Answered step by step
Verified Expert Solution
Question
1 Approved Answer
The screenshots show some parts of a VirusTotal report about an Android app. Identify possible malicious/suspicious indicators among the provided information. Make a conclusion whether
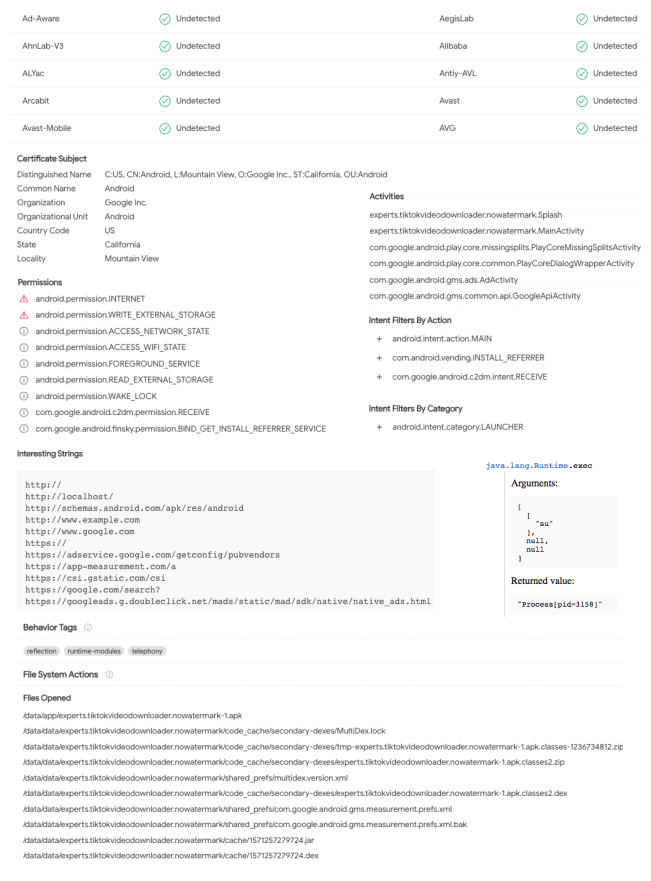

The screenshots show some parts of a VirusTotal report about an Android app. Identify possible malicious/suspicious indicators among the provided information. Make a conclusion whether this application is malware
Ad-Aware Undetected Aegislab > Undetected > > AhnLab-V3 Undetected Alibaba Undetected ALYac Undetected Antly-AVL Undetected Arcabit > Avast Undetected Undetected Undetected Avast-Mobile . AVG Undetected Certificate Subject Distinguished Name C:US. CN:Android. L:Mountain View.O:Google Inc. ST:California, Ou: Android Common Name Android Activities Organization Google Inc. Organizational Unit Android experts.tiktokvideodownloader.nowatermark Splash Country Code US experts.tiktokvideodownloader.nowatermark.MainActivity State California com.google.android.play.core.missingsplits.PlayCoreMissingSplitsActivity Locality Mountain View com.google.android.play.core.common.PlayCoreDialogWrapper Activity Permissions com.google.android.gms.ads.AdActivity Aandroid permission INTERNET com.google.android.gms.common.api.GoogleApi Activity Aandroid.permission.WRITE_EXTERNAL_STORAGE Intent Filters By Action android permission.ACCESS_NETWORK_STATE + android.intent.action.MAIN android permission.ACCESS_WIFI_STATE O android.permission. FOREGROUND_SERVICE + com.android.vending.INSTALL_REFERRER android permission.READ_EXTERNAL_STORAGE + com google.android.c2dm.intent.RECEIVE android permission.WAKE_LOCK O com.google.android.c2dm.permission.RECEIVE Intent Filters By Category O com.google.android.finsky.permission.BIND_GET_INSTALL_REFERRER_SERVICE + android.intent.category.LAUNCHER Interesting Strings java.lang.Runtime.exe Arguments: http:// http://localhost/ http://schemas.android.com/apk/res/android http://www.example.com http://www.google.com https:// https://adservice.google.com/getconfig/pubvendors https://app-measurement.com/a https://csi.gstatic.com/esi https://google.com/search? https://googleads.g.doubleclick.net/mads/static/mad/sdkativeative_adu.html null, null 1 Returned value: "Processi pid-31501" Behavior Tags reflection runtime-modules telephony File System Actions Files Opened datalapplexperts.tiktokvideodownloader.nowatermark-lapk dataidatalexperts.tiktokvideodownloader.nowatermarkcode_cache/secondary-dexes/MultiDex.lock dataidatalexperts.tiktokvideodownloader.nowatermarkcode_cache/secondary-dexes/tmp-experts tiktokvideodownloader nowatermark-1.apk classes-1236734812.zip idataidatalexperts.tiktokvideodownloader.nowatermark/code_cache/secondary-deweslexperts.titokvideodownloader nowatermark-1.apk.classes2.zip dataidatalexperts.tiktokvideodownloader.nowatermark/shared_prefs/multidex version.xml