Question
What type of attack is this? Explain it as per the image below Bob Darth read contents of message from Bob to Alice Internet
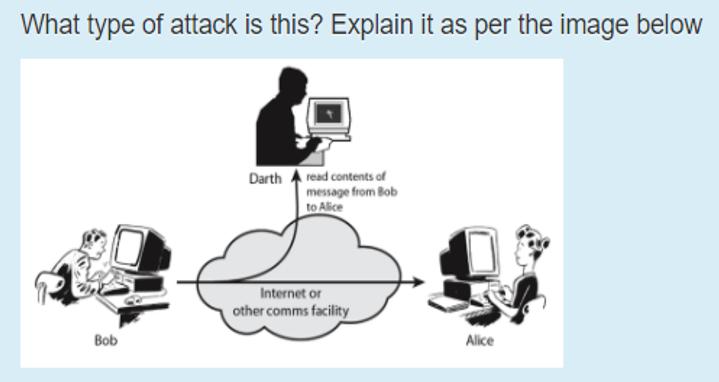
What type of attack is this? Explain it as per the image below Bob Darth read contents of message from Bob to Alice Internet or other comms facility Alice
Step by Step Solution
There are 3 Steps involved in it
Step: 1
The image depicts a maninthemiddle MITM attack This type of cyberattack occurs when an attacker posi...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get StartedRecommended Textbook for
Cryptography And Network Security
Authors: William Stallings
5th Edition
B00F0ZR6PC, 9780136097044
Students also viewed these Programming questions
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
View Answer in SolutionInn App



