Question
THIS IS A JAVA CLASS ASSIGNMENT! I am working on this final project for my JAVA class and I a having a bit of a
THIS IS A JAVA CLASS ASSIGNMENT! I am working on this final project for my JAVA class and I a having a bit of a hard time working through a few things. Here are screen shots of the project outlines:
Now, I have done the pseudocode and generated a basic java code, but I really need help to add a second class to the code and the "process documentation" portion of the "critical elements" section.
Here is my JAVA code thus far"
// import statements
import java.io.BufferedReader;
import java.io.FileReader;
import java.io.IOException;
import java.io.InputStreamReader;
import java.security.MessageDigest;
import java.security.NoSuchAlgorithmException;
import java.util.Scanner;
// Create a class secret public class Authentication {
// main() method public static void main(String[] args) throws IOException {
// Call loginScreen() method loginScreen();
}
// loginScreen() method for user login public static void loginScreen() {
// Declare variables String genPwd = "";
int flag = 0, attempts = 3;
// Create an object 'br' for BufferedReader class to accept data from // user and read data from a file BufferedReader br = new BufferedReader(new InputStreamReader(System.in));
System.out.println(" Login");
try {
do {
attempts--;
System.out.println("Enter Username");
String uName = br.readLine();
System.out.println("Enter Password");
String pwd = br.readLine();
// Create the object 'md' for the MessageDigest class to convert // password in md5 MessageDigest md = MessageDigest.getInstance("MD5");
md.update(pwd.getBytes());
byte[] bytes = md.digest();
// Create the object for String StringBuilder sb = new StringBuilder();
for (int j = 0; j
sb.append(Integer.toString((bytes[j] & 0xff) + 0x100, 16).substring(1));
}
genPwd = sb.toString();
//System.out.println("Password entered by you:" + genPwd); String currentLine;
// Open credentials.txt file BufferedReader bin = new BufferedReader(new FileReader("credentials.txt"));
// Check the username and password from the file // Read the each line from the file while ((currentLine = bin.readLine()) != null) {
// Split the line where the tab is present String[] arr = currentLine.split(" ");
// Check username if (arr[0].equals(uName)) {
// Check password if (arr[1].equals(genPwd)) {
flag = 1;
break;
}
}
}
// Checks if the user enters more then 3 attempts if (attempts == 0) {
System.out.println("You are attempted to login more then three times");
System.out.println("Exiting...");
System.exit(1);
}
// If username and password is true if (flag == 1) {
// Call adminScreen() method adminScreen();
break;
} // If invalid username and password else {
System.out.println("Invalid Username or Password.");
System.out.println("Please try again.");
System.out.println(attempts + " more attemptes left. ");
}
} while (attempts > 0);
} catch (NoSuchAlgorithmException e) {
e.printStackTrace();
} catch (IOException e) {
e.printStackTrace();
}
}
// Create adminScreen() method public static void adminScreen() {
String logOut;
// Create Scanner class object to accept data from the user Scanner sc = new Scanner(System.in);
System.out.println(" Welcome Admin");
System.out.println("Press 999 for log out ");
// Accept data from the user do {
logOut = sc.nextLine();
} while (!logOut.equals("999"));
// If the user want to exit from admin screen if (logOut.equals("999")) {
// Call login screen loginScreen();
}
}
}
And here is the pseduocode that I have:
ASK for username
ASK for password
CONVERT password using MD5
IF username is valid
AND password is valid
THEN grant access to authorized files
IF zookeeper
THEN display zookeeper files
IF admin
THEN display admin files
IF Vet
THEN display vet files
ELSE deny access
PRINT incorrect username and/or password
PRINT please try again
RETURN to credentials screen
ASK for username
ASK for password
IF incorrect username and/or password is entered 3 times
THEN deny access
PRINT 3 incorrect login attempts
EXIT credentials page
ASK for logout when desired by user
IF logout is requested
THEN return to credentials page
So, like I said, I need help to add a second class to my code and refine my pseudocode to match the changes.
THANK YOU!!!
