Question
What are the tools available to do the web application testing? Listed down and select any web application tool and try to find out what
- What are the tools available to do the web application testing? Listed down and select any web application tool and try to find out what the features are and how to use in testing?
- username" & "password" fields then what are the things required to perform the SQL injection
- How to prevent SQL injection attacks?
- Difference between encryption, encoding and Hashing?
- What is Xss or cross site scripting and types of XSS?
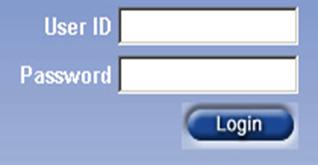
- You are engaged in a penetration-test where you are attempting to gain access to a protected location. You are presented with this login screen Which OWASP top 10 attack will help you and how you would attempt to gain access?
7. Which type of attack its belongs to and why as per the below example?
- An attacker uses scans for users using a common password. They can take over all accounts using this password. For all other users, this scan leaves only one false login behind. After some days, this may be repeated with a different password.
- A web server running older version of apache struts2 which is having remote code execution vulnerability that enables execution of arbitrary code on the server.
- A user uses a public computer to access an application. Instead of selecting "logout" the user simply closes the browser tab and walks away. An attacker uses the same browser an hour later, and the user is still authenticated.
- A sensitive's directory or files are open on websites for everyone to view and it is not disabled on the server. An attacker discovers they can simply access the directories. The attacker finds and downloads the compiled Java classes files, which they decompile and reverse engineer to view the code. The attacker then finds a serious access control flaw in the application.
8. What are the major changes in OWASP top 10 2013 vs 2017?
User ID Password Login
Step by Step Solution
There are 3 Steps involved in it
Step: 1
1Web Application Testing Tools Some popular web application testing tools include Selenium Burp Suite OWASP ZAP JMeter and Postman Lets take Selenium as an example Selenium is widely used for function...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


