using emu8086 in assembly language
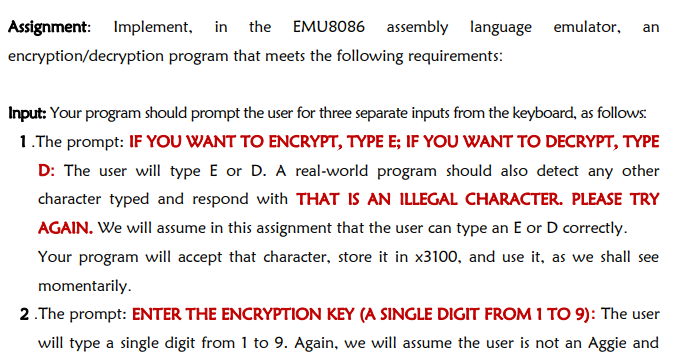

Assignment: Implement, in the EMU8086 assembly language emulator, an encryption/decryption program that meets the following requirements: Input: Your program should prompt the user for three separate inputs from the keyboard, as follows: 1. The prompt: IF YOU WANT TO ENCRYPT, TYPE E; IF YOU WANT TO DECRYPT, TYPE D: The user will type E or D. A real-world program should also detect any other character typed and respond with THAT IS AN ILLEGAL CHARACTER. PLEASE TRY AGAIN. We will assume in this assignment that the user can type an E or D correctly. Your program will accept that character, store it in 3100, and use it, as we shall see momentarily. 2 .The prompt: ENTER THE ENCRYPTION KEY (A SINGLE DIGIT FROM1 TO 9): The user will type a single digit from 1 to 9. Again, we will assume the user is not an Aggie and can successfully hit the digit keys on the keyboard. Your program will accept this digit, store it in 3101, and use it to encrypt or decrypt the message. 3 . The prompt: INPUT A MESSAGE OF NO MORE THAN 20 CHARACTERS. WHEN DONE, PRESS >. The user will input a character string from the keyboard, terminating the message with the ENTER > key. Your program will store the message, starting in location 3102. Since the message is restricted to \# 20 characters, and there is a key at the end (which you may want to store), you must reserve locations x3102 to x3116 (\#21 locations) to store the message. (Note that \#21 =x15.) One constraint: Messages must be less than or equal to \#20 characters. (Recall: \# means the number is decimal.) Hint: to continually read from the keyboard without first printing a prompt on the screen, use the appropriate interrupt (such as INT 21). For each key you wish to read, the EMU8086 operating system must execute this interrupt service routine. Don't forget to follow the input interrupt with the instruction for interrupt for output, the character the user types will be displayed on the screen. Algorithm: Shift Cipher Scheme (SCS) The shift Cipher algorithm is one of the simplest and most widely used monoalphabetic incryption algorithms. In this algorithm, every alphabetical character in the plaintext is eplaced by a character/letter with a fixed number of positions down the alphabet. The encryption algorithm is as follows. he provided key value has incremented every letter of the plaintext (We subtract the value of the key from the value of the letter). For an example, consider the following plain text. Plain Text: ABCDEF Key: 3 Cipher Text: DEFGHI The decryption algorithm is the reverse. That is, "he same procedure is carried out in decryption, but the difference is that the value of the iey is decreased from the ciphertext to get the respective plain text (We subtract the value of he key from the value of the letter). For an example, consider the following ciphertext. Cipher Text: DEFGHI Key: 3 Plain Text: ABCDEF Dutput: Your program should output the encrypted or decrypted message to the screen. Note that








