what changes we should make in the penetration test contract? using this penetration contract example 
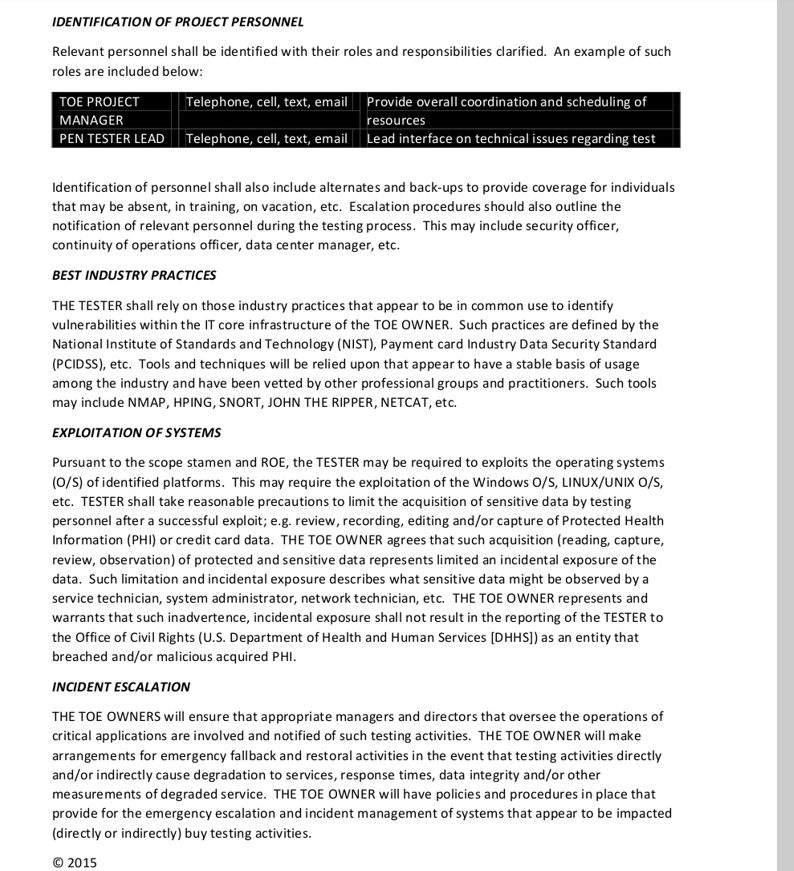
SAMPLE PENETRATION TESTING ENGAGEMENT LETTER PARTIES This document formalizes the relationship between the two parties; herein known as the TESTER and the entity that owns and operates the TARGET OF EVALUATION (TOE). THE TESTER is a consulting and professional services entity that shall perform an operational check of the TOE. This operational check shall be focused on the security vulnerabilities embedded with the Information Technology (IT) core infrastructure of the TOE. The TESTER will use tools as identified as leading industry practices to measure the vulnerabilities associated with various configurations of IT core infrastructure with the TOE. THE TOE OWNER is the entity that leases, operates, controls or maintains the TOE. The TOE OWNER warrants that it has the authority and responsibility to authorize testing of the TOE. Such testing may include evaluations of the vulnerabilities that may reside in IT core infrastructure appliances, servers, cloud based systems, etc. SCOPE STATEMENT The parties agree to define a mutual SCOPE STATEMENT that shall define the general parameters of the testing to be executed. Such parameters should define tangible and measurable boundaries that carve out the IT core infrastructure that shall comprise the TOE. For example, Internet Protocol (IP) address ranges, identification of servers (by system name and IP address), exposed web servers to be tested for application level vulnerabilities, identification of infrastructure appliances that shall be test for routing and networking vulnerabilities, wireless (Wi-Fi) access points that shall be test, remote access points (RADIUS, dial-in, VPN, etc.). The scope statement shall identify associated and ancillary infrastructure that is relied upon by the TOE owner; but, may not have formal permission to commit to such testing. Example of ancillary infrastructure may include supporting Internet-based domain name services (DNS), I.P. routing, application-level firewalls maintained to filter out Web-based attacks, infrastructure maintained by an Internet Services Provider (ISP) or cable company, etc. All such infrastructure that is not under the direct control of the TOE OWNER shall be identified and included in the scope statement to allow for arrangements to be made with such infrastructure providers. RULES OF ENGAGEMENT A separate formalized document shall be agreed upon that describes the rules of engagement (ROE) that shall govern the execution. ROE shall cover the impact and magnitude of testing, types of testing to be conducted, interactions with TOE OWNERS employees, consultants and ancillary experts. Thresholds of activity to include when notification to the TOE OWNER Project manager is necessary, etc. ROE also provides the protocols for addressing concerns and issue of a human resource and personnel issue (cooperation of employees, social engineering tests, red team tests, etc.). 2015 IDENTIFICATION OF PROJECT PERSONNEL Relevant personnel shall be identified with their roles and responsibilities clarified. An example of such roles are included below: TOE PROJECT Telephone, cell, text, email Provide overall coordination and scheduling of MANAGER resources PEN TESTER LEAD Telephone, cell, text, email Lead interface on technical issues regarding test Identification of personnel shall also include alternates and back-ups to provide coverage for individuals that may be absent, in training, on vacation, etc. Escalation procedures should also outline the notification of relevant personnel during the testing process. This may include security officer, continuity of operations officer, data center manager, etc. BEST INDUSTRY PRACTICES THE TESTER shall rely on those industry practices that appear to be in common use to identify vulnerabilities within the IT core infrastructure of the TOE OWNER. Such practices are defined by the National