Answered step by step
Verified Expert Solution
Question
1 Approved Answer
whats the complete program implementation, of both ways dynamic programming and brute force in java please Ms. Abeer is arranging for a professional training program.
whats the complete program implementation, of both ways dynamic programming and brute force 

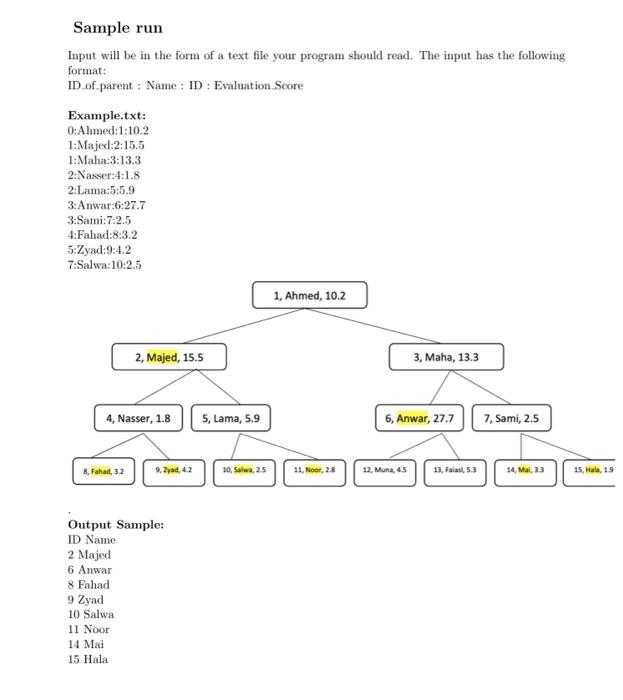
in java please
Ms. Abeer is arranging for a professional training program. The hierarchical structure of the university forms a tree rooted at the university's chief executive officer. The employees are ranked by the HR office based on their evaluation, which is a real number. In order to make the best utilization of the program, the chief executive officer does not want both an employee and his or her immediate head to attend. Ms. Abeer is given the tree that describes the structure of the university, using the tree data structure. Each node of the tree holds, in addition to the pointers, the name and evaluation-based ranking of an employee. Assume a complete binary tree. Describe two algorithms to make up a program registration offer list that maximizes the sum of the evaluation-based ratings of the employees such that an employee does not attend with his/her immediate head, using Brute Force and Dynamic Programming. Analyze the running time of your algorithms. Sample run Innut will he in the form of a text file vour nrooram ehould read. The innut has the following Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


