Question
Understanding Networks and Drawing a Network Diagram: Please review the following assignment. I am not sure how to draw the network diagram for this assignment.
Understanding Networks and Drawing a Network Diagram:
Please review the following assignment. I am not sure how to draw the network diagram for this assignment. How do I go about drawing this? Thanks.

Here is our network discovery plan:
Network discovery plan:
The route that our group took to plan to discover our network was to first use nmap to find the available hosts on the network.
Once we have that information we can find out what type of services the host offers and also the type of operating system running.
So the first command used was nmap ipaddr.
We then used Sparta to scan the hosts that were found on our subnet.
The results that was given by using Sparta was the lists of services running, the number of open ports, and the operating systems running using each scan.
The first scan that Sparta completes is the nmap scan then after it follows to run additional tools against the discovered services.
Traceroute is also a command we used when trying to come up with our network discovery plan.
This command shows the path a packet of information takes from your computer to one you specify.
It will list all the routers it passes through until it reaches its destination, or fails to and is discarded.
The info given is broken down into numbers.
1 is the internet gateway on the network the traceroute was done from, 2 is the ISP the origin computer is connected to.
3 is the extra network, 4 is timed out, etc,.
By using all of these command we would have enough information to come up with our network diagram with the proper routers, hosts, and ports available on the given network.
zenmap screenshot
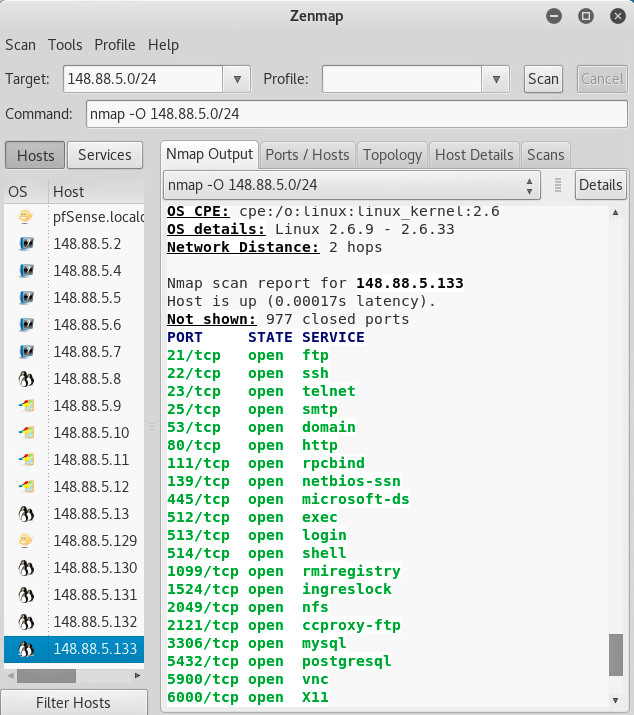
zenmap fisheye:
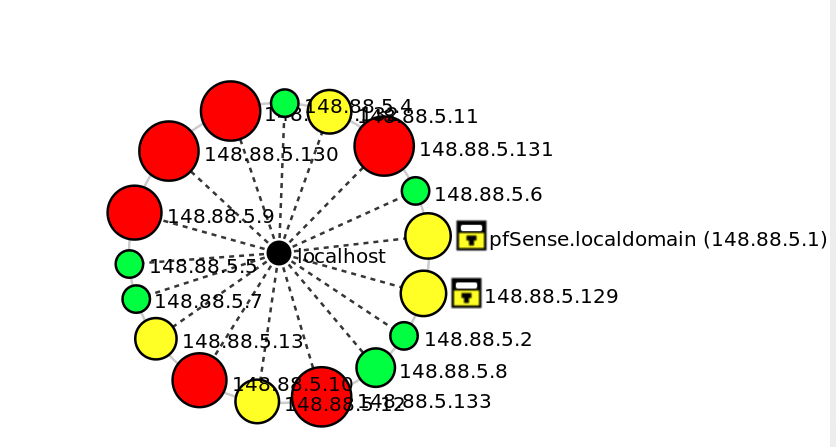
Activity 3 Group activity Using Nmap, Sparta, traceroute and any other tools available in Kali as your guide i. Draw a Network Diagram of your group's subnet. Include routers, switches, gateways hosts(workstations), servers, IP addresses Open ports and port services for all servers can be included in the diagram or in a separate table 2. Create a document that: i. Using the NVD, CVE and any other sources. List vulnerability for each Server or ii. Describe your plan to discover the network and the commands used in development of iii. In your description include an explanation of what worked and more importantly what iv. Next week you will need to explore the vulnerabilities and locate exploits to use against workstation found, ignore the Kali workstations. your network diagram didn't work and why e network Zenmap Scan Tools Profile Help Target: 148.88.5.0/24 Command: nmap -O 148.88.5.0/24 v Profile: Scan Cancel Hosts Services Nmap Output Ports / Hosts Topology Host Details Scans nmap -o 148.88.5.0/24 os CPE: :/o: linux : linuxkernel : 2.6 oS