, e.g, (154) as shown in Fig.1 For the sake of notational simplicity, only one zero point rs adopt the CALIC lossless image compression the quantized values as side information, to press the quantization residuals to create high compressed residual and ta are concatenated and embedded into the host ralized-LSB modification method. The payload Lie is from 15 to 143 kb for a 512 5128 e payload data h. The EEE TRANSACTIONS ON CIRCUITS AND SYSTEMS FOR VIDEO TECHNOLOGY, VOL 16, NO. 3, MARCH 2006 The original peak point disappears E DATA HIDING Peak point 5]. This observation is valid to all lossless data ms that use modulo 256 addition to achieve ersible marking technique that is suitable for 2oo t of data hiding was presented in [16]. This segments an image into nonoverlapping blocks, luces a discriminating function to classify these 1500 e groups: R(egular), S(ingular), and U(nusable duces a flipping operation, which can convert 000 an S-block and vice versa. A U-block remains 2000 Zero point fipping operation. By assigning, say, binary1 and binary 0 to an S-block, all R-and S-blocks o a chosen sequential order, resulting in a biased he binary numbers of 1 and 0 are not balanced) e. This biased binary sequence is losslessly Fig. Histogram of Lena image. leave space for data embedding and the com- uence is embedded into the cover media as an 250 grayscale image while the PSNR is 38 dB. Even though the ter reconstruction of the original image. In data R- and S-blocks are scanned once again and the ion is applied whenever necessary to make the IS-block sequence coincident with the to-be-em- payload is high, the PSNR is still not high enough. In this paper, we propose a new reversible data embedding technique, which can embed a large amount of data (5-80 kb for a 512 512 8 grayscale image) while keeping a very the overhead data mentioned above. high visual quality for all natural images, specifically, the PSN el and successful in reversible data hiding. marked i not large enough for some applications. Specifi- be higher than 48 dB. It utilizes the zero or the minimum point dding capacity estimated by authors ranges from the a 512 512 8 cover grayscale image when amplitude is 4 (the estimated average PSNR image versus the original image is 39 dB) [16] tested on different types of images, including some commonly m with the method is that when the embedding ses in order to increase the payload, the visual all of the 1096 i arked image will drop severely due to annoying tion of our proposed technique is quite simple and the execution crease the payload dramatically, a new lossless time is rather short. Although the proposed lossless data hiding hnique [17] based on integer wavelet transform technique is applied to stil images, i is also applicable to videos I (a second generation wavelet transform, which which consist of a sequence of i ind-off errors) was developed recently. Because The rest of the paper is organized as follows. The proposed decorrelation capability of wavelet transform, algorithm and its characteristics are described in Section II. Ex it plane compression of IWT coeficients in perimental results are presented in Section III, and conclusions subbands creates more space for data hiding. are drawn in Sections IV two to five imes payload as large as that in lly, its payload ranges from 15 to 94 kb for a 8 grayscale image at the same (39 dB) PSNR images compared with the original images. To ible data hiding, a histogram algonthm. pre-processing to prevent over/underflow. This ification causes, however, a relatively low PSNR some important issues including data embedding capacity are image versus the original image though there addressed. artifacts. It is noted that reversible data hiding ig. the of the marked image versus the original image is guaranteed to of the histogram (defined below) and slightly modifies the pixel grayscale values to embed data. This technique can be applied to virtually all types of images. Up to now, it has been successfully used images, medical images, texture images, aerial images, and mages in CorelDRAW database. The computa- mages. We first use the "Lena" image as an example to illustrate our modifications algorithm. Then the dada emhedding and extracting of the pro- posed algorithm are presented in terms of pseudocode. Finally For a given grayscale image, say, the Lena image (512 x 512 8). we first generate its histogram as shown in Fig. creasing attention recently, and more algorithms loped. A very recent example is the technique 1. The main idea is that in the embedding phase, Al Using an quantized and the residual r is obtained. With One Zero Point and One Peak Po In the histogram, we first find a zero poin, and then a peak point, A zero point corresponds to the grayscale value which no pixel in the given image assumes, e.g. h(255) as shown in Fig. 1. A peak point corresponds to the grayscale value which the maximum number of pixels in the given image assumes, e.g, (154) as shown in Fig.1 For the sake of notational simplicity, only one zero point rs adopt the CALIC lossless image compression the quantized values as side information, to press the quantization residuals to create high compressed residual and ta are concatenated and embedded into the host ralized-LSB modification method. The payload Lie is from 15 to 143 kb for a 512 5128 e payload data h. The EEE TRANSACTIONS ON CIRCUITS AND SYSTEMS FOR VIDEO TECHNOLOGY, VOL 16, NO. 3, MARCH 2006 The original peak point disappearsStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


