Answered step by step
Verified Expert Solution
Question
1 Approved Answer
With the use of link encryption, network - layer headers ( e . g . , frame or cell header ) are encrypted, reducing the
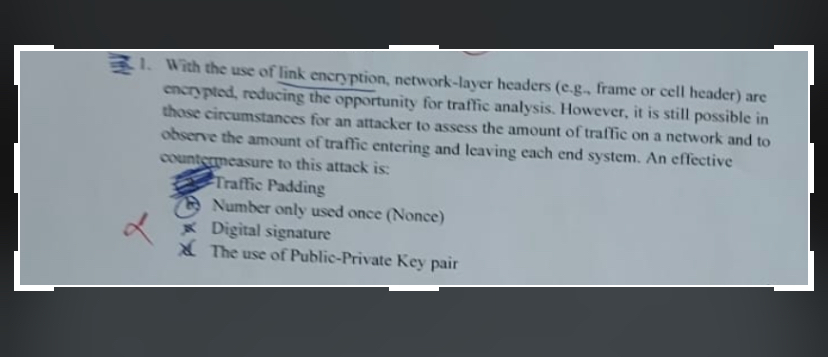
With the use of link encryption, networklayer headers eg frame or cell header are encrypted, reducing the opportunity for traffic analysis. However, it is still possible in those circumstances for an attacker to assess the amount of traffic on a network and to observe the amount of traffic entering and leaving each end system. An effective count gtmeasure to this attack is:
Traftic Padding
W Number only used once Nonce
x Digital signature
X The use of PublicPrivate Key pair
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