Institute of Standards and Technology (NIST), Payment card Industry Data Security Standard (PCIDSS), etc. Tools and techniques will be relied upon that appear to have a stable basis of usage among the industry and have been vetted by other professional groups and practitioners. Such tools may include NMAP, HPING, SNORT, JOHN THE RIPPER, NETCAT, etc. EXPLOITATION OF SYSTEMS Pursuant to the scope stamen and ROE, the TESTER may be required to exploits the operating systems (0/S) of identified platforms. This may require the exploitation of the Windows O/S, LINUX/UNIX O/S, etc. TESTER shall take reasonable precautions to limit the acquisition of sensitive data by testing personnel after a successful exploit; e.g. review, recording, editing and/or capture of Protected Health Information (PHI) or credit card data. THE TOE OWNER agrees that such acquisition (reading, capture, review, observation) of protected and sensitive data represents limited an incidental exposure of the data. Such limitation and incidental exposure describes what sensitive data might be observed by a service technician, system administrator, network technician, etc. THE TOE OWNER represents and warrants that such inadvertence, incidental exposure shall not result in the reporting of the TESTER to the Office of Civil Rights (U.S. Department of Health and Human Services (DHHS]) as an entity that breached and/or malicious acquired PHI. INCIDENT ESCALATION THE TOE OWNERS will ensure that appropriate managers and directors that oversee the operations of critical applications are involved and notified of such testing activities. THE TOE OWNER will make arrangements for emergency fallback and restoral activities in the event that testing activities directly and/or indirectly cause degradation to services, response times, data integrity and/or other measurements of degraded service. THE TOE OWNER will have policies and procedures in place that provide for the emergency escalation and incident management of systems that appear to be impacted (directly or indirectly) buy testing activities. 2015 SAMPLE PENETRATION TESTING ENGAGEMENT LETTER PARTIES This document formalizes the relationship between the two parties; herein known as the TESTER and the entity that owns and operates the TARGET OF EVALUATION (TOE). THE TESTER is a consulting and professional services entity that shall perform an operational check of the TOE. This operational check shall be focused on the security vulnerabilities embedded with the Information Technology (IT) core infrastructure of the TOE. The TESTER will use tools as identified as leading industry practices to measure the vulnerabilities associated with various configurations of IT core infrastructure with the TOE. THE TOE OWNER is the entity that leases, operates, controls or maintains the TOE. The TOE OWNER warrants that it has the authority and responsibility to authorize testing of the TOE. Such testing may include evaluations of the vulnerabilities that may reside in IT core infrastructure appliances, servers, cloud based systems, etc. SCOPE STATEMENT The parties agree to define a mutual SCOPE STATEMENT that shall define the general parameters of the testing to be executed. Such parameters should define tangible and measurable boundaries that carve out the IT core infrastructure that shall comprise the TOE. For example, Internet Protocol (IP) address ranges, identification of servers (by system name and IP address), exposed web servers to be tested for application level vulnerabilities, identification of infrastructure appliances that shall be test for routing and networking vulnerabilities, wireless (Wi-Fi) access points that shall be test, remote access points (RADIUS, dial-in, VPN, etc.). The scope statement shall identify associated and ancillary infrastructure that is relied upon by the TOE owner; but, may not have formal permission to commit to such testing. Example of ancillary infrastructure may include supporting Internet-based domain name services (DNS), I.P. routing, application-level firewalls maintained to filter out Web-based attacks, infrastructure maintained by an Internet Services Provider (ISP) or cable company, etc. All such infrastructure that is not under the direct control of the TOE OWNER shall be identified and included in the scope statement to allow for arrangements to be made with such infrastructure providers. RULES OF ENGAGEMENT A separate formalized document shall be agreed upon that describes the rules of engagement (ROE) that shall govern the execution. ROE shall cover the impact and magnitude of testing, types of testing to be conducted, interactions with TOE OWNERS employees, consultants and ancillary experts. Thresholds of activity to include when notification to the TOE OWNER Project manager is necessary, etc. ROE also provides the protocols for addressing concerns and issue of a human resource and personnel issue (cooperation of employees, social engineering tests, red team tests, etc.). 2015 IDENTIFICATION OF PROJECT PERSONNEL Relevant personnel shall be identified with their roles and responsibilities clarified. An example of such roles are included below: TOE PROJECT Telephone, cell, text, email Provide overall coordination and scheduling of MANAGER resources PEN TESTER LEAD Telephone, cell, text, email Lead interface on technical issues regarding test Identification of personnel shall also include alternates and back-ups to provide coverage for individuals that may be absent, in training, on vacation, etc. Escalation procedures should also outline the notification of relevant personnel during the testing process. This may include security officer, continuity of operations officer, data center manager, etc. BEST INDUSTRY PRACTICES THE TESTER shall rely on those industry practices that appear to be in common use to identify vulnerabilities within the IT core infrastructure of the TOE OWNER. Such practices are defined by the National Institute of Standards and Technology (NIST), Payment card Industry Data Security Standard (PCIDSS), etc. Tools and techniques will be relied upon that appear to have a stable basis of usage among the industry and have been vetted by other professional groups and practitioners. Such tools may include NMAP, HPING, SNORT, JOHN THE RIPPER, NETCAT, etc. EXPLOITATION OF SYSTEMS Pursuant to the scope stamen and ROE, the TESTER may be required to exploits the operating systems (0/S) of identified platforms. This may require the exploitation of the Windows O/S, LINUX/UNIX O/S, etc. TESTER shall take reasonable precautions to limit the acquisition of sensitive data by testing personnel after a successful exploit; e.g. review, recording, editing and/or capture of Protected Health Information (PHI) or credit card data. THE TOE OWNER agrees that such acquisition (reading, capture, review, observation) of protected and sensitive data represents limited an incidental exposure of the data. Such limitation and incidental exposure describes what sensitive data might be observed by a service technician, system administrator, network technician, etc. THE TOE OWNER represents and warrants that such inadvertence, incidental exposure shall not result in the reporting of the TESTER to the Office of Civil Rights (U.S. Department of Health and Human Services (DHHS]) as an entity that breached and/or malicious acquired PHI. INCIDENT ESCALATION THE TOE OWNERS will ensure that appropriate managers and directors that oversee the operations of critical applications are involved and notified of such testing activities. THE TOE OWNER will make arrangements for emergency fallback and restoral activities in the event that testing activities directly and/or indirectly cause degradation to services, response times, data integrity and/or other measurements of degraded service. THE TOE OWNER will have policies and procedures in place that provide for the emergency escalation and incident management of systems that appear to be impacted (directly or indirectly) buy testing activities. 2015