details: Linux 2.6.9- 2.6.33 Network Distance: 2 hops OS Host Details pfSense.local OS 148.88.5.2 148.88.5.4 148.88.5.5 148.88.5.6 148.88.5.7 - Nmap scan report for 148.88.5.133 Host is up (0.00017s latency). Notshown: 977 closed ports PORT 21/tcp open ftp 22/tcp ope ssh 23/tcp open telnet 25/tcp open smtp STATE SERVICE 148.88.5.8 148.88.5.9 148.88.5.10 53/tcp open domairn 80/tcp open http 139/tcp 445/tcp open microsoft-ds 148.88.5.12 open netbios-ssn 148.88.5.13 512/tcp open exec 148.88.5.129 513/tcp open login 148.88.5.130 1099/tcp open rmiregist 514/tcp open shell 1524/tcp open ingreslock 2049/tcp open nfs 3) 148.88.5.132 2121/tcp open ccproxy-ftp 6 148.88.5.133 3306/tcp open mysq 5432/tcp open postgresql 5900/tcp open vnc 6000/tcp open X11 Filter Hosts 8.5.11 148.88.5.131 148:88.5.130 .148.885.9 TpfSense.localdomain (148.88.5.1) T148.88.5.129 1 148.88.5.2 148.88.5.13. 148.88.5.8 5.1 48.8854B288.5.133 Activity 3 Group activity Using Nmap, Sparta, traceroute and any other tools available in Kali as your guide i. Draw a Network Diagram of your group's subnet. Include routers, switches, gateways hosts(workstations), servers, IP addresses Open ports and port services for all servers can be included in the diagram or in a separate table 2. Create a document that: i. Using the NVD, CVE and any other sources. List vulnerability for each Server or ii. Describe your plan to discover the network and the commands used in development of iii. In your description include an explanation of what worked and more importantly what iv. Next week you will need to explore the vulnerabilities and locate exploits to use against workstation found, ignore the Kali workstations. your network diagram didn't work and why e network Zenmap Scan Tools Profile Help Target: 148.88.5.0/24 Command: nmap -O 148.88.5.0/24 v Profile: Scan Cancel Hosts Services Nmap Output Ports / Hosts Topology Host Details Scans nmap -o 148.88.5.0/24 os CPE: :/o: linux : linuxkernel : 2.6 oS details: Linux 2.6.9- 2.6.33 Network Distance: 2 hops OS Host Details pfSense.local OS 148.88.5.2 148.88.5.4 148.88.5.5 148.88.5.6 148.88.5.7 - Nmap scan report for 148.88.5.133 Host is up (0.00017s latency). Notshown: 977 closed ports PORT 21/tcp open ftp 22/tcp ope ssh 23/tcp open telnet 25/tcp open smtp STATE SERVICE 148.88.5.8 148.88.5.9 148.88.5.10 53/tcp open domairn 80/tcp open http 139/tcp 445/tcp open microsoft-ds 148.88.5.12 open netbios-ssn 148.88.5.13 512/tcp open exec 148.88.5.129 513/tcp open login 148.88.5.130 1099/tcp open rmiregist 514/tcp open shell 1524/tcp open ingreslock 2049/tcp open nfs 3) 148.88.5.132 2121/tcp open ccproxy-ftp 6 148.88.5.133 3306/tcp open mysq 5432/tcp open postgresql 5900/tcp open vnc 6000/tcp open X11 Filter Hosts 8.5.11 148.88.5.131 148:88.5.130 .148.885.9 TpfSense.localdomain (148.88.5.1) T148.88.5.129 1 148.88.5.2 148.88.5.13. 148.88.5.8 5.1 48.8854B288.5.133
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


