Answered step by step
Verified Expert Solution
Question
1 Approved Answer
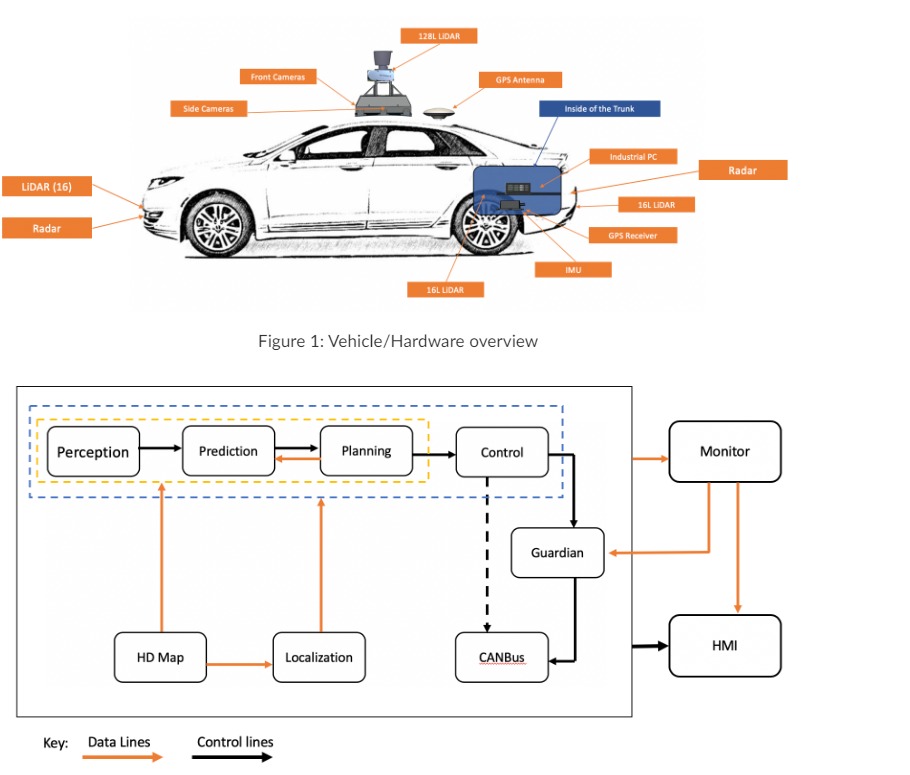
The tasks for the assignment are described in the following.Figure 1 : Vehicle / Hardware overview Task 1 - Identify the main assets ( the
The tasks for the assignment are described in the following.Figure : VehicleHardware overview
Task Identify the main assets the targets of the attacker of the system.
Task Identify the entry points of the system; that is the points that the attacker can use to inject data into the system and may modify its behavior.
Task Use abuse case threat modeling method to identify to abuse cases to ApolloAuto and relate the threats to the entry points that you identified in Task
Task Use the STRIDE threat modeling method to identify to major reasonable attack goals and relate them to the entry points that you identified in Task Next, develop an attack tree for each of the identified attack goals.
Task Reflect on the lessons that you learned from the exercise in about two paragraphs.
You may visit Section of this documentLinks to an external site. to see examples of to Credit card.
You should submit a report that describes your work on each of the tasks.
Task Give constructive feedback to the assigned submission. The comments should discuss the strengths and weaknesses of the work and should include improvement suggestions. The reviews must be submitted as a comment to the assigned submission. You do not need to submit an answer to Task in your report.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