Idataidatalexperts.iktokvideo downloader.nowatermarkloode_cache/secondary-dexestexperts.tictakvideodownloader.nowatermark-1.apk.classes2.dex Idataidatalexperts.tiktokvideodownloader.nowatermark/shared_prefscom.google.android gms.measurement.prefs.xml datadatalexperts.tiktokvideodownloader.nowatermarishared_prefscom.google.android.gms.measurement.prefs.xmlbak Idata datalexperts.tiktok videodownloader.nowatermarkdcache/1571257279724.jar Idataidatalexperts.tiktokvideodownloader.nowatermari cache/1571257279724.dex Highlighted Actions Process And Service Actions Permissions Checked + com.google.android.c2dm.permission SEND + android.permission.ACCESS_NETWORK_STATE Calls Highlighted android telephony TelephonyManager getNetwork Operator android telephony.TelephonyManager.getPhone Type android utilBased decode android.util.Base64 encode javax.crypto. Cipher.doFinal Shell Commands su Cryptographical Algorithms Observed AES Synchronization Mechanisms & Signals Signals Hooked android.intent.action.PROXY_CHANGE android.intent.action USER PRESENT android.intent.action SCREEN_OFF com.google.android.ads.intent.DEBUG_LOGGING_ENABLEMENT_CHANGED android.intent action SCREEN ON android.intent.action.BATTERY CHANGED android.hardware.usb.action. USB_STATE Cryptographical Keys Observed Ox00000000 B2 B01C CC 2E 25 25 E8 86 BD 09 CS 21 B 4C PO ......... Encoding Algorithms Observed base64 Decoded Text (DEFAULT) 1:748747249691:android: aeaocd50325114840be 8838774c0eb1a5790c2eac3bbb80631a8cff4cd android.util. Base64.decode Arguments: EXONIMYNXCL3/R6033212, "2" Returned value "OODOODOO 65 74 17 9 Os 4 a 18 2 61 61 C C C 4D Bet.......... ODOODLO 3 OB BD TT 44 SE LE ND DE 3 D 93 33 18 re............." Ad-Aware Undetected Aegislab > Undetected > > AhnLab-V3 Undetected Alibaba Undetected ALYac Undetected Antly-AVL Undetected Arcabit > Avast Undetected Undetected Undetected Avast-Mobile . AVG Undetected Certificate Subject Distinguished Name C:US. CN:Android. L:Mountain View.O:Google Inc. ST:California, Ou: Android Common Name Android Activities Organization Google Inc. Organizational Unit Android experts.tiktokvideodownloader.nowatermark Splash Country Code US experts.tiktokvideodownloader.nowatermark.MainActivity State California com.google.android.play.core.missingsplits.PlayCoreMissingSplitsActivity Locality Mountain View com.google.android.play.core.common.PlayCoreDialogWrapper Activity Permissions com.google.android.gms.ads.AdActivity Aandroid permission INTERNET com.google.android.gms.common.api.GoogleApi Activity Aandroid.permission.WRITE_EXTERNAL_STORAGE Intent Filters By Action android permission.ACCESS_NETWORK_STATE + android.intent.action.MAIN android permission.ACCESS_WIFI_STATE O android.permission. FOREGROUND_SERVICE + com.android.vending.INSTALL_REFERRER android permission.READ_EXTERNAL_STORAGE + com google.android.c2dm.intent.RECEIVE android permission.WAKE_LOCK O com.google.android.c2dm.permission.RECEIVE