Question
write 600 words regarding following Journal must be analysis to cover all topic also following the next point : - the topic is current and


write 600 words regarding following Journal must be analysis to cover all topic also following the next point :
- the topic is current and relevant
- the article cover the topic comprehensively, partially, or provide an overview
-Is the material organized and focused
-Is the argument or presentation understandable
-Is this an informative piece
Dont simply copy the content (% of similarity)
Adherence to prescribed format
Article without language errors
Scholarly works always contain a bibliography of resources that were consulted. This reference list should be in sufficient quantity and appropriate for the content.
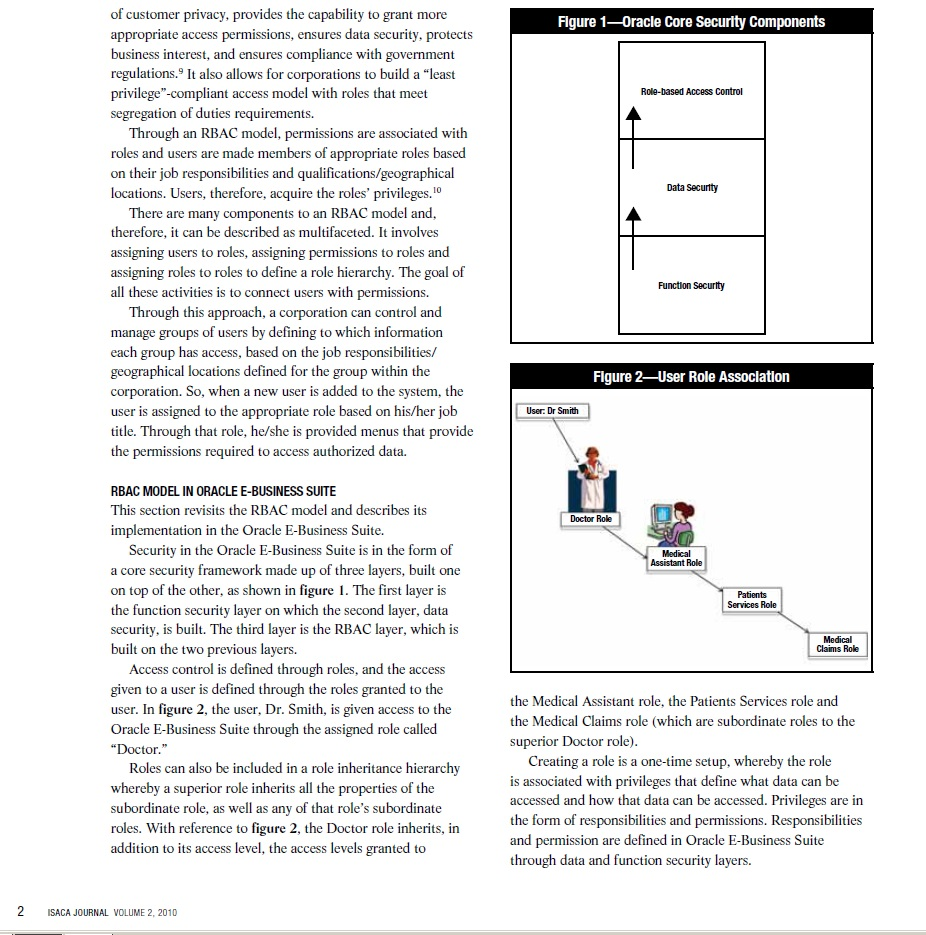
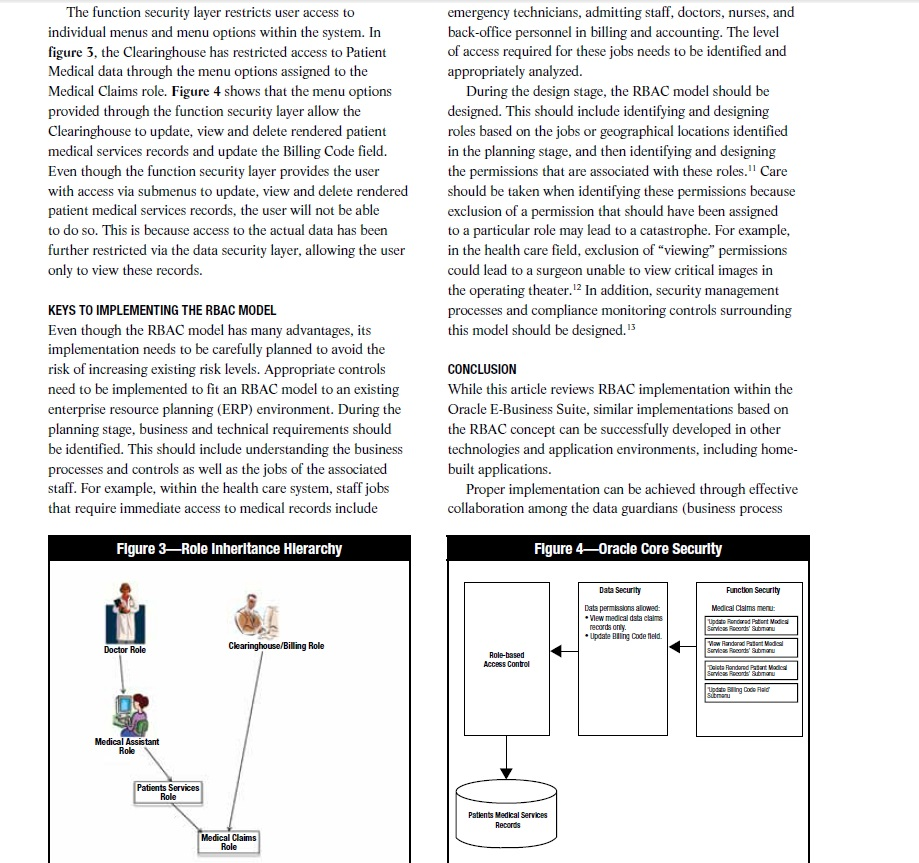
Journal Online Application Security Using the Role-based Access Control Model Ronke has more than 13 years of expenence working In th consuting Industry. Her areas of expartse Include IT aud and security, software Ife cycle and Sarbanes-Oodey comp ance. She has worked weth fims such as Emst &Young and Daloltte. Oyemade also ls an Instructor, who has traned employees ot Forine 500 companles, such as Coca Cola and Johnsona Johnson. She was the lead Instuctor at the ISACA Atanta Chapter's Oracle Audit tralning session n October 2009. She can be reached at share. In addition, corporations may be faced with the need to comply with privacy regulations such as the US Health Insurance Portability and Accountability Act (HIPAA)! set of three components: . Technology infrastructure security, which involves securing the network and host Corporations are constantly trying to balance these security issues, compliance requirements and the constant pressure of providing their services to their customers online. For example in the US, an investment of US $20 billion in federal funds is planned to achieve widespread deployment of electronic medical record (EMR) systems. This is being planned to reduce long- term costs and increase the effectiveness of health care business processes and, ultimately, to improve the US health care system. EMR systems will result in capturing and disseminating medical and health-related information for patients online, resulting in individuals being empowered to make health decisions for themselves, easily choose among providers, selectively disclose medical conditions and receive optimum care during emergencies.5 However, the security and privacy issues relating to providing patients information online include accidental or for profit