Answered step by step
Verified Expert Solution
Question
1 Approved Answer
This is how the professor told the students how to approach the program. Somewhat this way. All in one file. Write a complete program that

This is how the professor told the students how to approach the program. Somewhat this way. All in one file.
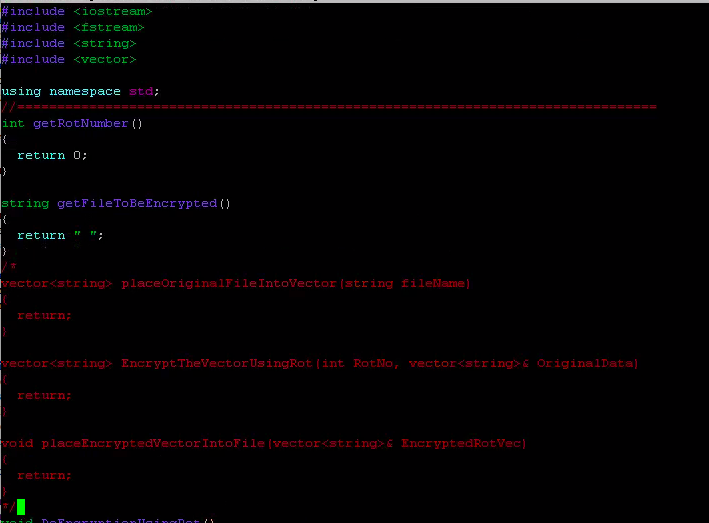
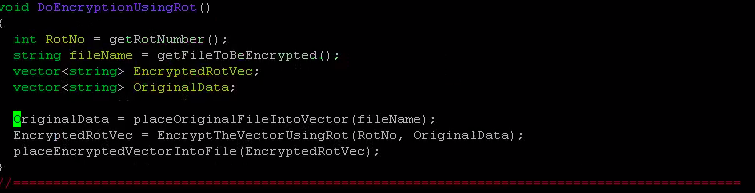
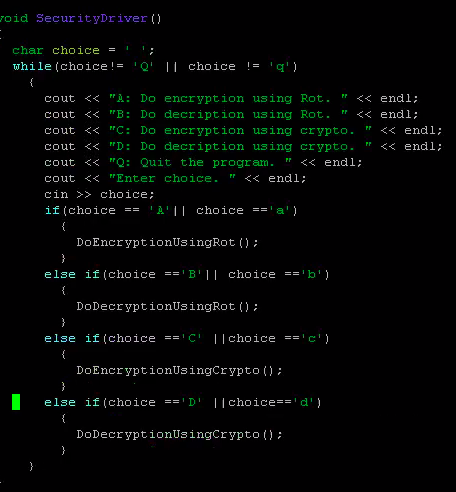
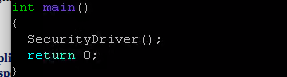
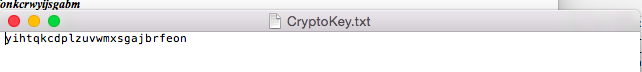
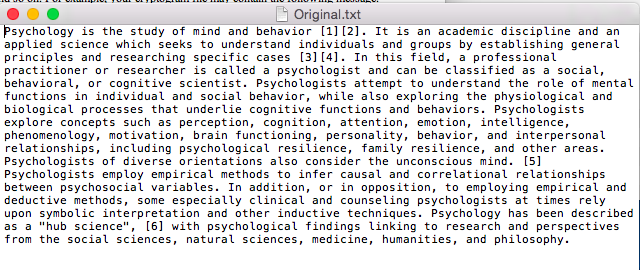
Write a complete program that performs encryption/decryption of a text file. Encryption means you need to scramble the words of a file to become secure. Decryption means you need to apply some rules to an encrypted file in order to find the original file with its original content. An example of encryption is to replace each letter in a file with its consecutive letter in the alphabet. Therefore, a, is replaced by b','b' is replaced byand so on and finally z' is replaced by 'a'. Thus, if the file contains the following message: I am a student at csusmm The encrypted message becomes: Then if you get this encrypted message and the key is 1 it means you need to shift the alphabets in the decrypted message by 1 to the left to get the original message back. This method is called "rotl" indicating that every alphabet rotates by 1 during the encryption. Similarly, rot10 means every alphabet should be rotated by 10 during encryption. Another method of encryption is to create cryptogram. A cryptogram is a message or word where each letter is replaced with another letter. For example, the string: The birds name was squawk might be scrambled to form Note that space or any punctuation is not scrambled. In this particular case, "T, was replaced with X, each 'a, was replaced with h. etc. we assume there is no difference between lower case or uppercase. Therefore, you must turn all of the letters of a word into lower case before encrypt it. For example, if your work is "McMaster, the function (word-"tolower("McMaster") makes word to be equal to "mcmaster" Your job is to write a driver program (look at the program guide to see how to create a driver program) that performs different types of encryption or description. First, you need to ask the user to see if the user wants to do encryption or decryption. If the user wants to do encryption, you should find out if the user wants to use "rot" method or cryptogram method. If the user selects the "rot" method, you need to ask for the encryption key. For example, entering 15, means that the user wants to use "rotl5" method to do encryption. If the user selects the cryptogram method, you should open the cryptogram text file called "CryptoKey" where the cryptogram string is stored. The cryptogram string should contain a string of 26 letters where the first letter corresponds to letter 'a', the second letter corresponds to letter "b' and so on. For example, your cryptogram file may contain the following message. uhtxvdepqkfonkcrwyijsgabm which means u' corresponds to 'a' 'h' corresponds to 'b' and and finally 'm' corresponds to 'z' The same procedure should be followed for decryption. You need to ask the user which method the user wants to use (rot or cryptogram) for encryption. Then write the routines that takes an encrypted file and does the decryption to get the original file back. You are responsible to use string and vector class in this program. For encryption, you need to read the file to be encrypted into a vector of string and place the words (one word per element) into a vector. Then read the elements of your vector one by one and do the encryption and place the encrypted word into another vector. Finally write the content of encrypted vector to an output file. For decryption, you need to do the same process which is read the file that contains the encrypted information and place the encrypted words one by one into a vector. Then create another vector so that as you decrypt the information you can place the decrypted words into another vector. Finally, the vector that contains the decrypted words (original message) should be written to an output file
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