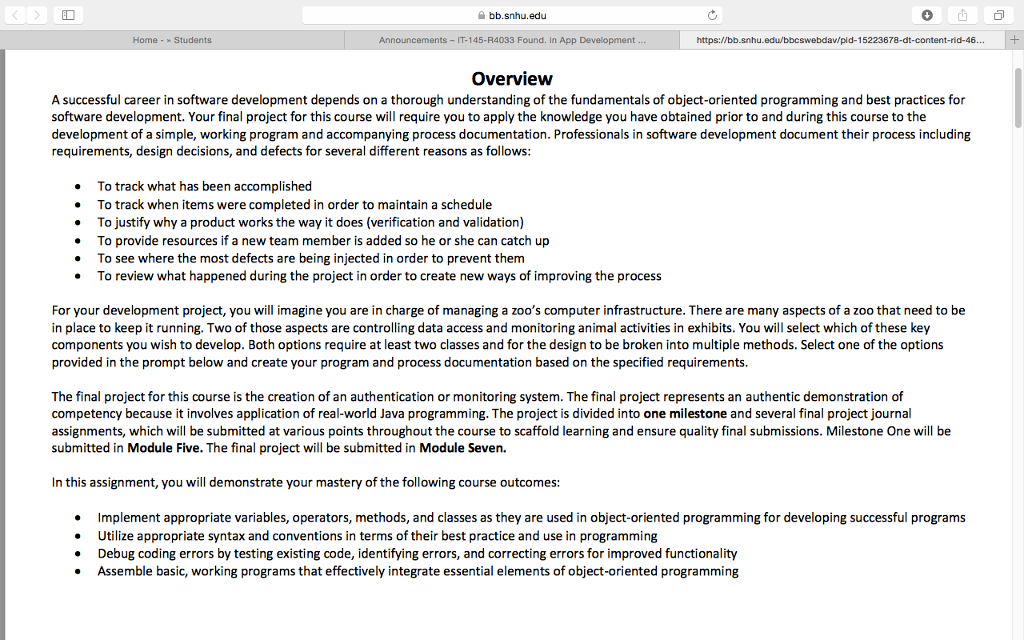
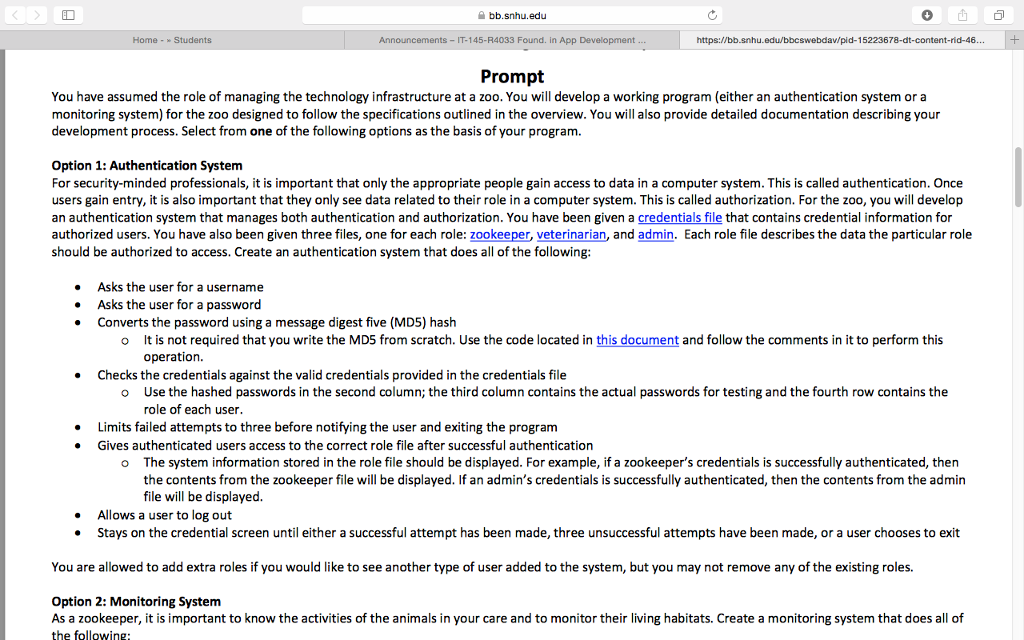
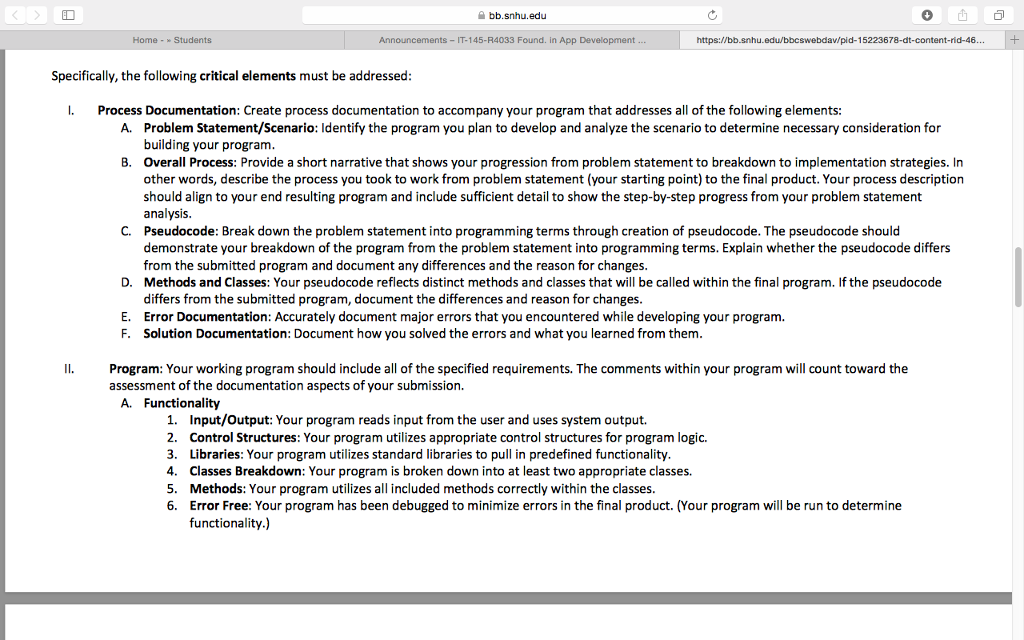
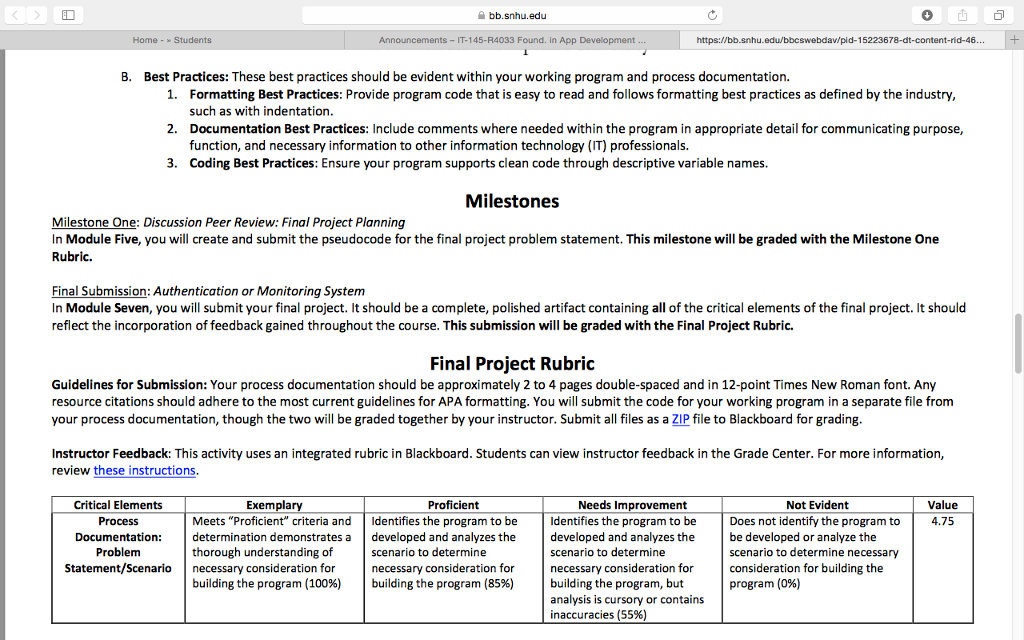
bb.snhu.edu Home Students Announcements 45-R4033 Found. in App Development https://bb.snhu edu/bbcswebdav/pid-15223678-dt content-rid-465. Overview A successful career in software development depends on a thorough understanding of the fundamentals of object-oriented programming and best practices for software development. Your final project for this course will require you to apply the knowledge you have obtained prior to and during this course to the development of a simple, working program and accompanying process documentation. Professionals in software development document their process including requirements, design decisions, and defects for several different reasons as follows: To track what has been accomplished To track when items were completed in order to maintain a schedule To justify why a product works the way it does (verification and validation) To provide resources if a new team member is added so he or she can catch up To see where the most defects are being injected in order to prevent them To review what happened during the project in order to create new ways of improving the process For your development project, you will imagine you are in charge of managing a zoo's computer infrastructure. There are many aspects of a zoo that need to be in place to keep it running. Two of those aspects are controlling data access and monitoring animal activities in exhibits. You will select which of these key components you wish to develop. Both options require at least two classes and for the design to be broken into multiple methods. Select one of the options provided in the prompt below and create your program and process documentation based on the specified requirements. The final project for this course is the creation of an authentication