disclosure or al information by insiders, the specific type of data at risk (patient identification, financials and medical information), and the scale at which data can be exposed (i.e., number of patient records threatened). For example, an unauthorized disclosure of medical records to the press for an individual with the HIV virus could lead to . Operating environment security, which involves securing the database and operating system . Application security, which involves securing and the actual application. This includes user access management and role-based access control This article addresses application security focusing on the RBAC model. It takes a look at some of the currently publicized security breaches and privacy violations and the risk involved and discusses how RBAC implementation minimizes such events and risks. Finally, it addresses the implementation of this model within the Oracle With a large user base using an system, administering user accounts can become a resource-intensive, time-consuming task and can lead to a system where segregation of duties conflicts prevail In addition, instances of security breaches and violations of privacy with regard to data kept by corporations are constantly in the news.2 Most publicized security breaches originate from unauthorized access of information systems from extemal sources, but a significant percentage of breaches come from the inside and these pose a serious threat to companies because they come from trusted users. For example, according to Privacy Rights Clearinghouse, a senior financial analyst at Countrywide downloaded sensitive social personal information (including Social Security numbers) of an estimated 2 million mortgage loan CONTI stating effects, such as family or community ostracism, job loss and denial of medical benefits. A large security breach could lead to HIPAA violations with severe consequences or penalties. ts over a period of two years. He told law enforcement that he profited anywhere from US $50,000 to US $70,000 from the sale of the WHY IMPLEMENT AN RBAC SECURITY MODEL? Management can minimize risk by introducing an RBAC model to administer and manage user access to the organization's information systems. Using a security platform based on an model simplifies user access administration and management, assists in maintaining a high level center stores.4 It only takes one mouse click to send sensitive data all over the world RBAC Security breaches and privacy issues can lead to a loss of reputation, customer trust and market SACA JOURNAL VOLUME 2,2010 1
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


