Answered step by step
Verified Expert Solution
Question
1 Approved Answer
The transposition cipher is also known as permutation cipher. We know give the mathematical description of the permutation cryptosystem as follows: Def: Permutation Cipher
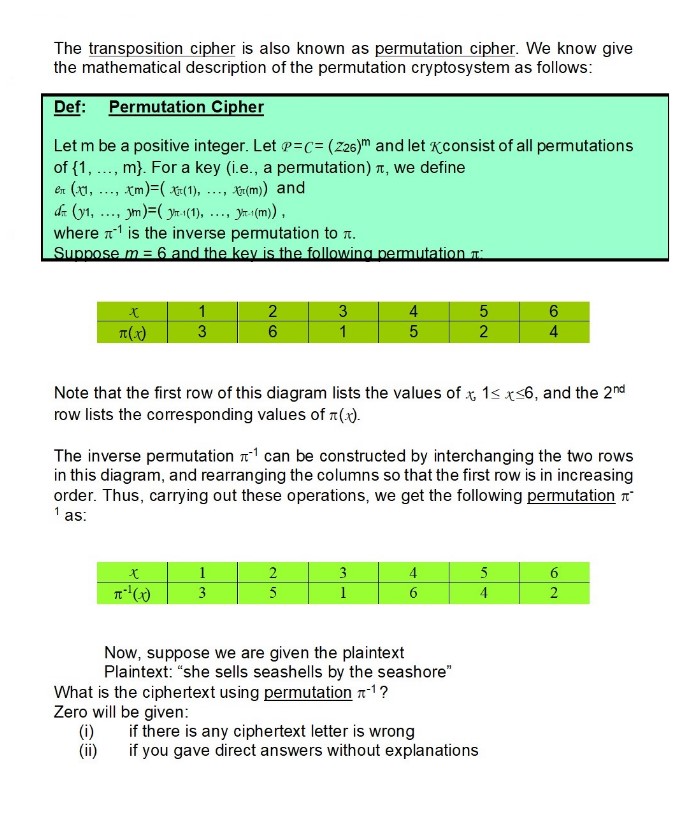
The transposition cipher is also known as permutation cipher. We know give the mathematical description of the permutation cryptosystem as follows: Def: Permutation Cipher Let m be a positive integer. Let P=C= (Z26)m and let consist of all permutations of {1, ..., m}. For a key (i.e., a permutation), we define en (x1, d. (y1, where xm)=(x(1), Jm)=(y-1(1), .... Xx(m)) and y-1(m)), is the inverse permutation to . Suppose m = 6 and the key is the following permutation x 1 2 3 4 5 6 (x) 3 6 1 5 2 4 Note that the first row of this diagram lists the values of x 1x6, and the 2nd row lists the corresponding values of (x). The inverse permutation can be constructed by interchanging the two rows in this diagram, and rearranging the columns so that the first row is in increasing order. Thus, carrying out these operations, we get the following permutation 1 as: x 1 2 3 4 5 -1(x) 3 5 1 6 4 Now, suppose we are given the plaintext Plaintext: "she sells seashells by the seashore" What is the ciphertext using permutation ? Zero will be given: (i) (ii) if there is any ciphertext letter is wrong if you gave direct answers without explanations 6 62
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


