Use vmware ubnutu to set up
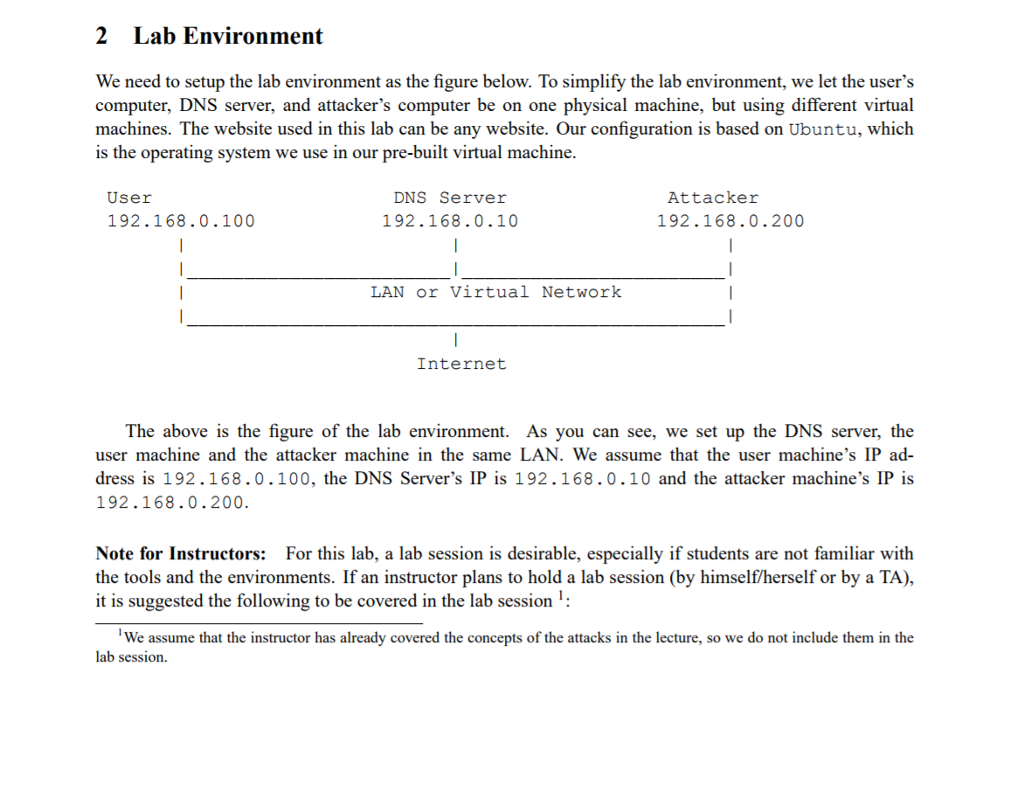



2 Lab Environment We need to setup the lab environment as the figure below. To simplify the lab environment, we let the user's computer, DNS server, and attacker's computer be on one physical machine, but using different virtual machines. The website used in this lab can be any website. Our configuration is based on Ubuntu, which is the operating system we use in our pre-built virtual machine. User 192.168.0.100 DNS Server 192.168.0.10 Attacker 192.168.0.200 LAN or Virtual Network Internet The above is the figure of the lab environment. As you can see, we set up the DNS server, the user machine and the attacker machine in the same LAN. We assume that the user machine's IP ad- dress is 192.168.0.100, the DNS Server's IP is 192.168.0.10 and the attacker machine's IP is 192.168.0.200 Note for Instructors: For this lab, a lab session is desirable, especially if students are not familiar with the tools and the environments. If an instructor plans to hold a lab session (by himself/herself or by a TA), it is suggested the following to be covered in the lab session: We assume that the instructor has already covered the concepts of the attacks in the lecture, so we do not include them in the lab session 2 Lab Environment We need to setup the lab environment as the figure below. To simplify the lab environment, we let the user's computer, DNS server, and attacker's computer be on one physical machine, but using different virtual machines. The website used in this lab can be any website. Our configuration is based on Ubuntu, which is the operating system we use in our pre-built virtual machine. User 192.168.0.100 DNS Server 192.168.0.10 Attacker 192.168.0.200 LAN or Virtual Network Internet The above is the figure of the lab environment. As you can see, we set up the DNS server, the user machine and the attacker machine in the same LAN. We assume that the user machine's IP ad- dress is 192.168.0.100, the DNS Server's IP is 192.168.0.10 and the attacker machine's IP is 192.168.0.200 Note for Instructors: For this lab, a lab session is desirable, especially if students are not familiar with the tools and the environments. If an instructor plans to hold a lab session (by himself/herself or by a TA), it is suggested the following to be covered in the lab session: We assume that the instructor has already covered the concepts of the attacks in the lecture, so we do not include them in the lab session