Intent Filters By Category O com.google.android.finsky.permission.BIND_GET_INSTALL_REFERRER_SERVICE + android.intent.category.LAUNCHER Interesting Strings java.lang.Runtime.exe Arguments: http:// http://localhost/ http://schemas.android.com/apk/res/android http://www.example.com http://www.google.com https:// https://adservice.google.com/getconfig/pubvendors https://app-measurement.com/a https://csi.gstatic.com/esi https://google.com/search? https://googleads.g.doubleclick.net/mads/static/mad/sdkativeative_adu.html null, null 1 Returned value: "Processi pid-31501" Behavior Tags reflection runtime-modules telephony File System Actions Files Opened datalapplexperts.tiktokvideodownloader.nowatermark-lapk dataidatalexperts.tiktokvideodownloader.nowatermarkcode_cache/secondary-dexes/MultiDex.lock dataidatalexperts.tiktokvideodownloader.nowatermarkcode_cache/secondary-dexes/tmp-experts tiktokvideodownloader nowatermark-1.apk classes-1236734812.zip idataidatalexperts.tiktokvideodownloader.nowatermark/code_cache/secondary-deweslexperts.titokvideodownloader nowatermark-1.apk.classes2.zip dataidatalexperts.tiktokvideodownloader.nowatermark/shared_prefs/multidex version.xml Idataidatalexperts.iktokvideo downloader.nowatermarkloode_cache/secondary-dexestexperts.tictakvideodownloader.nowatermark-1.apk.classes2.dex Idataidatalexperts.tiktokvideodownloader.nowatermark/shared_prefscom.google.android gms.measurement.prefs.xml datadatalexperts.tiktokvideodownloader.nowatermarishared_prefscom.google.android.gms.measurement.prefs.xmlbak Idata datalexperts.tiktok videodownloader.nowatermarkdcache/1571257279724.jar Idataidatalexperts.tiktokvideodownloader.nowatermari cache/1571257279724.dex Highlighted Actions Process And Service Actions Permissions Checked + com.google.android.c2dm.permission SEND + android.permission.ACCESS_NETWORK_STATE Calls Highlighted android telephony TelephonyManager getNetwork Operator android telephony.TelephonyManager.getPhone Type android utilBased decode android.util.Base64 encode javax.crypto. Cipher.doFinal Shell Commands su Cryptographical Algorithms Observed AES Synchronization Mechanisms & Signals Signals Hooked android.intent.action.PROXY_CHANGE android.intent.action USER PRESENT android.intent.action SCREEN_OFF com.google.android.ads.intent.DEBUG_LOGGING_ENABLEMENT_CHANGED android.intent action SCREEN ON android.intent.action.BATTERY CHANGED android.hardware.usb.action. USB_STATE Cryptographical Keys Observed Ox00000000 B2 B01C CC 2E 25 25 E8 86 BD 09 CS 21 B 4C PO ......... Encoding Algorithms Observed base64 Decoded Text (DEFAULT) 1:748747249691:android: aeaocd50325114840be 8838774c0eb1a5790c2eac3bbb80631a8cff4cd android.util. Base64.decode Arguments: EXONIMYNXCL3/R6033212, "2" Returned value "OODOODOO 65 74 17 9 Os 4 a 18 2 61 61 C C C 4D Bet.......... ODOODLO 3 OB BD TT 44 SE LE ND DE 3 D 93 33 18 reStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