or monitoring system. The final project represents an authentic demonstration of competency because it involves application of real-world Java programming. The project is divided into one milestone and several final project journal assignments, which will be submitted at various points throughout the course to scaffold learning and ensure quality final submissions. Milestone One will be submitted in Module Five. The final project will be submitted in Module Seven. In this assignment, you will demonstrate your mastery of the following course outcomes Implement appropriate variables, operators, methods, and classes as they are used in object-oriented programming for developing successful programs Utilize appropriate syntax and conventions in terms of their best practice and use in programming Debug coding errors by testing existing code, identifying errors, and correcting errors for improved functionality Assemble basic, working programs that effectively integrate essential elements of object-oriented programming bb.snhu.edu Home Students Announcements 45-R4033 Found. in App Development https://bb.snhu edu/bbcswebdav/pid-15223678-dt content-rid-465. Overview A successful career in software development depends on a thorough understanding of the fundamentals of object-oriented programming and best practices for software development. Your final project for this course will require you to apply the knowledge you have obtained prior to and during this course to the development of a simple, working program and accompanying process documentation. Professionals in software development document their process including requirements, design decisions, and defects for several different reasons as follows: To track what has been accomplished To track when items were completed in order to maintain a schedule To justify why a product works the way it does (verification and validation) To provide resources if a new team member is added so he or she can catch up To see where the most defects are being injected in order to prevent them To review what happened during the project in order to create new ways of improving the process For your development project, you will imagine you are in charge of managing a zoo's computer infrastructure. There are many aspects of a zoo that need to be in place to keep it running. Two of those aspects are controlling data access and monitoring animal activities in exhibits. You will select which of these key components you wish to develop. Both options require at least two classes and for the design to be broken into multiple methods. Select one of the options provided in the prompt below and create your program and process documentation based on the specified requirements. The final project for this course is the creation of an authentication or monitoring system. The final project represents an authentic demonstration of competency because it involves application of real-world Java programming. The project is divided into one milestone and several final project journal assignments, which will be submitted at various points throughout the course to scaffold learning and ensure quality final submissions. Milestone One will be submitted in Module Five. The final project will be submitted in Module Seven. In this assignment, you will demonstrate your mastery of the following course outcomes Implement appropriate variables, operators, methods, and classes as they are used in object-oriented programming for developing successful programs Utilize appropriate syntax and conventions in terms of their best practice and use in programming Debug coding errors by testing existing code, identifying errors, and correcting errors for improved functionality Assemble basic, working programs that effectively integrate essential elements of object-oriented programmingStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


