Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Web Application Vulnerabilities Participants in the case study CTO: Executive of the company CISO: Security Specialist Case Study The CTO was an executive at

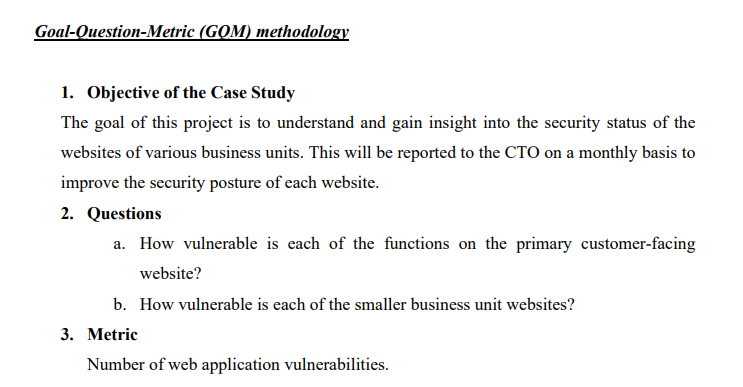
Web Application Vulnerabilities Participants in the case study CTO: Executive of the company CISO: Security Specialist Case Study The CTO was an executive at the company responsible for overseeing web site development of several distinct business units. The CISO was responsible for security of each of these business units. The CTO and the CISO already had a good working relationship. Although the CTO was not an expert in security, the CTO trusted the CISO for his security recommendations in this area. The CTO approached the CISO asking for information about the security status of each of the web sites. Specifically, the CTO was interested in using a security metric to improve the security posture of each of the web sites, something that could be tracked month after month to improve the sites' security posture. Goal-Question-Metric (GOM) methodology 1. Objective of the Case Study The goal of this project is to understand and gain insight into the security status of the websites of various business units. This will be reported to the CTO on a monthly basis to improve the security posture of each website. 2. Questions a. How vulnerable is each of the functions on the primary customer-facing website? b. How vulnerable is each of the smaller business unit websites? 3. Metric Number of web application vulnerabilities.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


